Multi-authority encryption method and system
A technology of authorization and encryption method, applied in the field of encryption, can solve the problems of high communication cost, inappropriate cloud storage system, lack of scalable features, etc., to improve integrity and security, solve collusion attacks, and improve security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0078] Please refer to figure 1 , Embodiment 1 of the present invention is:
[0079] A multi-authority encryption method, specifically comprising:
[0080] S1. The attribute authority generates the master private key and system public parameters according to the preset algorithm, and the attribute authority (AA) has multiple and is independent of each other;
[0081] Specifically:
[0082] Receive the system security parameter λ, and generate the multiplicative cyclic group G and G of the prime number p whose group order is λ bits T , the length of the prime number p is λ bits, and generates the bilinear group e:G×G→G T , g is a generator of the multiplicative cyclic group G;
[0083] Each attribute authority randomly selects the first random value w and the second random value a k , a k ∈ Z p * Calculate the first indicated value and the second indicated value where k represents the kth attribute authority, Z p * ={1,2,...,p-1};
[0084] selecting a fourth indi...
Embodiment 2
[0117] A multi-authority organization encryption method, which differs from Embodiment 1 in that:
[0118] Also include before the step S5:
[0119] The data holder outputs ciphertext according to the system public parameters, plaintext and access policy set;
[0120] Specifically:
[0121] Select the plaintext m to be encrypted, the access policy set W={W 1 ,W 2 ,...,W n} and a random positive integer s;
[0122] Calculate the ciphertext header C of the ciphertext 0 =g s , ciphertext
[0123] Set the initial value of the root node ε of the access tree to s∈Z N / 0, and mark the number of child nodes ζ;
[0124] Judging the identification relationship between the root node and the child nodes, if it is an "or" operation, setting all the child nodes corresponding to the root node to s;
[0125] If it is an "AND" operation, an integer s is randomly selected i As the value of the i-th child node corresponding to the root node, and the values of all the child nodes c...
Embodiment 3
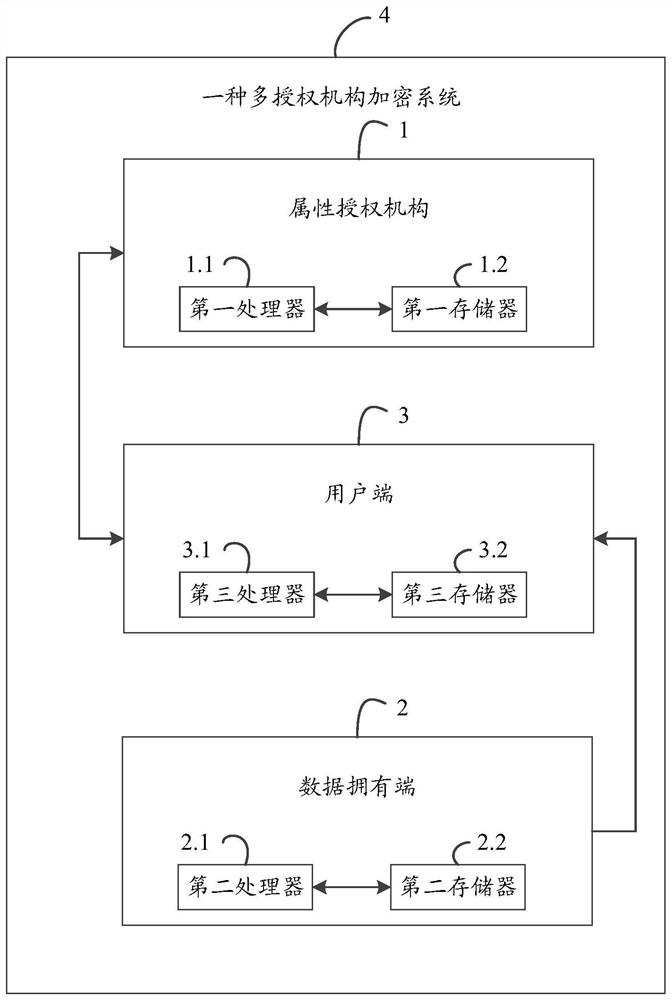
[0137] Please refer to figure 2 , Embodiment three of the present invention is:
[0138] A multi-authority encryption system, including an attribute authority 4, a data owner 2, and a user terminal 3, the attribute authority 1 includes a first memory 1.2, a first processor 1.1 and stored on the first memory 1.2 The first computer program that can run on the first processor 1.1, the data owner 2 includes a second memory 2.2, a second processor 2.1, and is stored on the second memory 2.2 and can be used in the The second computer program running on the second processor 2.1; the client 3 includes a third memory 3.2, a third processor 3.1 and is stored on the third memory 3.2 and can be run on the third processor 3.1 The running third computer program, when the first processor executes the first computer program, implements the steps implemented by the attribute authority in Embodiment 1 or Embodiment 2;
[0139] When the second processor executes the second computer program, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com