Reusable VPN architecture and VPN scheduling method
A scheduling method and scheduling unit technology, applied in the communication field, can solve problems such as low reuse rate, flat business logic, and poor maintainability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
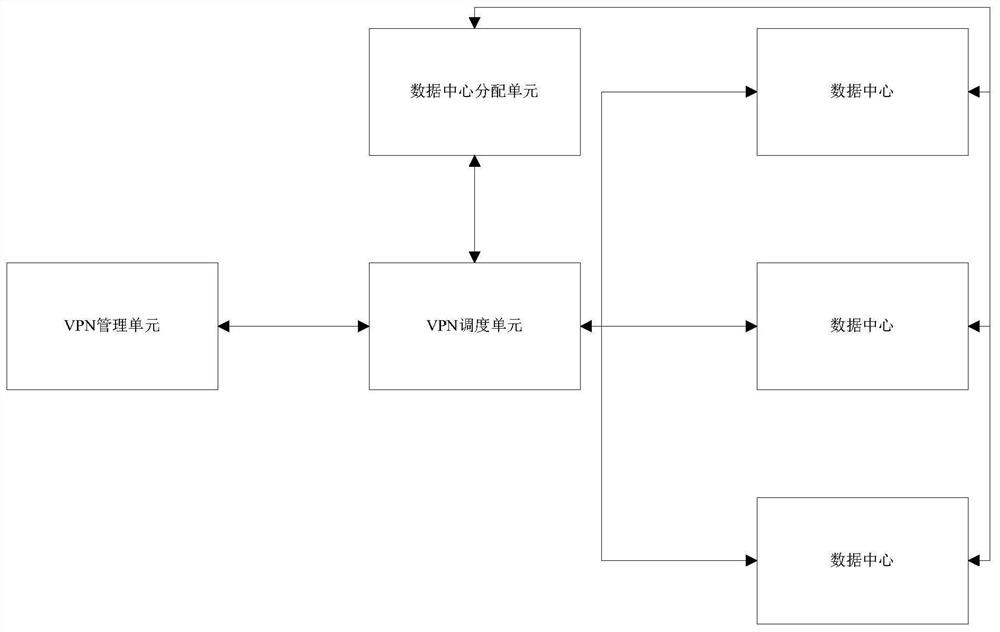
[0039] refer to figure 1 , a reusable VPN architecture, including a VPN management unit, a VPN scheduling unit, and one or more data centers;
[0040] VPN management unit: used to create and manage at least one type of VPN group according to user requests, each VPN group includes several VPN services, each VPN service is composed of several VPN instances, and each VPN service has a corresponding VPN specification;
[0041] VPN scheduling unit: used to obtain VPN specifications from the VPN management unit, send the VPN specifications to the data center, receive information on the operation resources allocated for the VPN group fed back by the data center, and establish each VPN in the VPN group according to the information on the operation resources. The configuration information of the instance is sent to the data center;
[0042] Data center: used to allocate operating resources for the VPN group according to the VPN specification, and run the VPN instance according to the ...
Embodiment approach
[0044]The VPN architecture includes: a VPN management unit, a VPN scheduling unit, and multiple data centers.
[0045] The VPN management unit and VPN scheduling unit can be set on the same or multiple local physical machines, or on a cloud server.
[0046] VPN management unit: used to create and manage at least one type of VPN group according to user requests, each VPN group includes several VPN services, each VPN service is composed of several VPN instances, and each VPN service has a corresponding VPN specification;
[0047] VPN specifications can be understood as user demands for VPN services. For example, the VPN specification is:
[0048] {protocol type: tcp, ping interval: 60, retry times: 3, encryption algorithm: AES_256}
[0049] Indicates that it is necessary to build a VPN service that uses the tcp transmission protocol between the client and the server, with a PING interval of 60 seconds, 3 failed retries, and an encryption algorithm of AES_256. The VPN specific...
Embodiment 2
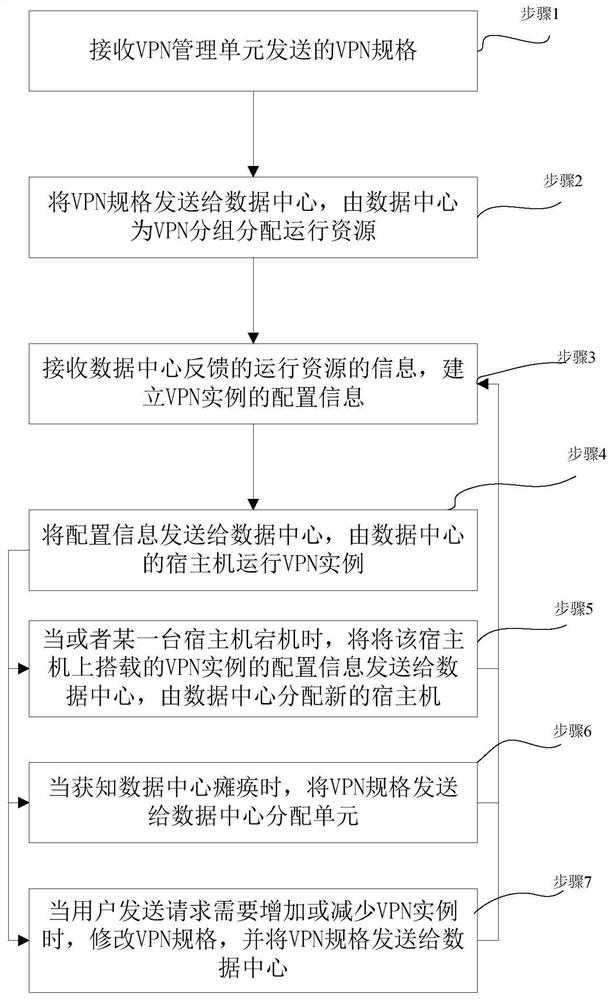
[0084] refer to figure 2 , a VPN scheduling method based on the VPN architecture as described in Embodiment 1, comprising the steps of:
[0085] Step 1: receiving the VPN specification sent by the VPN management unit;
[0086] Step 2: Send VPN specifications to the data center, and the data center allocates operating resources for VPN groups;
[0087] Specifically, the VPN specification is sent to the data center through the data center allocation unit, and the data data center allocation unit is used to receive the VPN specification sent by the VPN scheduling unit, select a suitable data center, and send the VPN specification to the data center. center;
[0088] Step 3: Receive the running resource information fed back by the data center, and establish the configuration information of the VPN instance;
[0089] Step 4: Send the configuration information to the data center, and the host computer in the data center runs the VPN instance.
[0090] Step 5: When or when a cer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com