Method and device for identifying network encrypted traffic
A flow recognition and network technology, applied in character and pattern recognition, biological neural network models, instruments, etc., can solve the problems of high time-consuming and poor real-time performance of flow recognition algorithms, and achieve automatic learning, solve classification problems and data inconsistencies The effect of balance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0089] The present invention provides a network encryption traffic identification method, which is characterized in that it includes the following processes:
[0090] Obtain the encrypted traffic file to be identified;
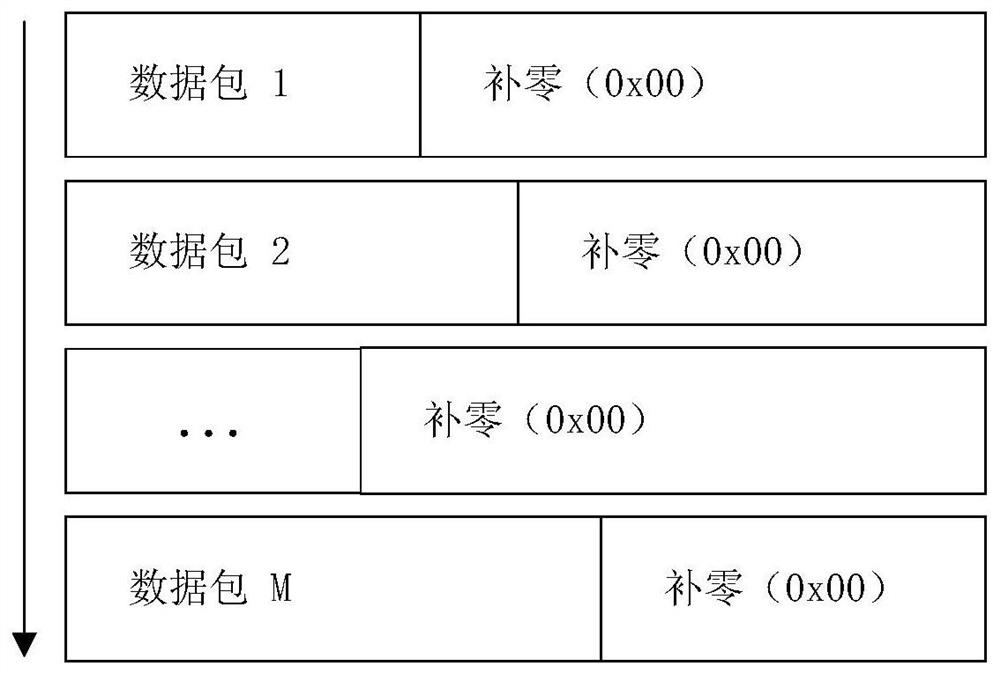
[0091] The encrypted traffic to be identified is preprocessed, and the preprocessing includes: dividing the encrypted traffic flow into multiple flows; then collecting multiple continuous data packets from each flow as samples; finally performing vectorization, Standardize to obtain a formatted sample vector set;
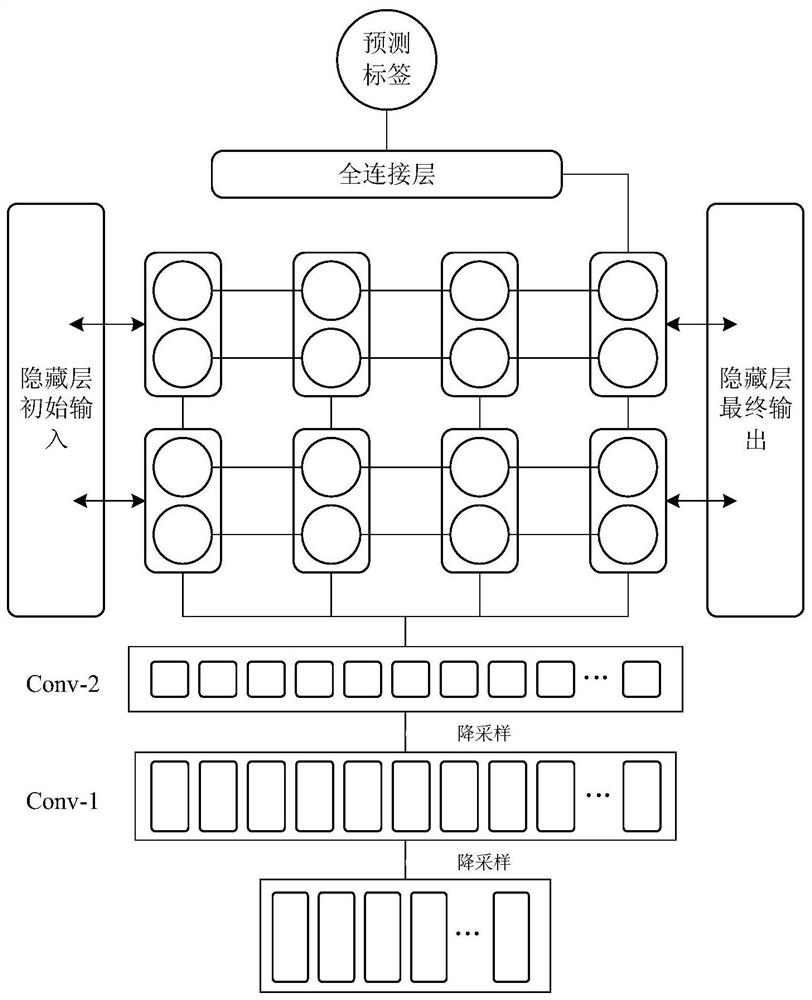
[0092] Inputting the sample vector set obtained after preprocessing into the pre-trained hybrid neural network model to obtain a prediction vector, where the element values in this prediction vector represent the predicted values of encrypted traffic belonging to each category;
[0093]The hybrid neural network model includes: a 1D-CNN network, a stacked bidirectional LSTM network, and a fully connected layer network; the 1D-CNN network perform...
