Black hole attack defense method in route discovery
A black hole attack and routing technology, applied in the field of black hole attack defense, can solve the problems of low practical applicability and difficulties of trusted third parties, and achieve good adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
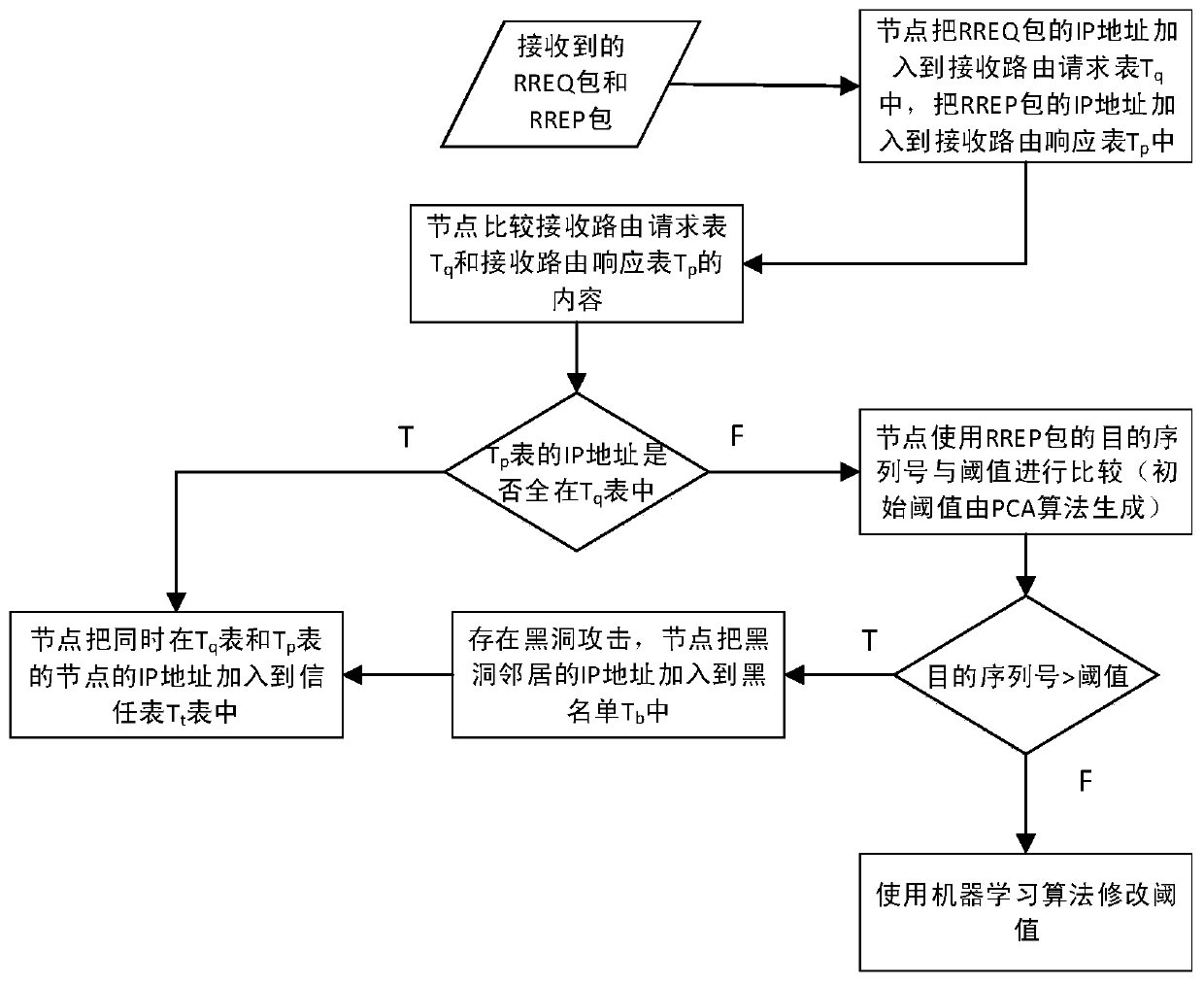
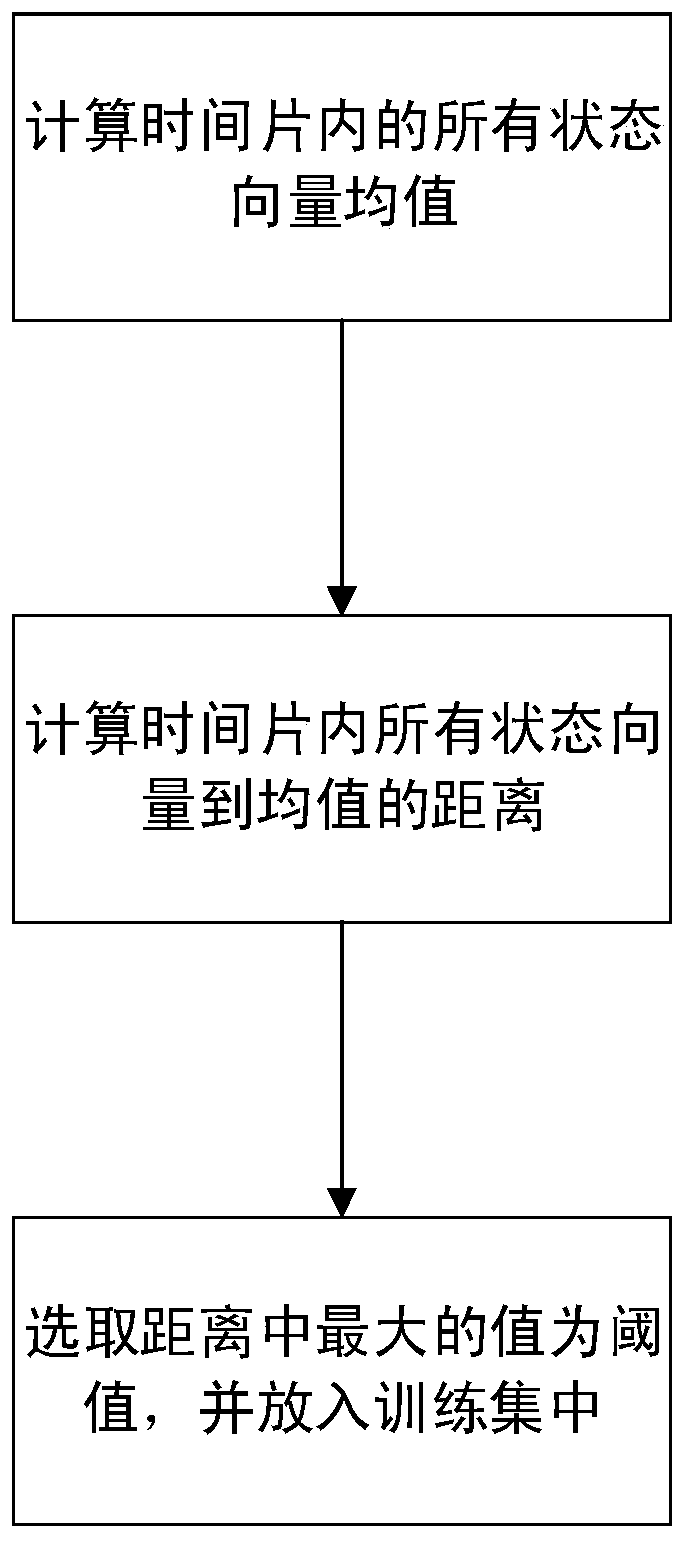
[0040] The present invention uses a received routing request table T based on q and receive route response table T p The method of comparison obtains the set of suspicious nodes, and then uses the machine learning algorithm to obtain the destination sequence number threshold of the route response packet, and then the source node uses the received destination sequence number of the route response packet to compare with the threshold to determine whether a black hole attack occurs, and use it again. The comparison of the above two tables obtains the black hole node.
[0041] The present invention receives the routing request table T q , receive routing response table T p The knowledge of set theory and engineering optimization is applied in the steps of comparison and the step of applying machine learning algorithm to dynamically calculate the serial number threshold. The symbols used are shown in Table 1.
[0042]
[0043]
[0044] Note: 0
[0045] The present inv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com