Network intrusion cooperative detection method based on security cloud
An intrusion detection and network intrusion technology, applied in the field of network security, can solve the problems of network intrusion detection not running normally, computer security monitoring, and abnormal lower-level detection nodes, etc., to prevent malicious interception of files, strong security performance, and strong timeliness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
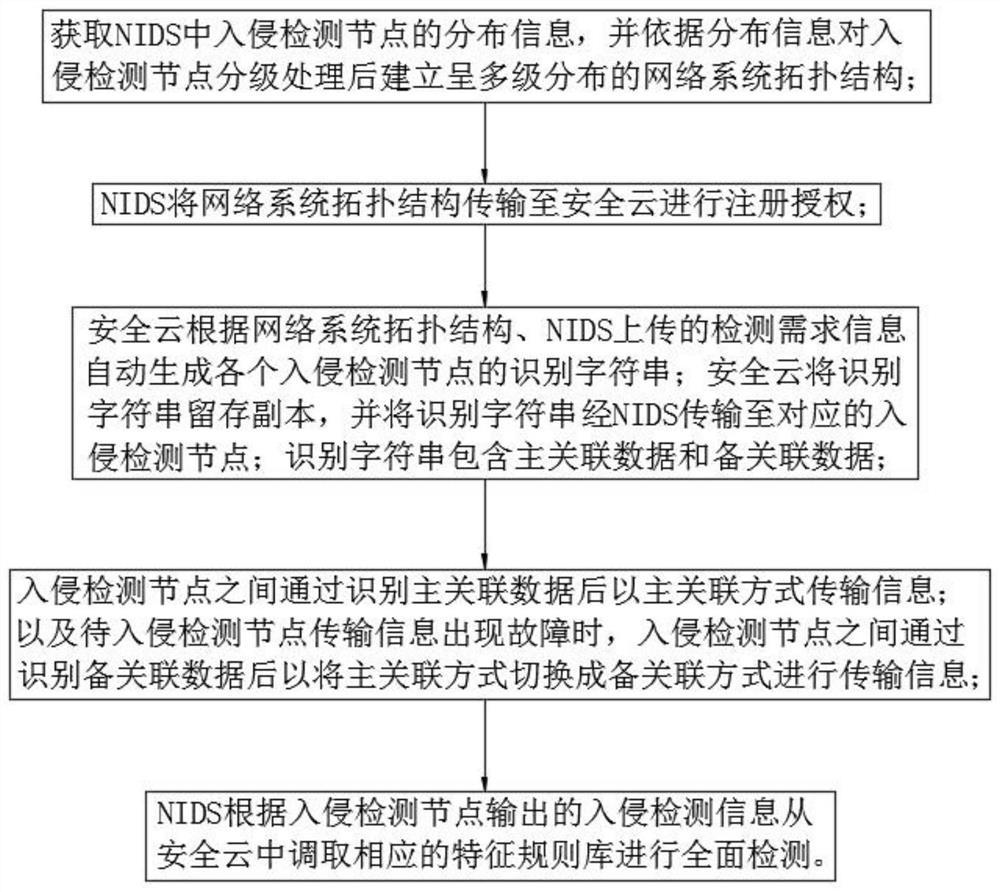
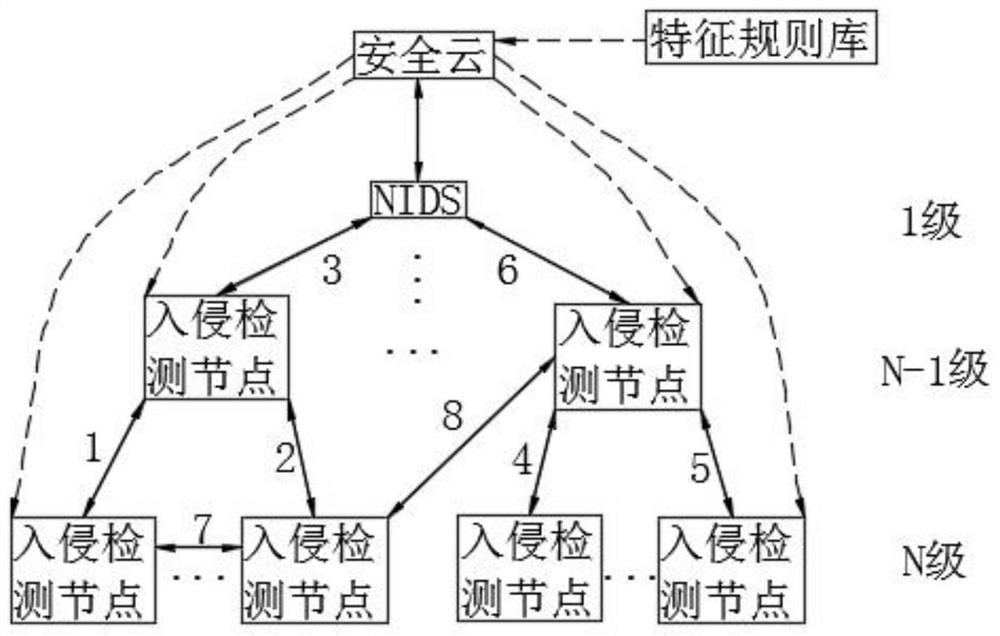
[0038] Embodiment: a network intrusion collaborative detection method based on security cloud, such as figure 1 and figure 2 As shown, it is specifically implemented by the following steps.
[0039] Step 1: Obtain the distribution information of intrusion detection nodes in NIDS, and establish a multi-level distribution network system topology after classifying the intrusion detection nodes according to the distribution information. Such as figure 2 As shown, the network system topology includes management nodes and basic nodes; each management node corresponds to at least one basic node, and the basic nodes subordinate to the same management node are in the same operator network area. Among them, there is no bottom-level basic node at level N, level 1 is the management center of NIDS, and level N-1 is the management node.
[0040] Step 2: NIDS transmits the topology of the network system to the security cloud for registration and authorization. Intrusion detection nodes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com