Container environment anomaly detection method and device, medium and computer equipment
An anomaly detection and container technology, applied in the field of network security, can solve problems such as high modeling costs and inability to ensure detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
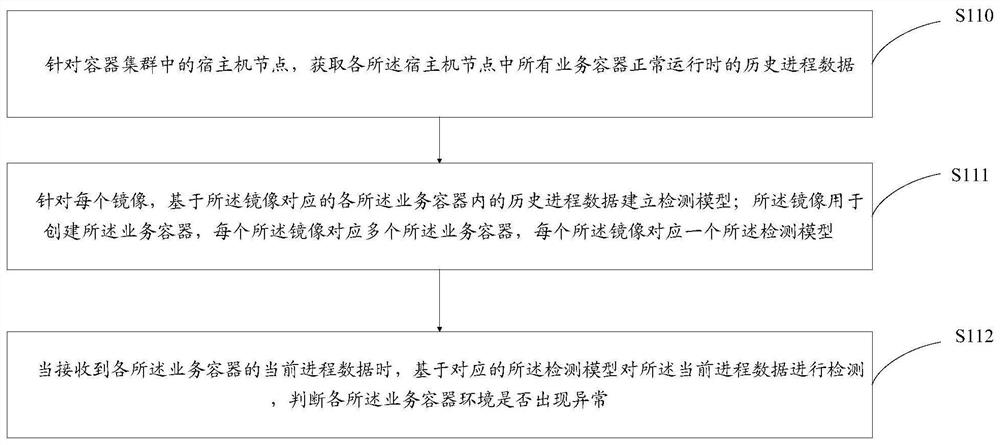
[0049] This embodiment provides a method for detecting anomalies in a container environment, such as figure 1 As shown, the methods include:
[0050] S110, for the host nodes in the container cluster, collect historical process data of all business containers in each host node when they are running normally;
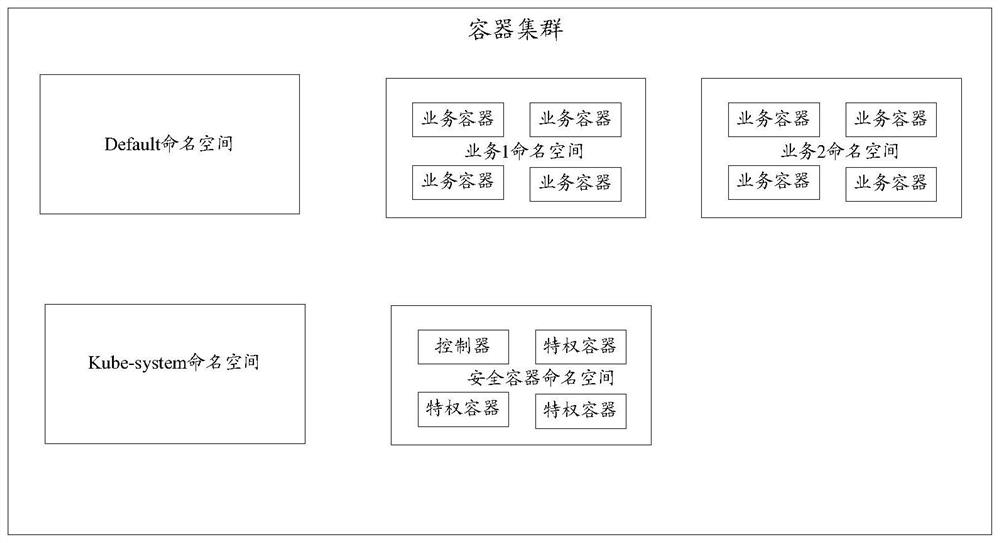
[0051]In a distributed system, there are multiple hosts, one host is a node, and multiple containers are deployed on each host node to form a container cluster.
[0052] In order to ensure the processing efficiency of each host node, after the container is created, it is deployed uniformly by the background management module of the distributed system; the background management unit determines the optimal deployment method according to the current resource occupancy rate of each host node . In this way, even different containers created by the same image may be deployed on different host nodes.
