A Workflow-Based Information Detection and Penetration Testing Method
A technology of penetration testing and workflow, applied in the field of workflow-based information detection and penetration testing, it can solve the problems of large-scale network segments and URL information detection and penetration testing difficulties, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The specific embodiments of the present invention will be described in further detail below with reference to the accompanying drawings and embodiments. The following examples are intended to illustrate the present invention, but not to limit the scope of the present invention.
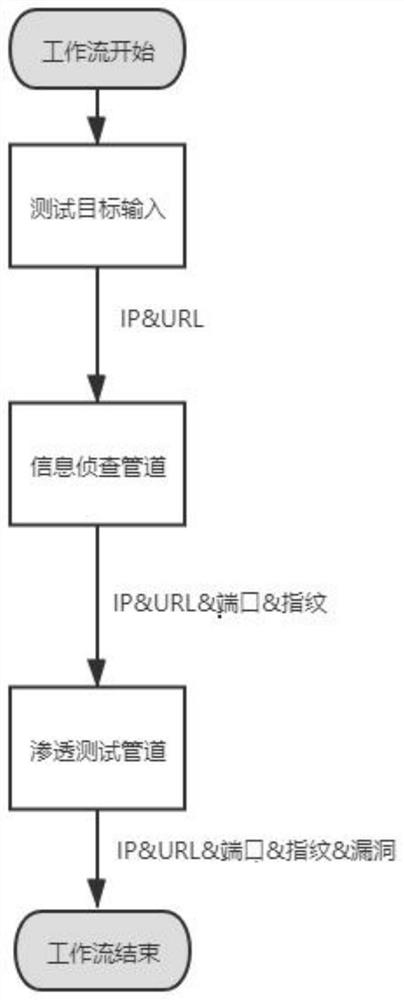
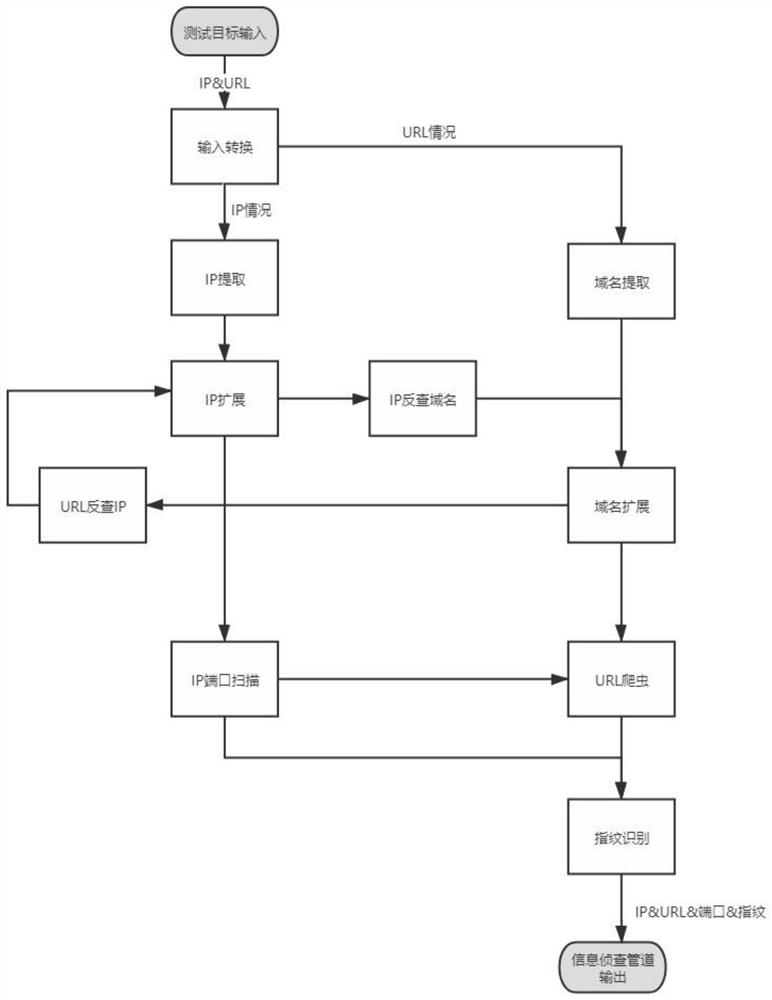
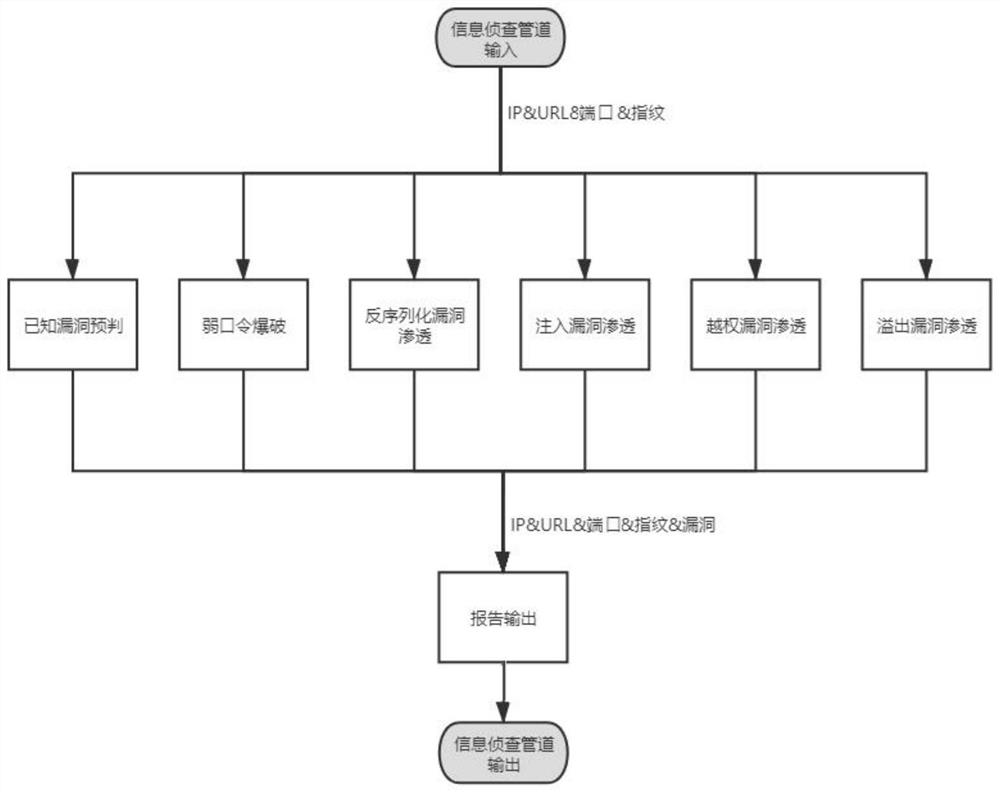
[0032] In this embodiment, a workflow-based information detection and penetration testing method is based on figure 1 The shown workflow implements detection, filtering, and deduplication of the domain name, IP, IP port, URL, and fingerprint of the test target, as well as known vulnerabilities, weak password vulnerabilities, deserialization vulnerabilities, injection vulnerabilities, unauthorized vulnerabilities, and overflow vulnerabilities. Conduct information reconnaissance and penetration testing.
[0033] The workflow includes a test target input, an information investigation pipeline and a penetration test pipeline; the test target input is used to input assets of the test target, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com