System and method of detecting malicious files based on file fragments
A malicious file and file technology, applied in transmission systems, electrical components, instruments, etc., can solve problems such as hindering malware analysis, and achieve the effect of improving computer security and realizing information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
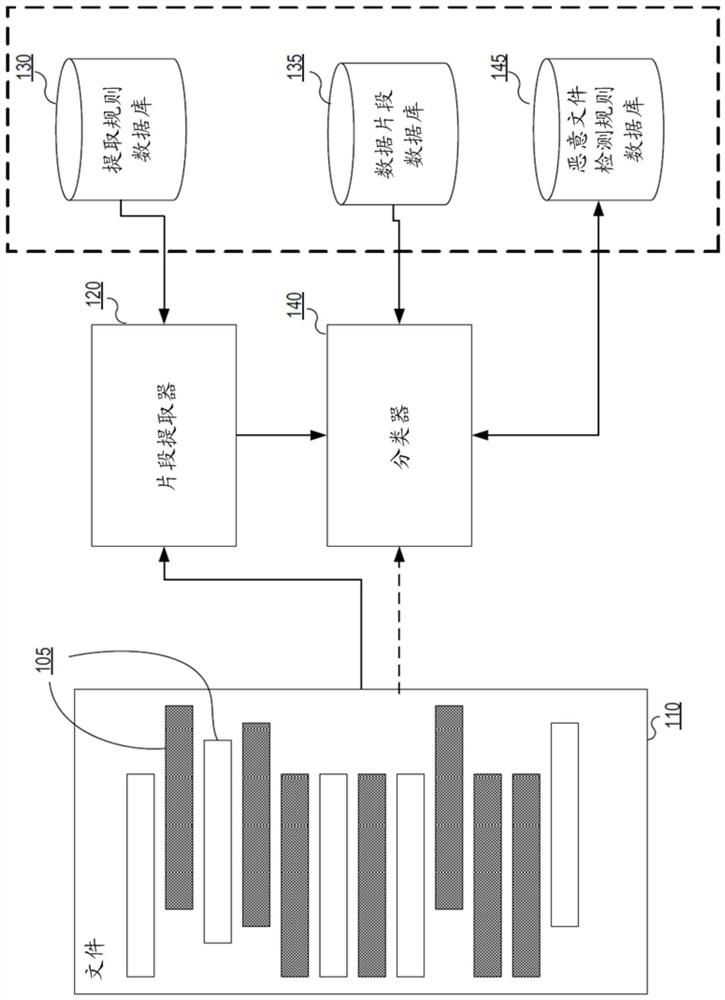
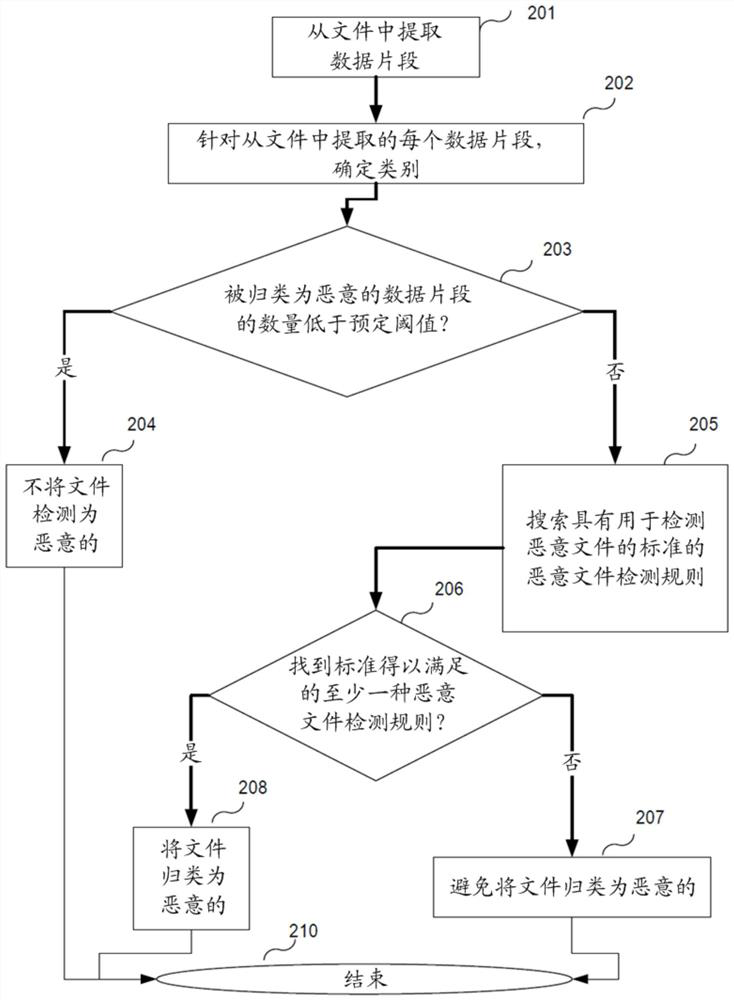
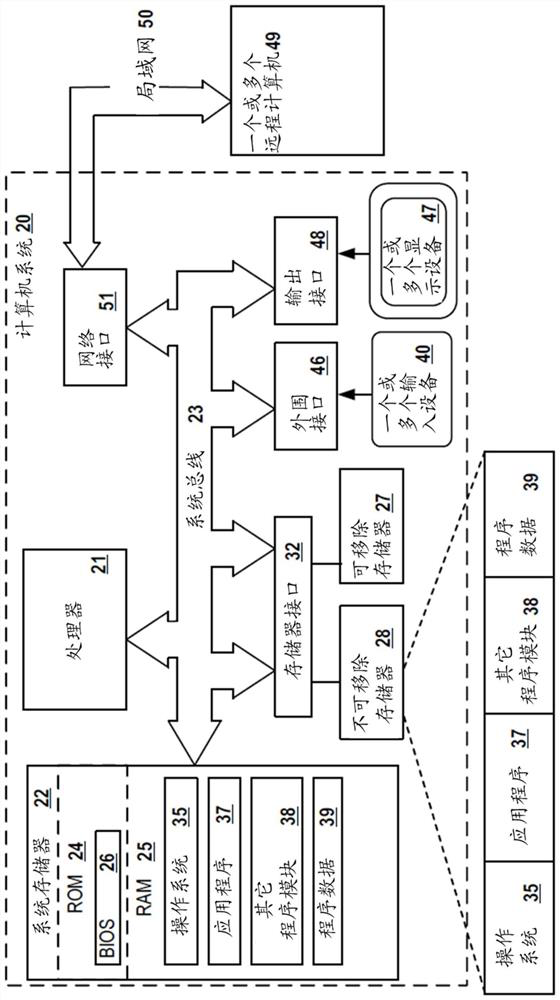
[0021] Exemplary aspects are described herein in the context of systems, methods, and computer programs for detecting malicious files based on file fragments. Those of ordinary skill in the art will appreciate that the following description is illustrative only and is not intended to be limiting in any way. Other aspects will readily suggest themselves to those skilled in the art with the benefit of the invention. Reference will now be made in detail to implementations of the exemplary aspects as illustrated in the accompanying drawings. Wherever possible, the same reference numbers will be used throughout the drawings and the following description to refer to the same or like items.
[0022] In order to clearly present the teachings of the invention, a number of terms and concepts are defined herein as used to describe various aspects of the invention.
[0023] A malicious application is an application capable of causing damage to a computing system or to the data of a user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com