Self-adaptive modeling method and system for safety control strategy of power system sent by power supply cluster
A technology of power system and modeling method, which is applied in circuit devices, AC network circuits, and single-network parallel feeding arrangements, etc., can solve the problems of frequent adjustment of security control strategies and inability to meet the needs of scheduling operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0121] Compared with the traditional method of manually maintaining the security control policy table and security E file, which cannot meet the needs of dispatching and operation, this embodiment proposes a power system security control strategy self-adaptation that uses computer technology to automatically realize the power cluster sending. modeling method.
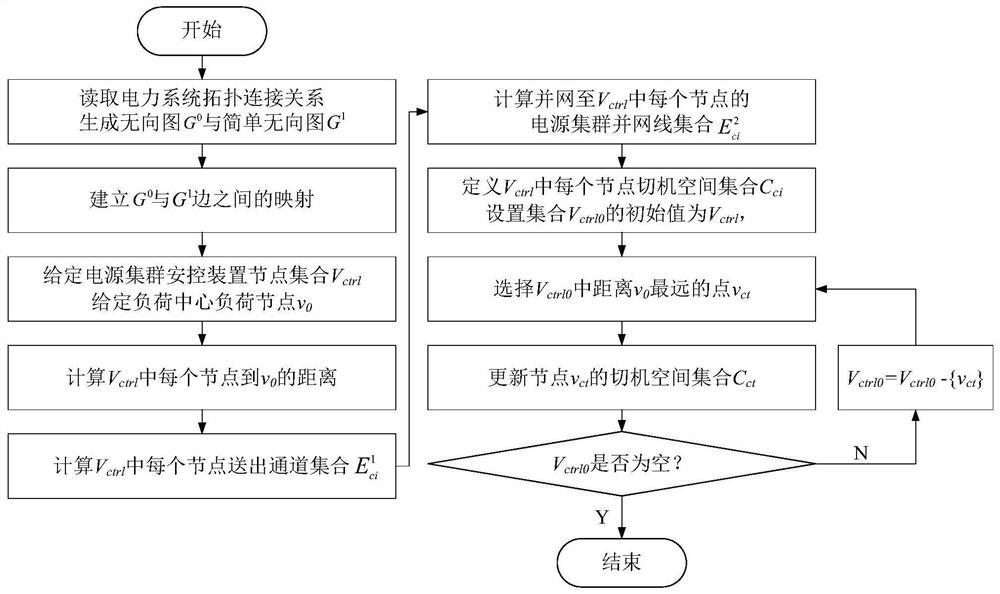
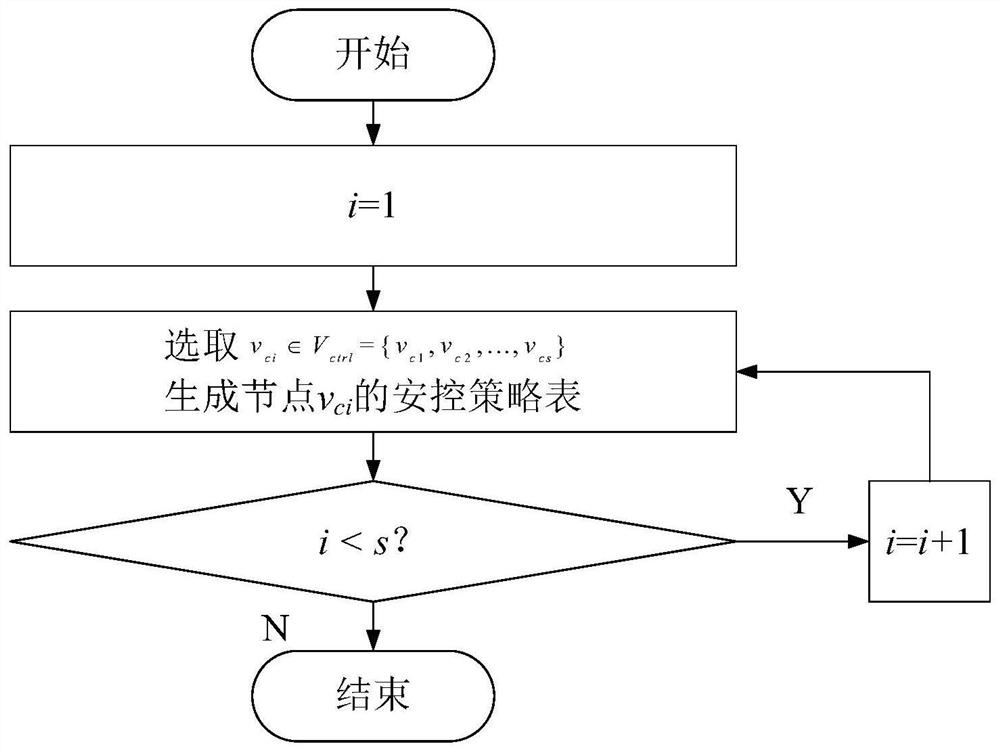
[0122] The following combination figure 1 , figure 2 , image 3 , Figure 4 , the method of the present invention is described in detail.
