Method and system for business connection between cloud management platform and cloud security management platform
A security management platform and security business technology, applied in the field of business connection between the cloud management platform and the cloud security management platform, can solve the problems that the cloud business management ability does not play any role, the process cannot be managed in a unified way, and no effective solution has been proposed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
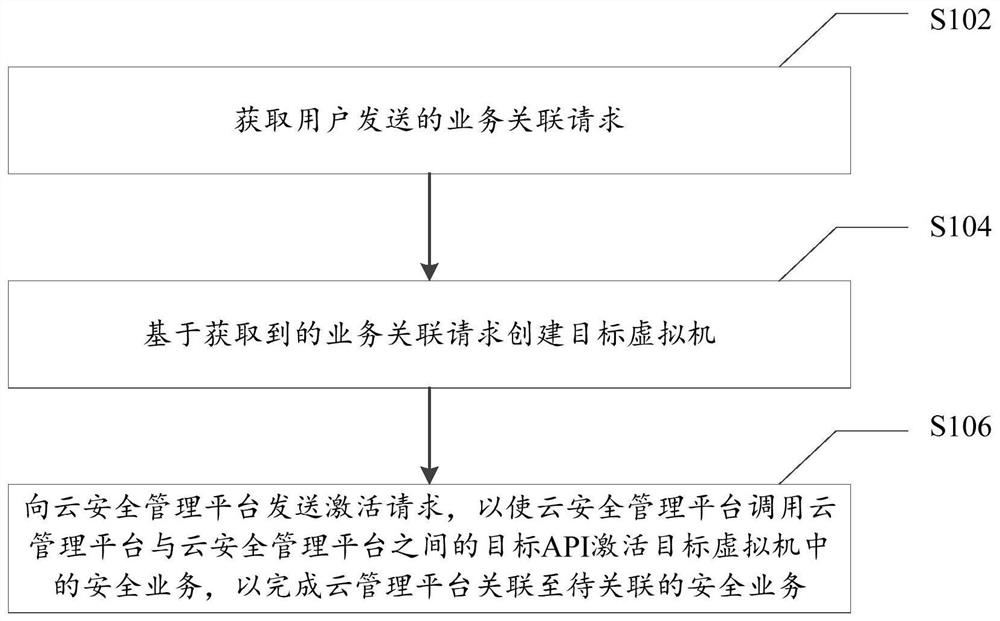
[0026] figure 1 It is a flowchart of a method for business connection between a cloud management platform and a cloud security management platform provided according to an embodiment of the present invention, and is applied to the cloud management platform, wherein the cloud management platform and the cloud security management platform are connected through an application program interface API. like figure 1 As shown, the method specifically includes the following steps:
[0027] Step S102: Obtain a service association request sent by the user, wherein the service association request carries the security service to be associated, and the security service to be associated is a virtual security service belonging to the cloud security management platform.
[0028] Step S104: Create a target virtual machine based on the acquired service association request, where the target virtual machine includes an image file of the security service to be associated.
[0029] Specifically, t...
Embodiment 2
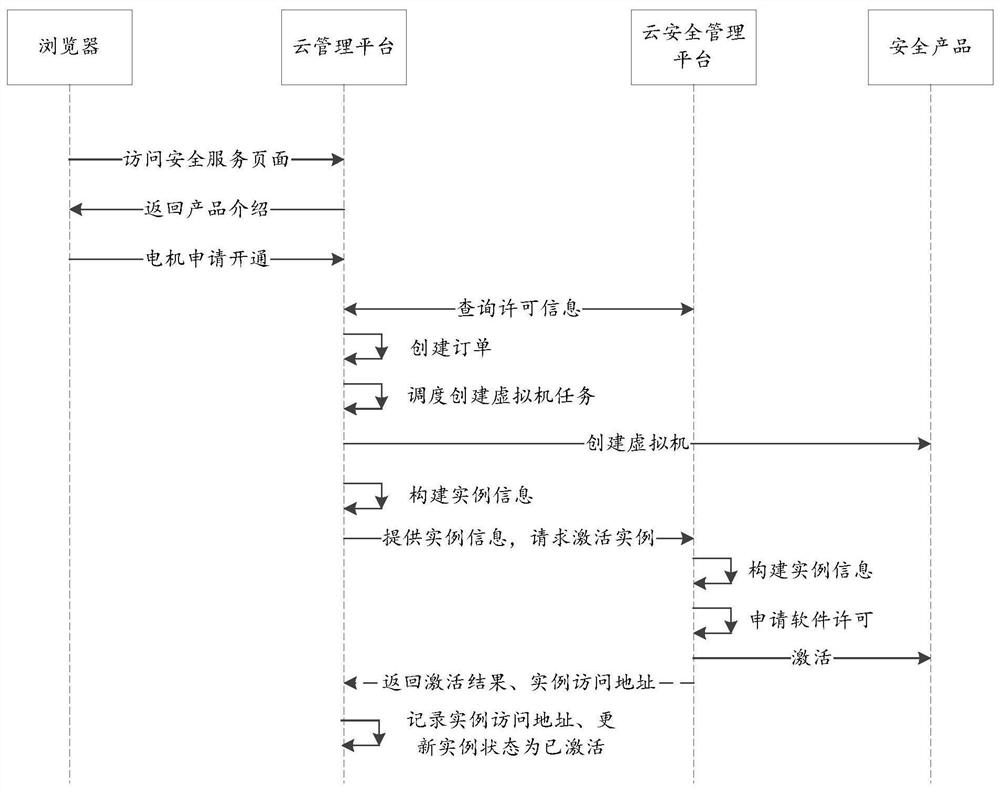
[0063] Figure 4 It is a schematic diagram of a system for business docking between a cloud management platform and a cloud security management platform according to an embodiment of the present invention. The system is applied to a cloud management platform, wherein the cloud management platform and the cloud security management platform are connected through an application program interface API. Specifically, as Figure 4 As shown, the system includes: an acquisition module 10 , a creation module 20 and an activation module 30 .
[0064] Specifically, the obtaining module 10 is configured to obtain the service association request sent by the user, wherein the service association request carries the security service to be associated, and the security service to be associated is the virtual security service belonging to the cloud security management platform.
[0065] The creating module 20 is configured to create a target virtual machine based on the acquired service associa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com