Single sign-on method and system
A single sign-on, external system technology, applied in the field of network communication, can solve problems such as low user experience and lack of practicality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] Embodiment 1, a single sign-on method, such as figure 1 shown, including the following steps:
[0062] S100. Obtain a login request of an external system, where the login request includes a token;
[0063] S200. Verify the token, and obtain a corresponding external account when the verification is successful;
[0064] S300. Obtain an internal account mapped to the external account;
[0065] S400. Complete login based on the internal account.
[0066]In this embodiment, the application system where the user is located is used as the external system, and the associated system through which the user signs on through the application system is used as the internal system. steps performed in .
[0067] The above-mentioned external account is the account information for the user to log in to the external system, and the internal account is the account information for the user to log in to the internal system, and the account information includes an account and a password. ...
Embodiment 2
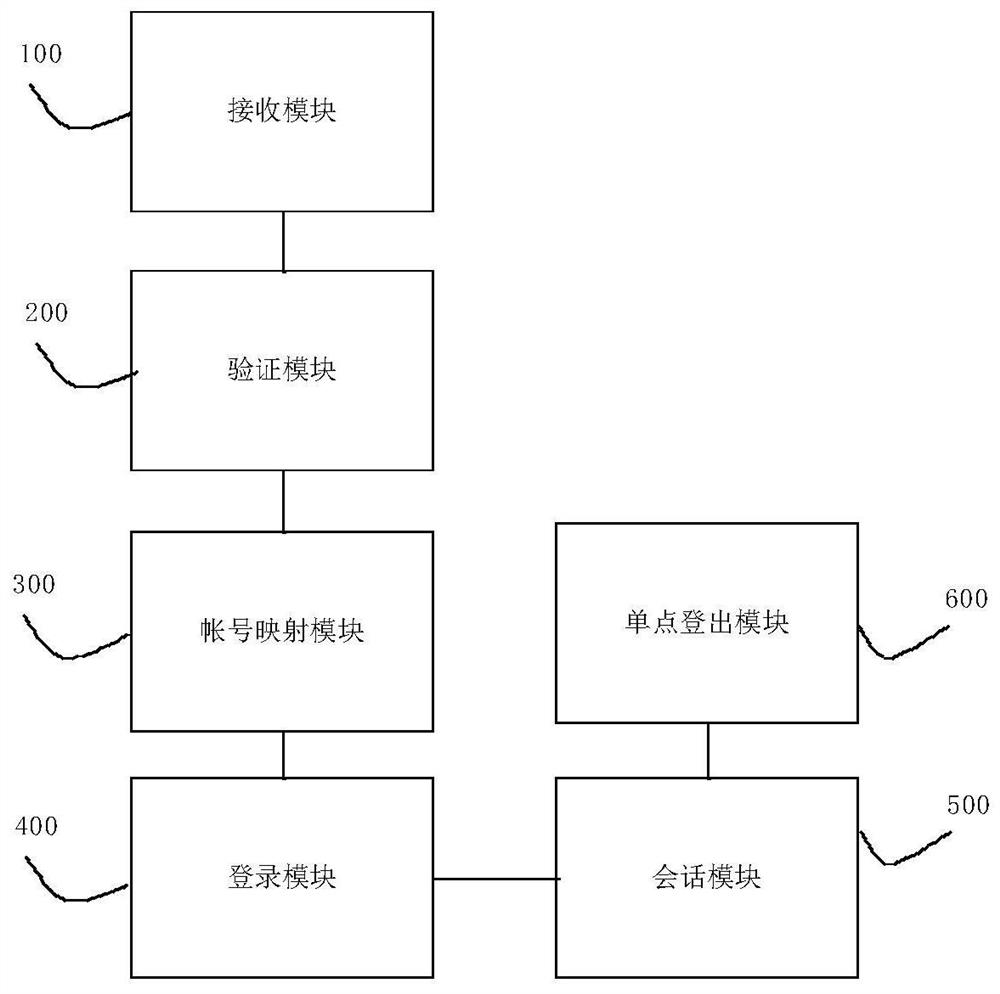
[0144] Embodiment 2, a single sign-on system, such as figure 2 As shown, it includes a receiving module 100, a verification module 200, an account mapping module 300 and a login module 400;
[0145] The receiving module 100 is configured to obtain a login request of an external system, the login request includes a token; the login request also includes a user ID and a signature;
[0146] The verification module 200 is configured to verify the token, and obtain a corresponding external account when the verification is successful;
[0147] The account mapping module 300 is configured to obtain an internal account mapped to the external account;
[0148] The login module 400 is configured to complete login based on the internal account.
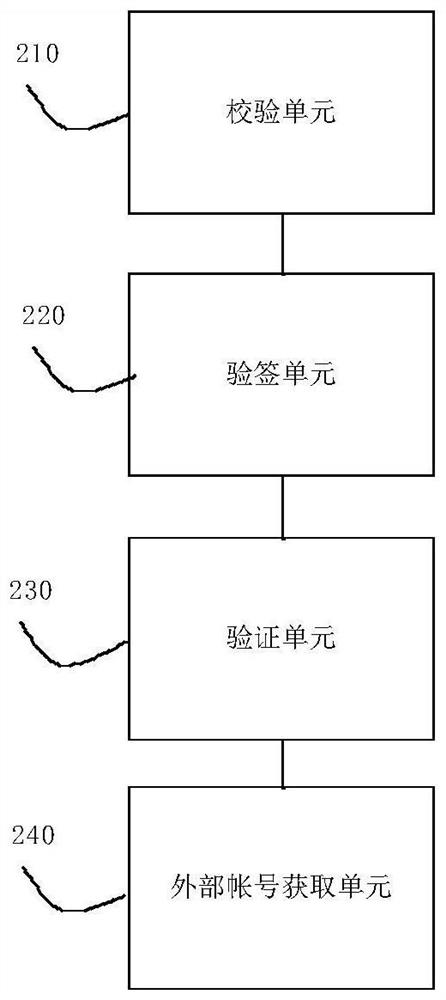
[0149] refer to image 3 , the verification module 200 includes a verification unit 210, a signature verification unit 220, a verification unit 230 and an external account acquisition unit 240;
[0150] The checking unit 210 is configured t...
Embodiment 3
[0166] Embodiment 3. A computer-readable storage medium stores a computer program, and when the program is executed by a processor, the steps of the method described in Embodiment 1 are implemented.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com