Bypass interception Bluetooth communication device and method and application thereof
A technology of Bluetooth communication and bypass interception, applied in security devices, wireless communication, short-distance communication services, etc., can solve the problems of efficiency improvement, cost saving but not obvious effect, obstacles to digital transformation of equipment, etc., to avoid node disconnection The effect of network congestion, facilitating digital transformation, reducing usage impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
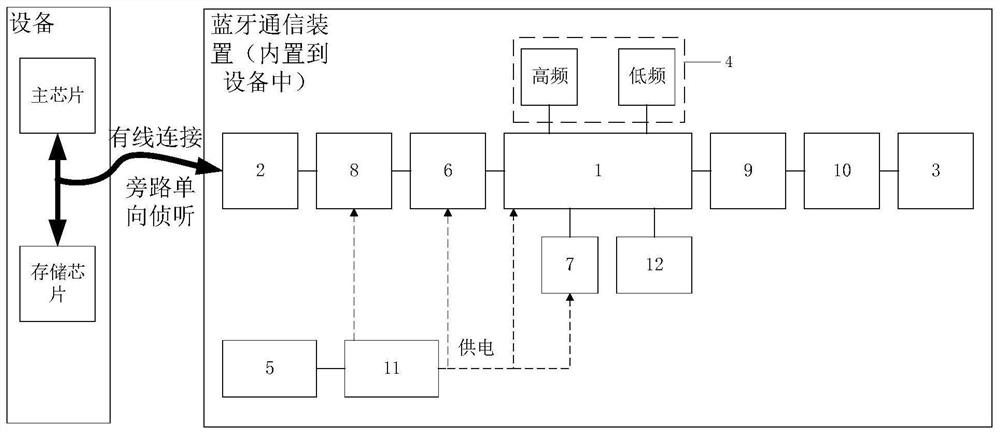
[0041] Such as figure 1 As shown, a bluetooth communication device for bypass listening, which is built in the device to be listened to as a whole, including a bluetooth main chip 1, a listening interface circuit 2, a bluetooth antenna 3, a crystal oscillator circuit 4, a display circuit 7 and an isolation Power supply 5, wherein, the listening interface circuit 2 is connected with the bluetooth main chip 1 through the signal conditioning circuit 6, and the listening interface circuit 2 is bypass-connected to the main chip of the intercepted device and the data interaction line of the storage chip, which can The interface of the intercepted data interaction line includes a parallel bus interface, a serial bus interface, a single bus interface and various privately defined interfaces, etc., and the hardware signal of the data stream first enters the device through the interception interface circuit 2, and the signal conditioning circuit 6 Carry out shaping, expansion, expansion...
Embodiment 2
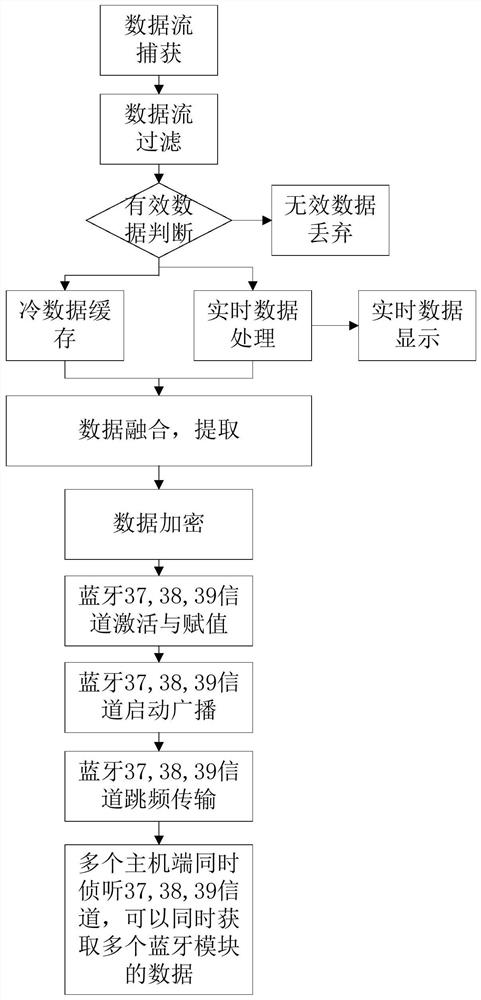
[0050] Such as figure 2 As shown, this embodiment provides a Bluetooth communication method for bypass listening, including the following steps:
[0051] 1) Listen to the data transmission of the listened device in real time through the bypass listening mode, and execute step 2) when the data flow is captured;
[0052] 2) Filtering the data stream;
[0053] 3) judging whether the data stream is valid data, if so, then perform step 4), if not, discard the data stream;
[0054] 4) If the data stream is real-time data, real-time data display is performed, and if it is cold data, cold data cache is performed;
[0055] 5) Extracting the transmission data that needs to be transmitted from the data stream, that is, parsing out the required data packets, and encrypting the transmission data;
[0056] 6) Use the non-networking multi-to-many Bluetooth transmission method to realize the transmission of the encrypted transmission data, specifically: fill the encrypted transmission dat...
Embodiment 3
[0062] This embodiment provides a method for implementing digital transformation of a device. The device is used as an intercepted device, and the above-mentioned bypass intercepted Bluetooth communication device is bypassed into the intercepted device. Typical application cases include the data interaction interception between the main chip of the forehead thermometer and the EEPROM memory chip, the data interaction between the memory of the industrial gateway and the flash memory chip, etc.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com