[0053] For the host nodes in the container cluster, collect the historica...
Embodiment 2
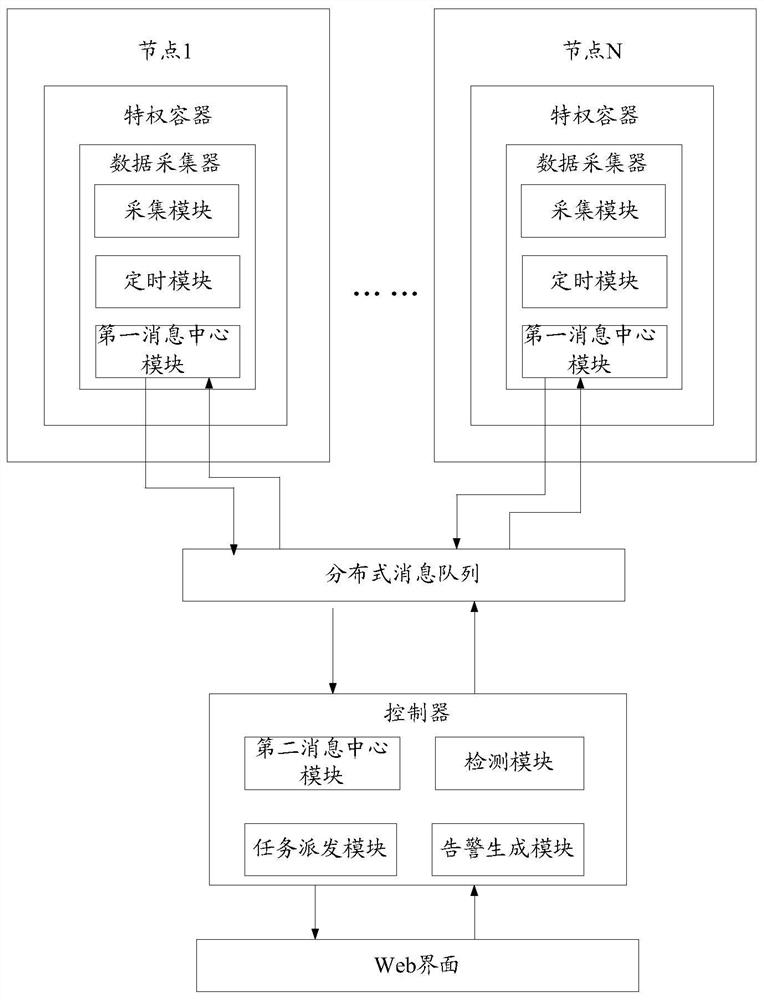
[0102] This embodiment provides a container environment anomaly detection device, such as Figure 6 As shown, the device includes: an acquisition module 61, an establishment module 62 and an abnormality detection module 63; wherein,
[0103] The acquisition module 61 is used to collect historical process data of all business containers normally running in each host node for the host nodes in the container cluster;
[0104] Establishment module 62 is used for establishing detection model based on the historical process data in each service container corresponding to the image for each image; the image is used to create service containers, each image corresponds to multiple service containers, and each image corresponds to a detection model;
[0105] The anomaly detection module 63 is configured to detect the current process data based on the corresponding detection model when receiving the current process data of each service container, and judge whether the environment of eac...
Embodiment 3
[0154] This embodiment provides a computer device, such as Figure 7 As shown, it includes a memory 70, a processor 71 and a computer program 72 stored on the memory 70 and operable on the processor 71. When the processor 71 executes the computer program 72, the following steps are implemented:
[0155] For the host nodes in the container cluster, obtain the historical process data of all business containers in each host node when they are running normally;
[0156] For each image, a detection model is established based on the historical process data in each of the service containers corresponding to the image; the image is used to create the service container, each of the images corresponds to a plurality of the service containers, and each Each of the mirror images corresponds to one of the detection models;
[0157] When the current process data of each of the service containers is received, the current process data is detected based on the corresponding detection model to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com