System and method for determining anomaly source in cyber-physical system having certain characteristics
A cyber-physical system, abnormal technology, applied in transmission systems, data exchange networks, digital transmission systems, etc., to solve problems such as incorrect operation of computer equipment, increased power consumption, unauthorized access to information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
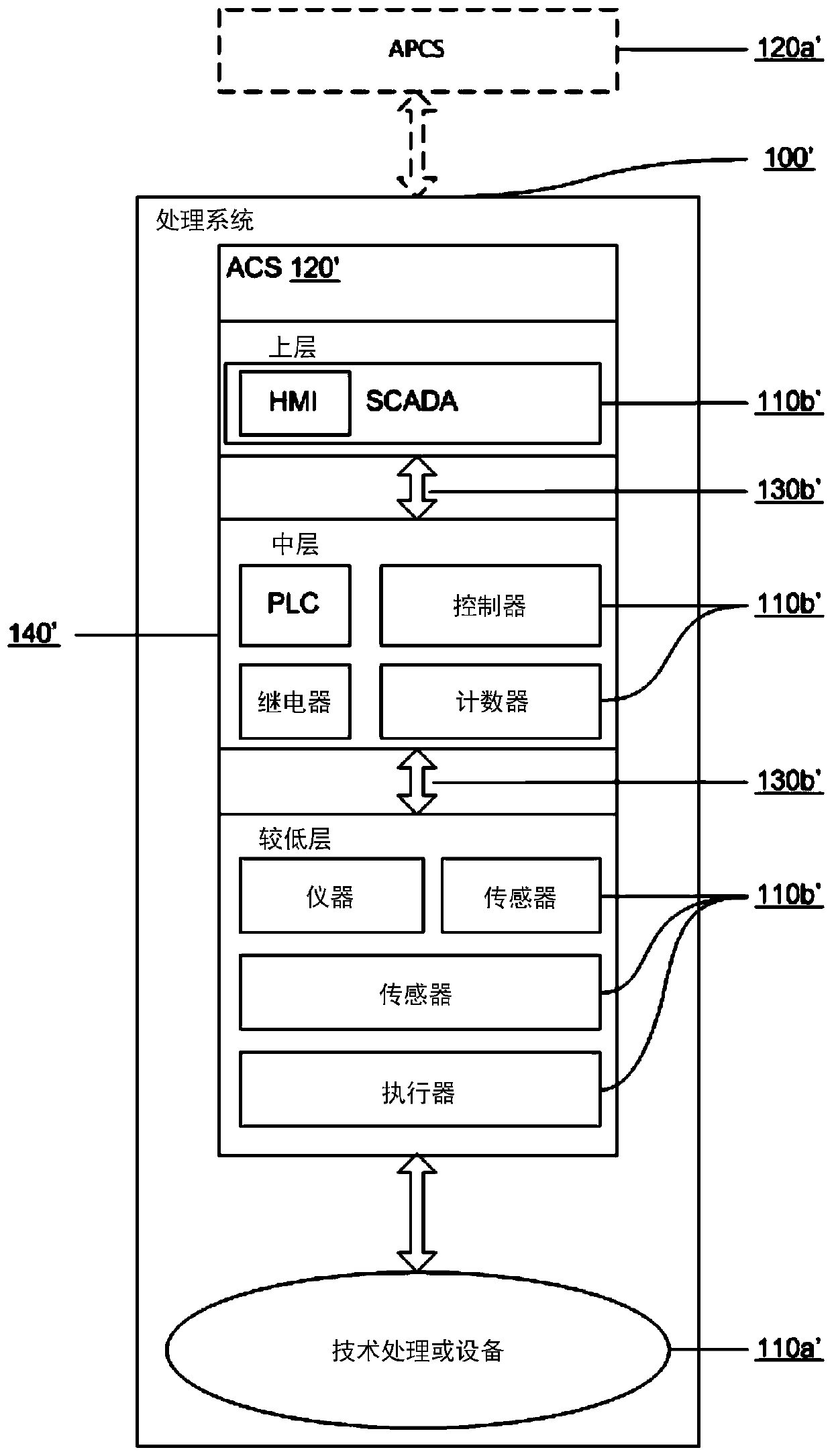
[0037] The following definitions and concepts are used throughout the description, especially the examples.
[0038] For example, a controlled object is a process object to which external influences (control and / or disturbance) are directed in order to change its state. In an embodiment, such objects may be devices (eg, electric machines) or processes (or parts thereof).
[0039] In an embodiment, a technical process (TP) may be a material production process comprising a continuous change in the state of a material substance (work object).
[0040] In an embodiment, a process control may be a set of methods used to control technical parameters when producing a final product.
[0041] In an embodiment, a control loop may consist of a material substance and a control function for automatically controlling the measured technical parameter value towards a desired set point value. The control loop consists of sensors, controllers and actuators.
[0042] In an embodiment, a proce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com