Malicious behavior identification method for industrial control honey pot
An identification method and malicious technology, applied in the field of network security, can solve problems such as the inability to effectively identify malicious behavior of industrial protocols, and achieve the effect of improving the accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
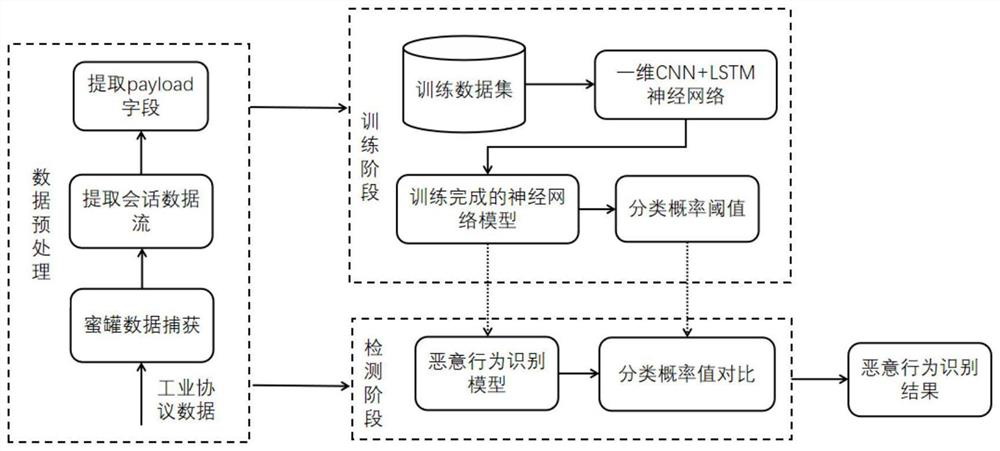
[0030] The technical solution of the present invention is tested in combination with specific data.
[0031] Firstly, the data to be tested is input into the built neural network model, the model will give its classification probability vector and quasi-classification result, compare the vector with the category threshold, if it is less than the threshold, then output the neural network classification result, if If it is greater than the threshold, the sample is identified as an unknown category.
[0032] The method of the present invention is used to classify and identify the malicious traffic captured by the honeypot. The sample contains five types of malicious behaviors, including common detection attacks, FUZZ attacks, malicious response injection, malicious state command injection, and malicious function code injection. The experimental results are shown in Table 1. Experimental results show that the method adopted in the present invention can significantly improve the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com