Virtualization escape defense method based on kernel debugger
A virtualization and debugger technology, applied in the field of virtualization security, can solve problems such as threats to host security, and achieve the effect of quick analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Embodiments of the present invention will be disclosed in the following diagrams. For the sake of clarity, many practical details will be described together in the following description. It should be understood, however, that these practical details should not be used to limit the invention. That is, in some embodiments of the invention, these practical details are not necessary.
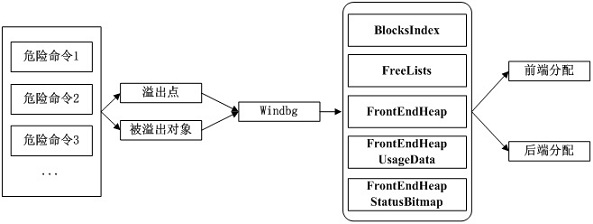
[0035] The present invention is a virtualization escape defense method based on the Windbg debugger. First, the virtual machine process is attached to the Windbg in the host, and the captured RPCI commands are integrated, and the data packet analysis module performs analysis to screen out suspicious commands. Then judge the parameters, calling functions, data block length, etc., analyze the overflow point and the location of the overflowed object, and judge its allocation method at the same time, and finally combine the key data structure and specific allocation method to carry out precise he...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com