A Named Entity Recognition Method and Device Based on Composable Weak Authenticator
A named entity recognition and entity recognition technology, applied in neural learning methods, instruments, biological neural network models, etc., can solve problems such as large differences in entity boundaries, failure, and strong subjective consciousness, so as to enrich training samples and increase robustness. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
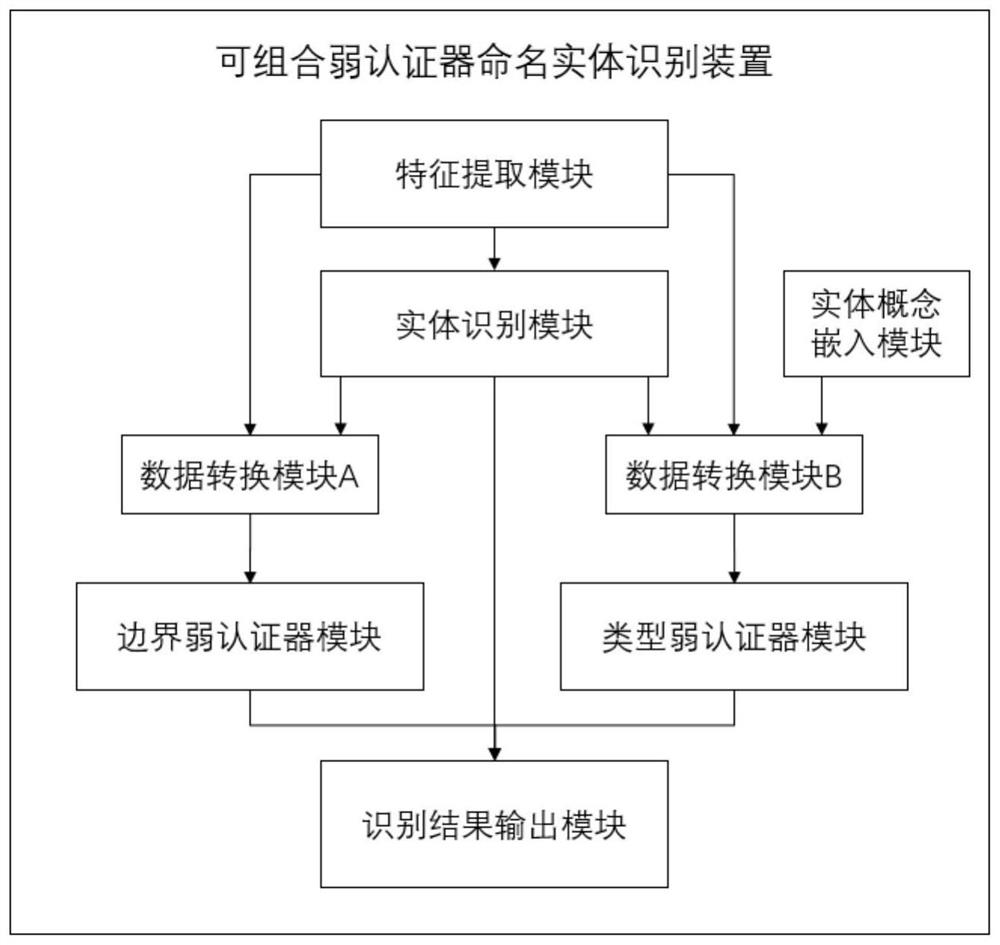
[0128] An algorithm framework for named entity recognition based on a composable weak authenticator, including: an entity recognition part and a result authentication part;
[0129] The entity recognition part is used to complete the recognition task and obtain the recognition result;
[0130] The result authentication part includes two or more weak authenticators, which are respectively used to verify and authenticate the recognition results on the subdivision targets corresponding to each weak authenticator.