Embodiment 2
[0097] The extraction of features used to identify encrypted traffic is related to traffic preprocessing methods, vectorization methods, and information on different parts of the traffic data stream. For example, the meta-information and payload information of the traffic, which can provide different and effective characteristics for the identification of encrypted traffic. In this solution, on the one hand, consider using information such as flow meta information, partial payload of data packets, and timing characteristics between data packets to improve data integrity. On the other hand, a hybrid neural network model is designed in this method for automatic representation learning of the above information.
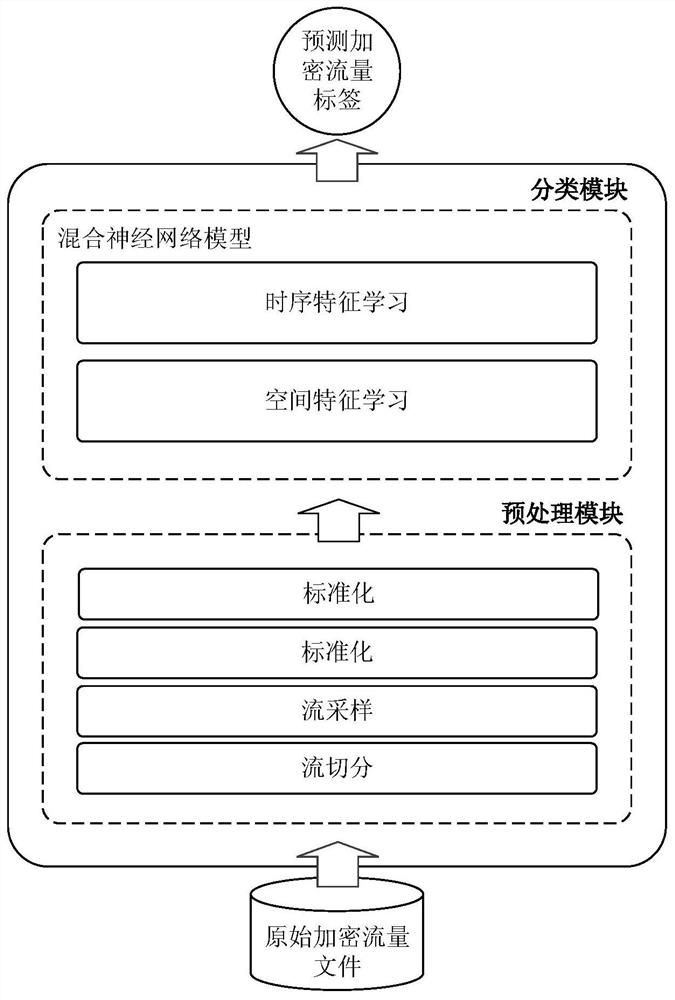
[0098] figure 1 This is the overall frame diagram of the method of the present invention, which mainly includes two stages: a preprocessing stage and a classification stage. The preprocessing stage directly converts the original traffic into standard data, which includ...
Embodiment 3
[0181] Correspondingly, the present invention also provides a network encrypted traffic identification device, including an encrypted traffic acquisition module, a preprocessing module, a classification prediction module and a classification identification module; wherein:
[0182] The encrypted traffic acquisition module is used to acquire the encrypted traffic file to be identified;
[0183] A preprocessing module, used for preprocessing the encrypted traffic to be identified, the preprocessing module includes a stream segmentation unit, a collection unit and a vectorization unit, wherein:
[0184] The stream splitting unit is used to split the encrypted traffic stream into multiple streams;
[0185] a collection unit for collecting a plurality of consecutive data packets as samples from each flow;
[0186] The vectorization unit is used to vectorize and standardize each sample to obtain a formatted sample vector set;
[0187] The classification prediction module is used t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com