[0123] In this embodiment, according to the stable section control limit information in the power grid stability operation management regulations, the relevant constraint conditions of the modeled equipment in the power grid dispatching automation system are described in a structured manner according to the agreed stability rule description method; for unstructured information or unmodeled The relevant information of the equipment is supplemented by the remark text, so as to re...
Embodiment 2
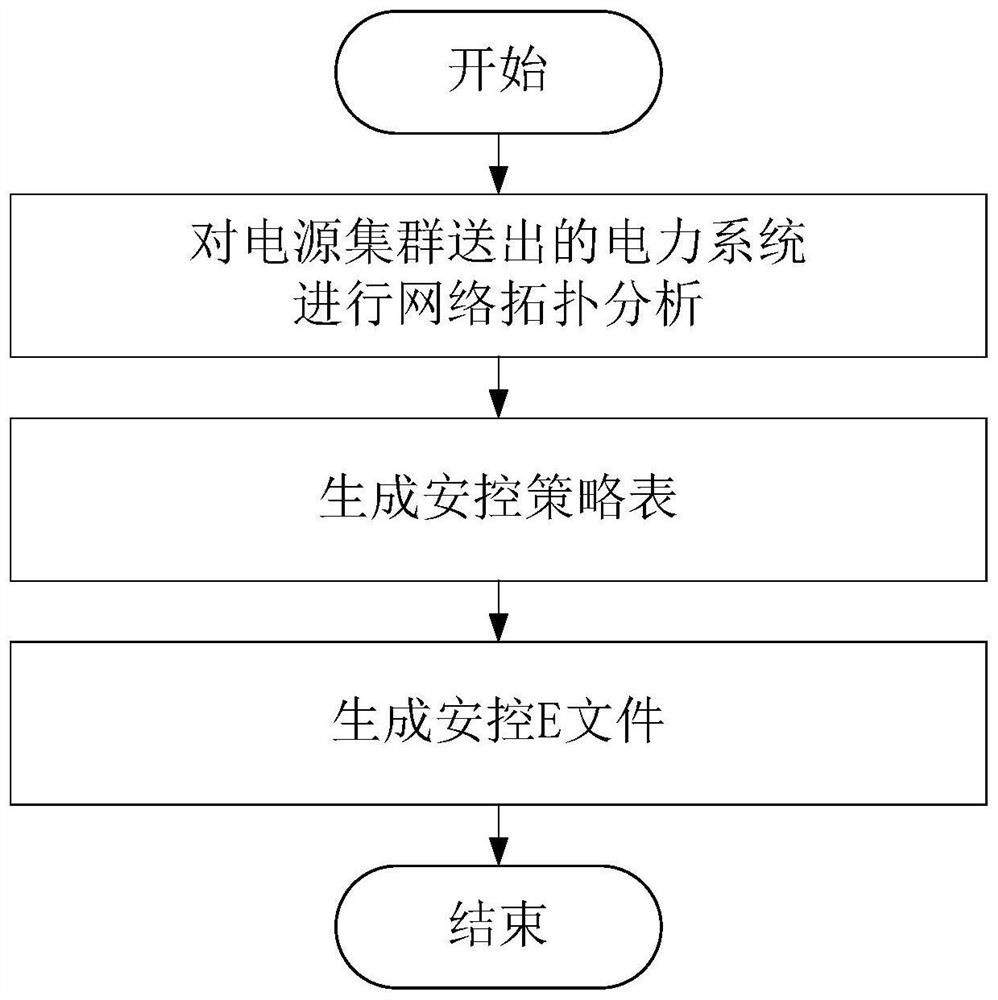
[0278] This embodiment proposes an adaptive modeling system for power system security control strategies sent by power clusters, such as Figure 5 As shown, the system of the present embodiment includes a topology analysis module, a safety control strategy table generation module and a safety control E file generation module;
[0279] Wherein, the topology analysis module of this embodiment is used to analyze the network topology of the power system sent by the power cluster;
[0280] The security control policy table generating module of this embodiment is used to generate the security control policy table according to the topology analysis result;
[0281] The security control E file generating module of this embodiment is used to generate the security control E file according to the topology analysis result and the security control strategy table.
[0282] The topology analysis module of this embodiment includes: a topology map generation unit, a mapping unit
[0283] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com