[0131] The algorithm architecture also includes an information input layer to be identified, an entity identification layer, a data conversion layer and a weak authenticator output layer;
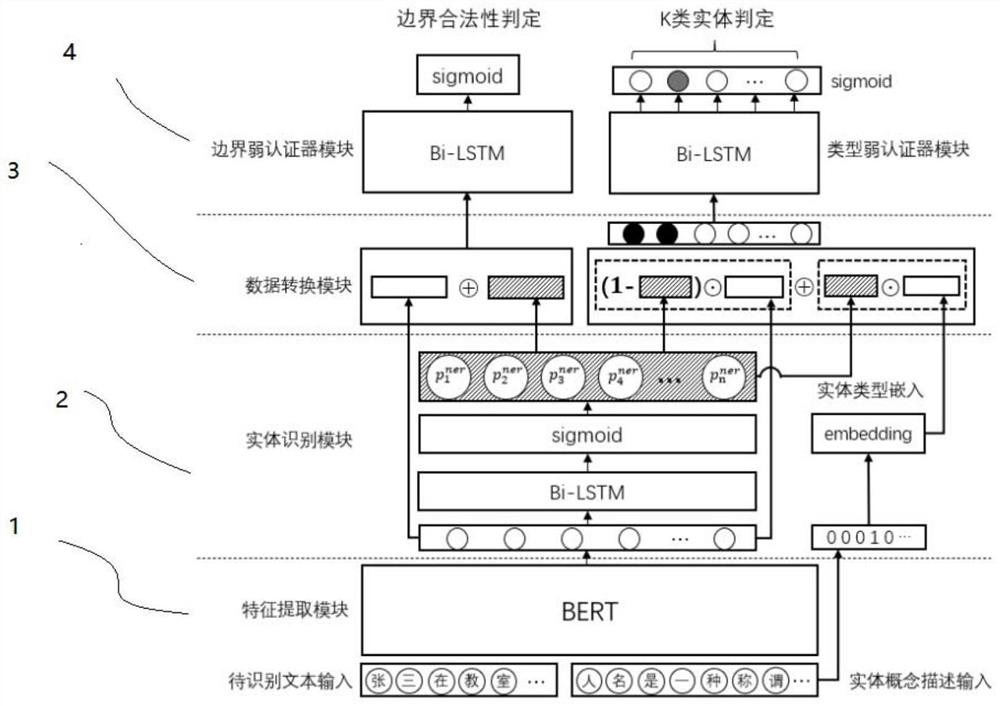
[0132] The information input layer to be identified performs feature extraction: this layer includes a feature extraction module; the text input to be identified and the entity description input are processed by the feature extraction module as the first input information of the ent...
Embodiment 2
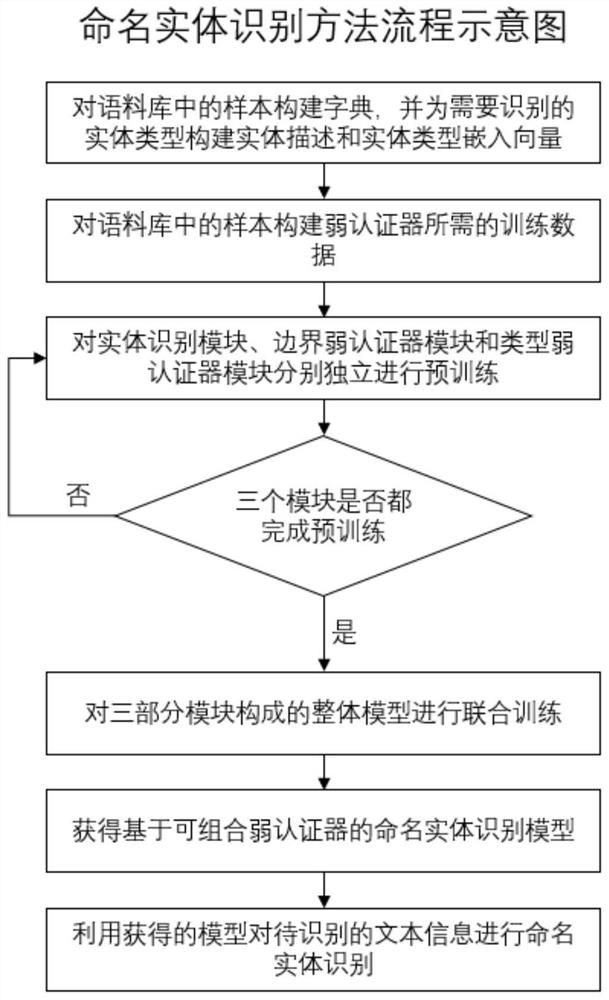
[0145] According to the algorithm architecture of named entity recognition based on combinable weak authenticators described in Embodiment 1, the architecture also includes a training information flow, and the training information flow specifically includes: a pre-training information flow and a joint training information flow;
[0146] Among them, the pre-training information flow includes the entity recognition module pre-training information flow, the boundary weak authenticator pre-training information flow and the type weak authenticator pre-training information flow;
[0147] Pre-training information flow of the entity recognition module: the feature extraction module in the input layer of the information to be recognized and the entity recognition module in the entity recognition layer participate in the training, and the weak authenticator layer closes the input and output interfaces; the training data is the original training marked corpus;
[0148] Boundary weak authe...
Embodiment 3
[0152] As described in Embodiment 1, based on the algorithm architecture of the named entity recognition of the combinable weak authenticator, the entity recognition module includes multiple sets of neural network series and activation functions of the neural network. Preferably, each set of neural networks can have an extraction sequence The network structure of feature capabilities, such as Bi-LSTM neural network (Bidirectional Long Short-Term Memory, Bidirectional Long Short-Term Memory), Bi-GRU neural network (Bidirectional Gate Recurrent Unit, bidirectional gated recurrent unit) or deep convolutional neural network, etc.
[0153] Preferably, the feature extraction module is loaded with a pre-trained language model based on the self-attention mechanism; preferably, the BERT algorithm is loaded.
[0154] A neural network (such as Bi-LSTM neural network, Bi-GRU neural network or deep convolutional neural network, etc.) and a neural network activation function (such as sigmoid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com