Apt attack scene recovery detection method and system based on multi-source log correlation analysis
A technology of correlation analysis and attack scenarios, applied in the field of network security, can solve problems such as poor APT attack effect, and achieve the effect of simple construction and strong applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
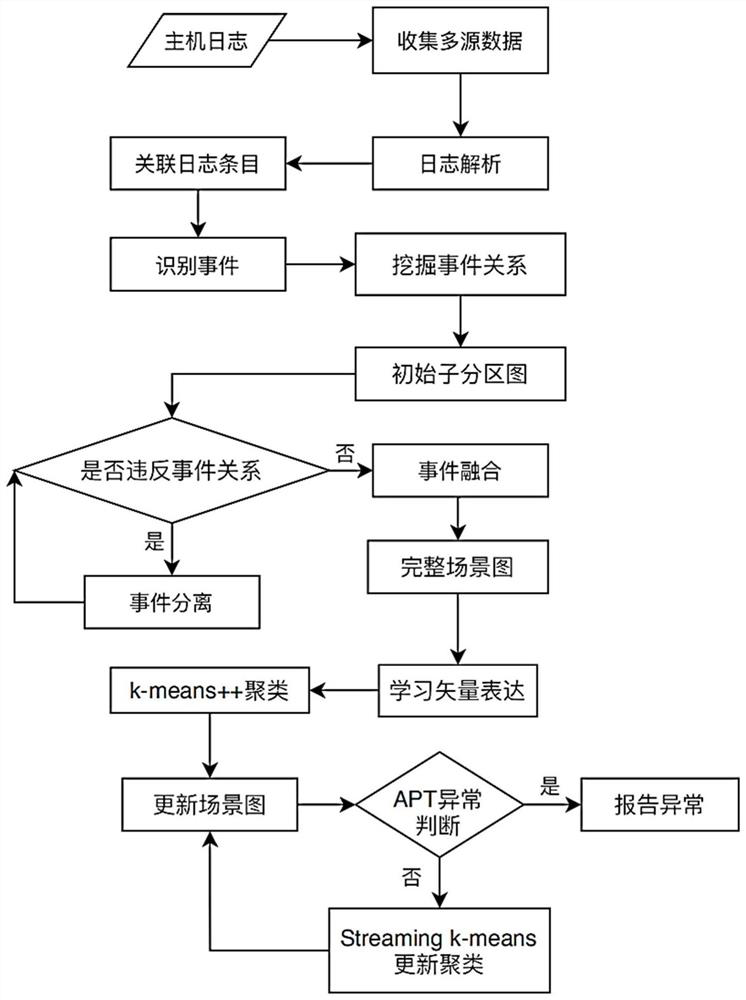
[0055] The APT attack scene recovery detection method based on multi-source log association analysis of the present invention is mainly composed of three stages: identifying events in the system, constructing a scene graph, and detecting APT attacks. see figure 1 , the specific implementation method is as follows:
[0056] Step 1, identify events in the system;
[0057] (1a) Collect firewall logs, network traffic records and process logs, analyze the logs, unify the format of log entries, and use 24-dimensional relationship vectors Correlate all log entries, capturing the relationships within and between logs:
[0058] Specifically, first collect logs from different sources (firewall logs, network traffic records, and process logs), analyze the logs, adjust parameters, delete redundancy, and unify the format. The present invention retains...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com