Named entity identification method oriented to field of network security
A technology for named entity recognition and network security, applied in the field of named entity recognition, it can solve the problems of poor applicability and migration, weak versatility, performance dependence, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings and examples. It should be understood that the specific embodiments are for better explaining the present invention, and all technologies realized based on the content of the present invention belong to the scope of the present invention.
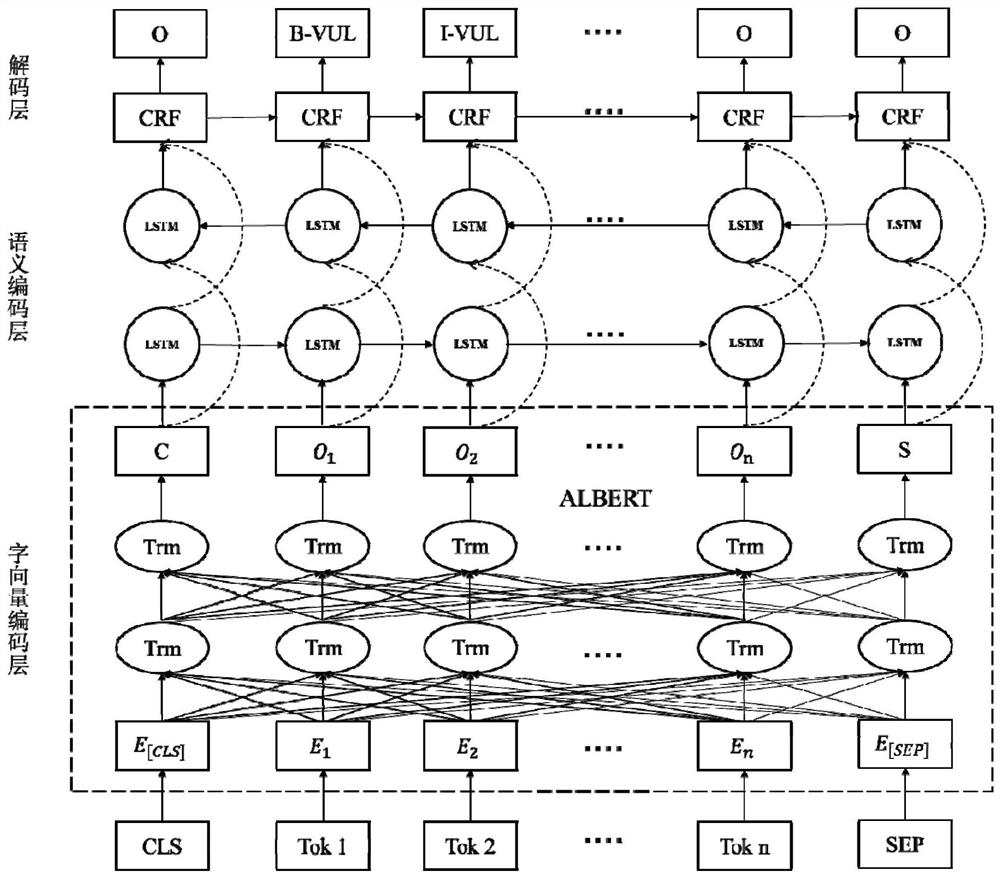
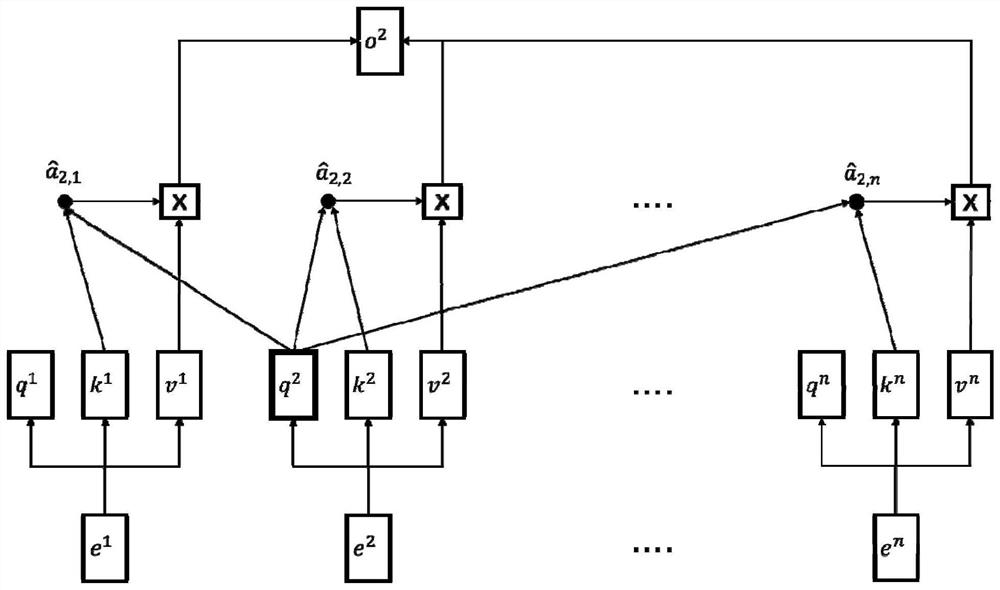
[0028] refer to Figure 1 to Figure 3 , a named entity recognition method oriented to the field of network security, comprising the following steps:
[0029] Step 1, design a crawler program, obtain relevant network security text data from various information sources such as vulnerability information database, security forum, and enterprise emergency response center, and store them in the database. The embodiment obtains network security text data by crawling respectively from China National Information Security Vulnerability Database (CNNVD), FreeBuf Security Forum, and Sangfor Security Center.
[0030] Step 2, use ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com