Application program security test method and related device
An application program and security testing technology, applied in computer security devices, software testing/debugging, error detection/correction, etc., can solve problems such as error-prone and inaccurate application program security testing methods, and reduce the dependence on request response Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Embodiments of the present application are described below in conjunction with the accompanying drawings.
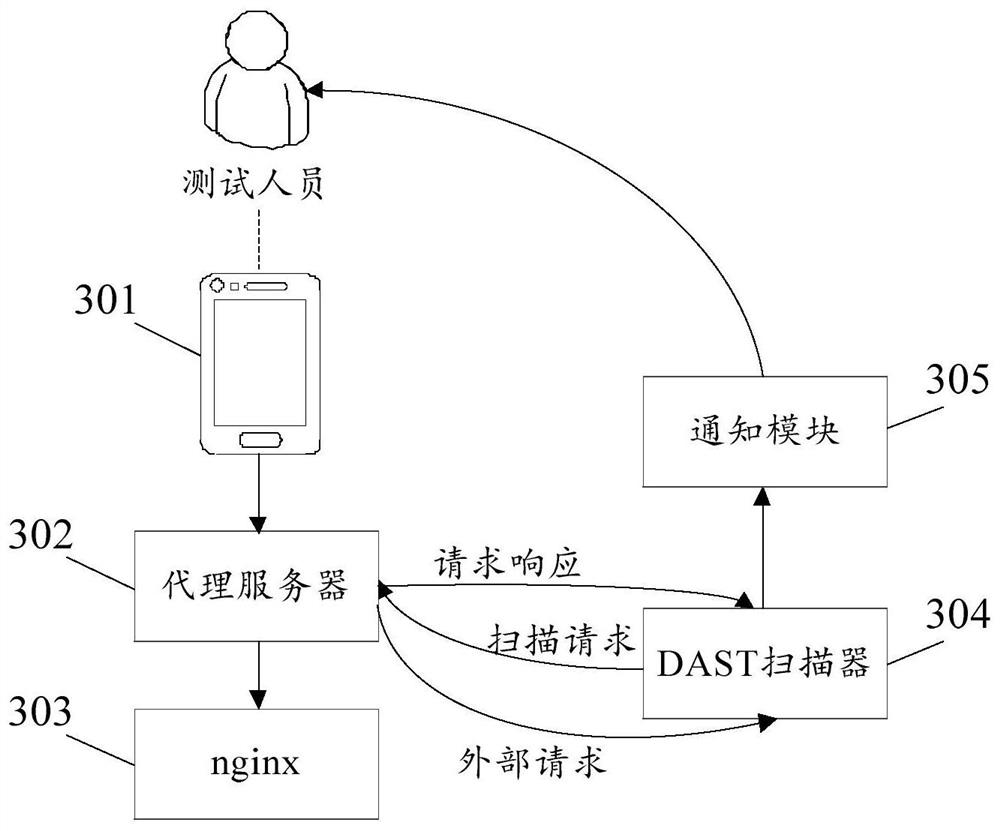
[0030] In related technologies, application A is deployed under a server that provides network services to build a security testing environment for application A; all external requests received by application A are collected and forwarded to the DAST scanner, which generates scanning requests. The scanning request is used to scan the application A, and the application A responds to the scanning request, and returns the request response to the DAST scanner. The DAST scanner judges whether there is a vulnerability in the application A according to the request response, and realizes the security test of the application A.
[0031] However, the above-mentioned application A security testing method relies heavily on the request response obtained by the application A responding to the scanning request. In the case of network delays, algorithm defects, etc., it is easy to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com