Power grid data security protection method and distributed power grid data security protection system
A data security and power grid technology, applied in the field of data security, can solve the problems of poor power grid system operation reliability, low labor or protection level, data security protection and audit dependence, etc., to achieve the effect of safe transmission and improved reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0018] A power grid data security protection method, which implements grid data configuration transformation based on information source coding, configures different data transmission channels and data storage grids for each type of grid data, and provides different data access channels and data storage grids for different data access channels and data storage grids. Different grid data access operation rules and data access nodes are configured in each grid. And configure the corresponding abnormal data filtering algorithm for the entrance of each data transmission channel, all the filtered abnormal data will be fed back to the corresponding power grid data audit node, and the analysis will be realized through the power grid data analysis audit model loaded in the grid data audit node Audit, all analysis and audit results will be fed back to the management cloud.
[0019] In this embodiment, different data access nodes are invoked according to the user's identification result...
Embodiment 2
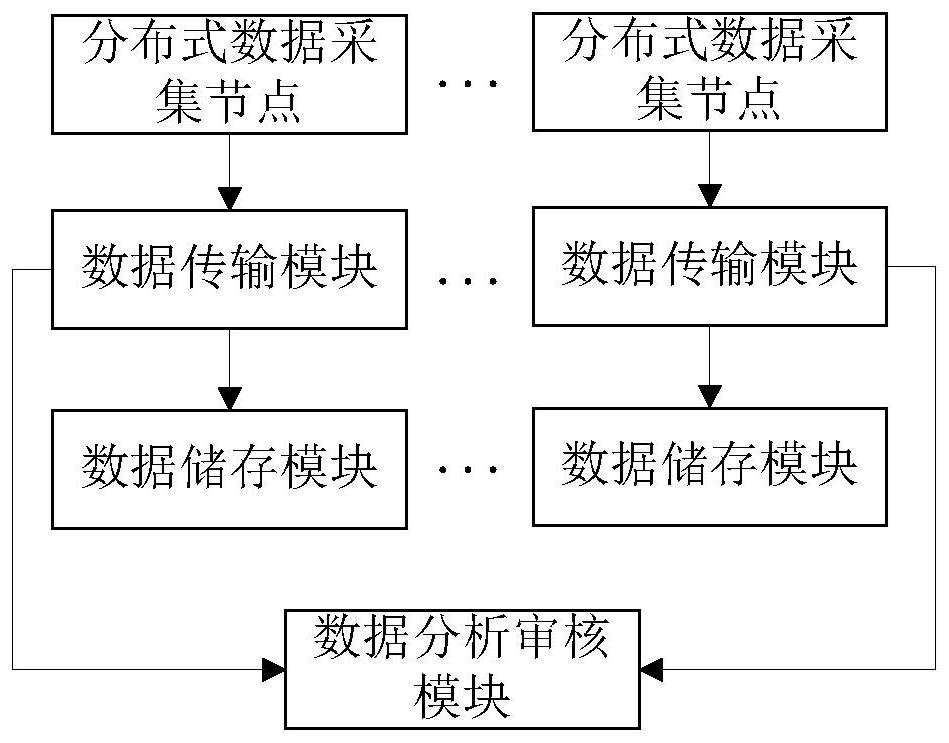
[0023] Such as figure 1 As shown, a distributed power grid data security protection system includes:
[0024] Distributed data acquisition nodes are used to collect different types of grid data respectively. In this embodiment, the categories can be configured according to the monitoring purpose of grid data;
[0025] The data transmission module is used to configure different data transmission channels for each type of grid data according to the type of grid data collected, so as to realize the filtering and transmission of grid data;
[0026] The data storage module is used to configure different data storage grids for each type of grid data according to the type of grid data collected, and configure different grid data access operation rules and data access for different data access channels and data storage grids Node, and the entrances of different data transmission channels are configured with corresponding abnormal data filtering algorithms;
[0027] The data analysis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com