Method for validating a node
A node and database technology, applied in the field of verifying the digital signature of at least one node, network, and public key, can solve problems such as download failures, and achieve the effect of improving efficiency and robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 2
[0400] "Embodiment 2". The computer-implemented method of "Embodiment 1", wherein steps b) to e) are performed in parallel with respect to step a).
Embodiment approach 3
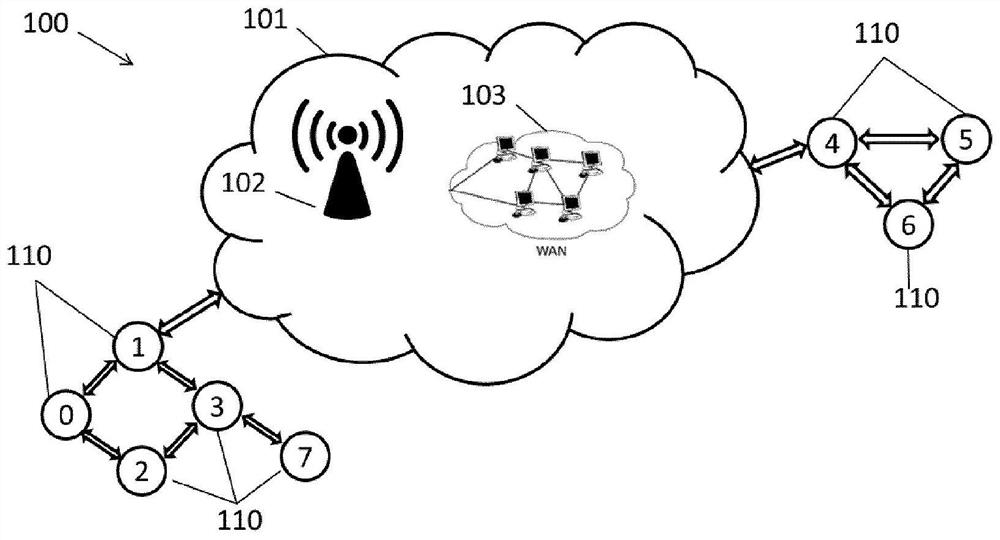
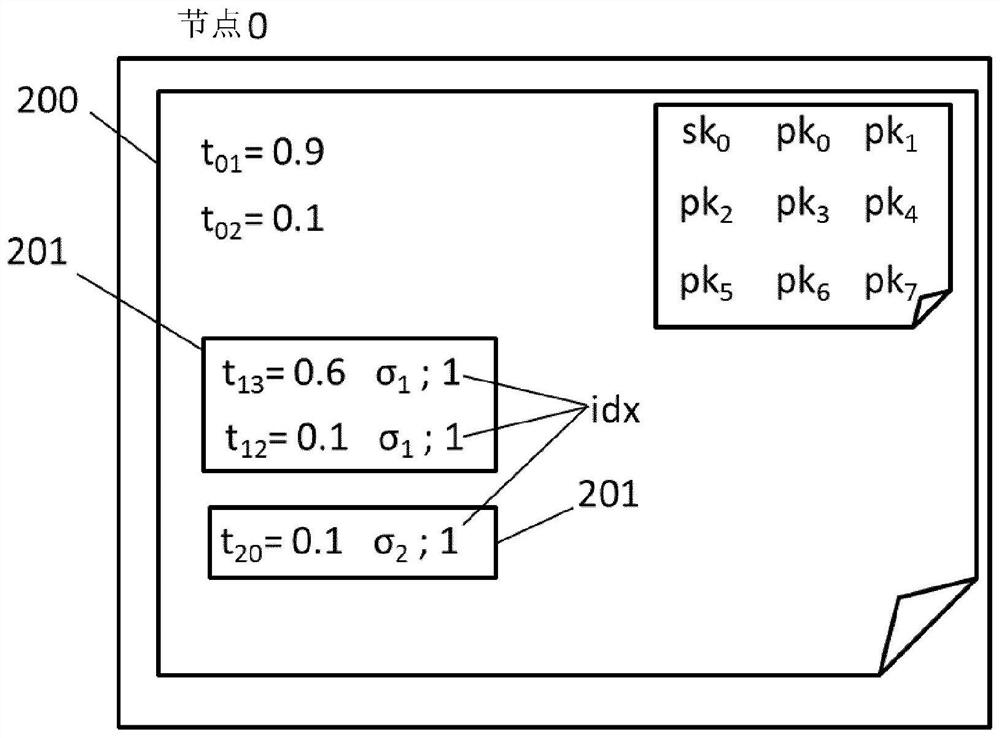
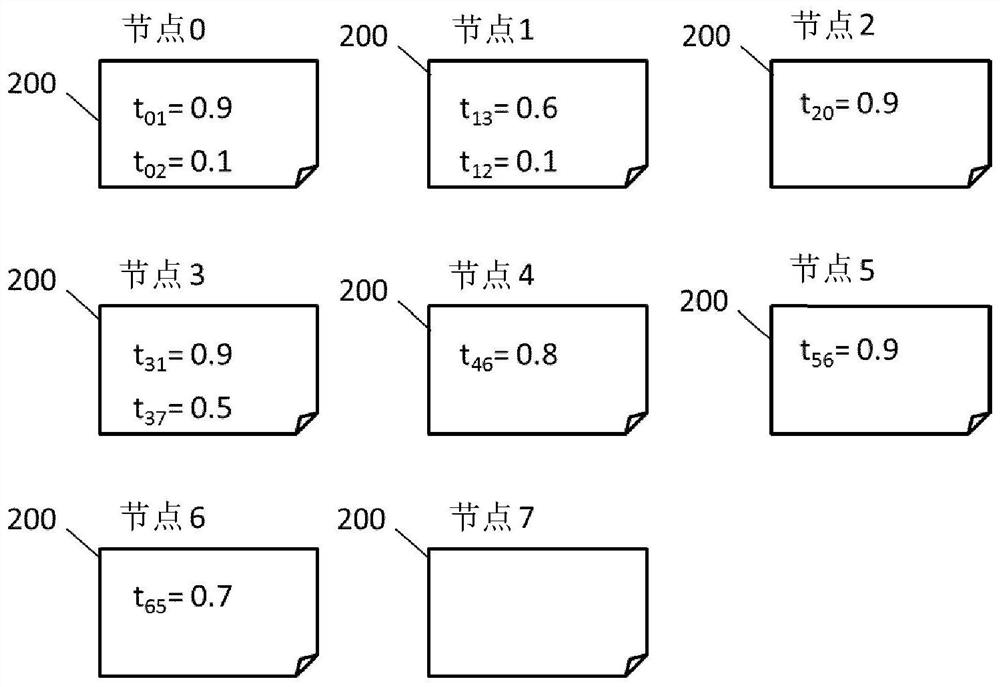
[0401]"Embodiment 3". The computer-implemented method according to any one of the preceding "Embodiments", wherein each node (110) includes at least one public and private node key pair and the remaining nodes of the peer-to-peer network (100) the public key of (110), wherein said public and private node key pair is a public key and a private key associated with each node (110),
[0402] Wherein, at least one endorsement message (201) includes at least one trust endorsement value t, an index value (idx) associated with each trust endorsement value t, and an endorsement signature (σ 1 ,σ 2 );as well as
[0403] wherein said endorsement is signed (σ 1 ,σ 2 ) to sign, and
[0404] Wherein, the gossip algorithm of step a) comprises the following steps:
[0405] a.1 in each node (110) listening to other nodes (110) of the network (100) and detecting at least one endorsement message (201) from said other nodes (110); and
[0406] a.2 For each detected endorsement message (201)...
Embodiment approach 4
[0411] "Embodiment 4". The computer-implemented method according to "Embodiment 3", wherein, between steps a.2.2 and a.3, the gossip algorithm in step a) further includes:
[0412] If at least one trust endorsement value t is new, the detected trust endorsement (201) is added to the database (200).
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com