Method and device for researching and judging security alarm threats
A threatening and safe technology, applied in the field of network security, can solve the problem of insufficient utilization of historical intelligence data, and achieve the effect of comprehensive research and judgment results, accurate judgment results, and reasonable threat coefficient
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] figure 1 It shows a flow chart of a method for analyzing and judging security alarm threats provided by an embodiment of the present invention; figure 1 As shown, the technical solution of the method described in this embodiment comprises the following steps:
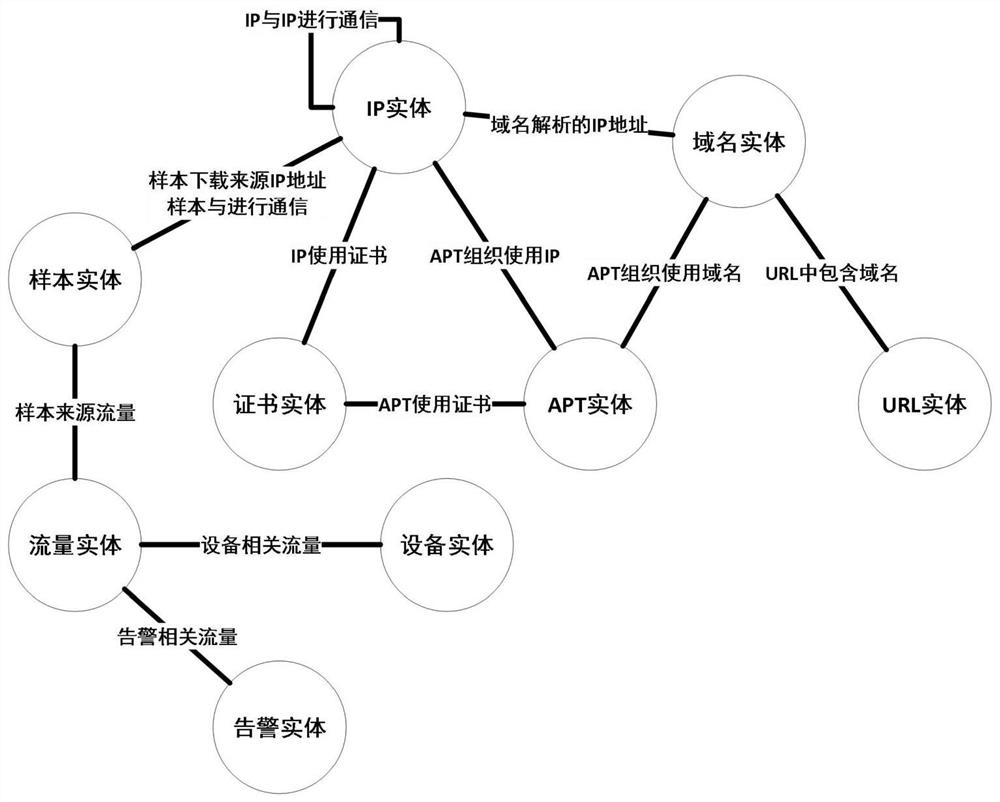
[0036] S1: Construct a network security intelligence knowledge map based on historical intelligence database data, classify intelligence data, identify its attributes, determine the explicit relationship between various types of data, and enter the generated threat entities and entity relationships into the knowledge map;
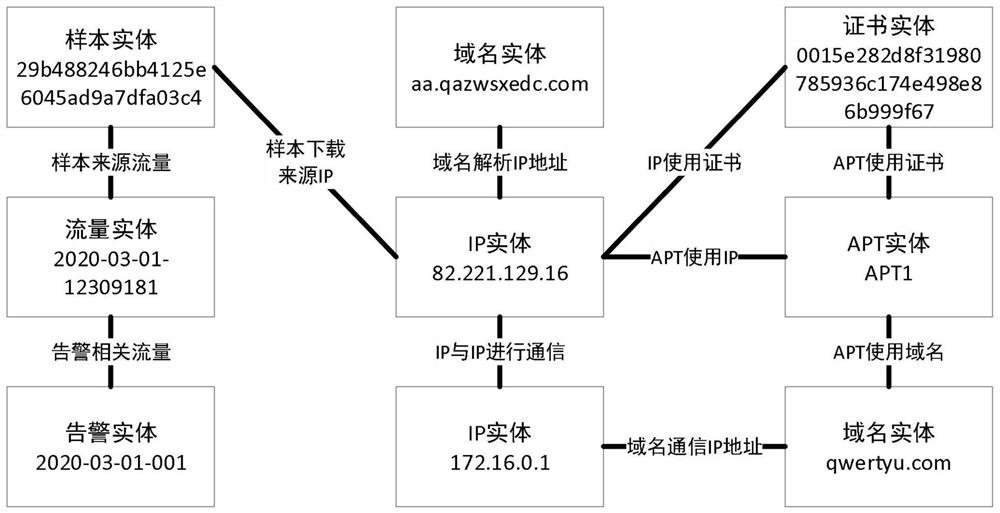
[0037] S2: Analyze the security alarm data to be studied and extract elements of each threat entity, perform association reasoning based on the network security intelligence knowledge map, and form a security alarm association subgraph of the security alarm data, which is used to describe the security alarm data The relationship between the elements of the threat entity;
[0038] figure 2 ...
Embodiment 2
[0076] Furthermore, as an implementation of the methods shown in the above embodiments, another embodiment of the present invention also provides a security alarm threat analysis and judgment device. This device embodiment corresponds to the foregoing method embodiment. For the convenience of reading, this device embodiment does not repeat the details in the foregoing method embodiment one by one, but it should be clear that the device in this embodiment can correspond to the foregoing method implementation. Everything in the example. In the device of this embodiment, there are following modules:
[0077] 1. Build a knowledge map module: configured to build a network security intelligence knowledge map based on historical intelligence database data; the technical solution implemented by this module corresponds to step 1 in Embodiment 1.
[0078] 2. Correlation subgraph module: configured to analyze the security warning data to be studied and judge and extract elements of each...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com