Message expansion circuit of secure hash algorithm
A secure hash algorithm and circuit technology, applied in the protection of internal/peripheral computer components, etc., can solve problems such as high power consumption and achieve the effect of reducing power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, and do not limit the protection scope of the present invention.
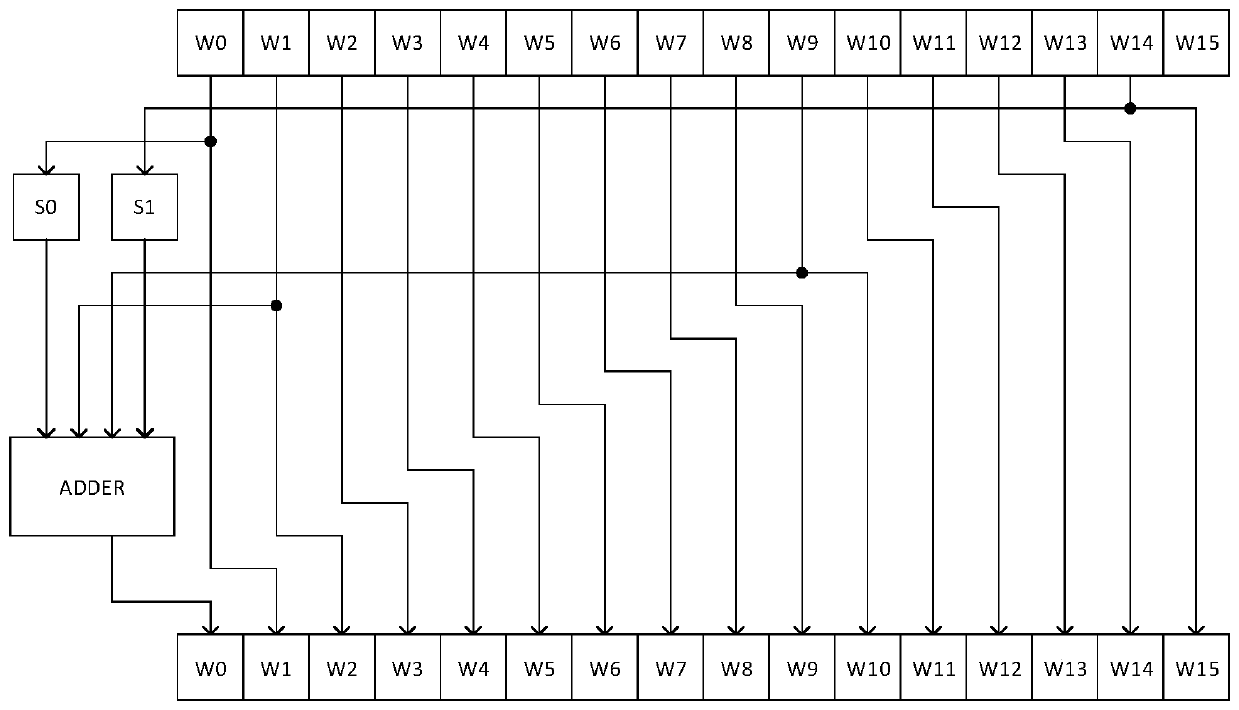
[0036] In order to solve the problem of high power consumption caused by secure hash algorithm operations. This embodiment provides a message expansion circuit for a secure hash algorithm. The following embodiments take SHA256 as an example to illustrate the message expansion circuit of SHA256.
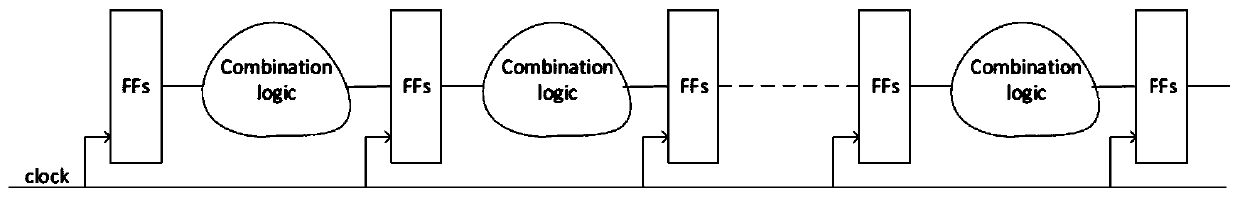
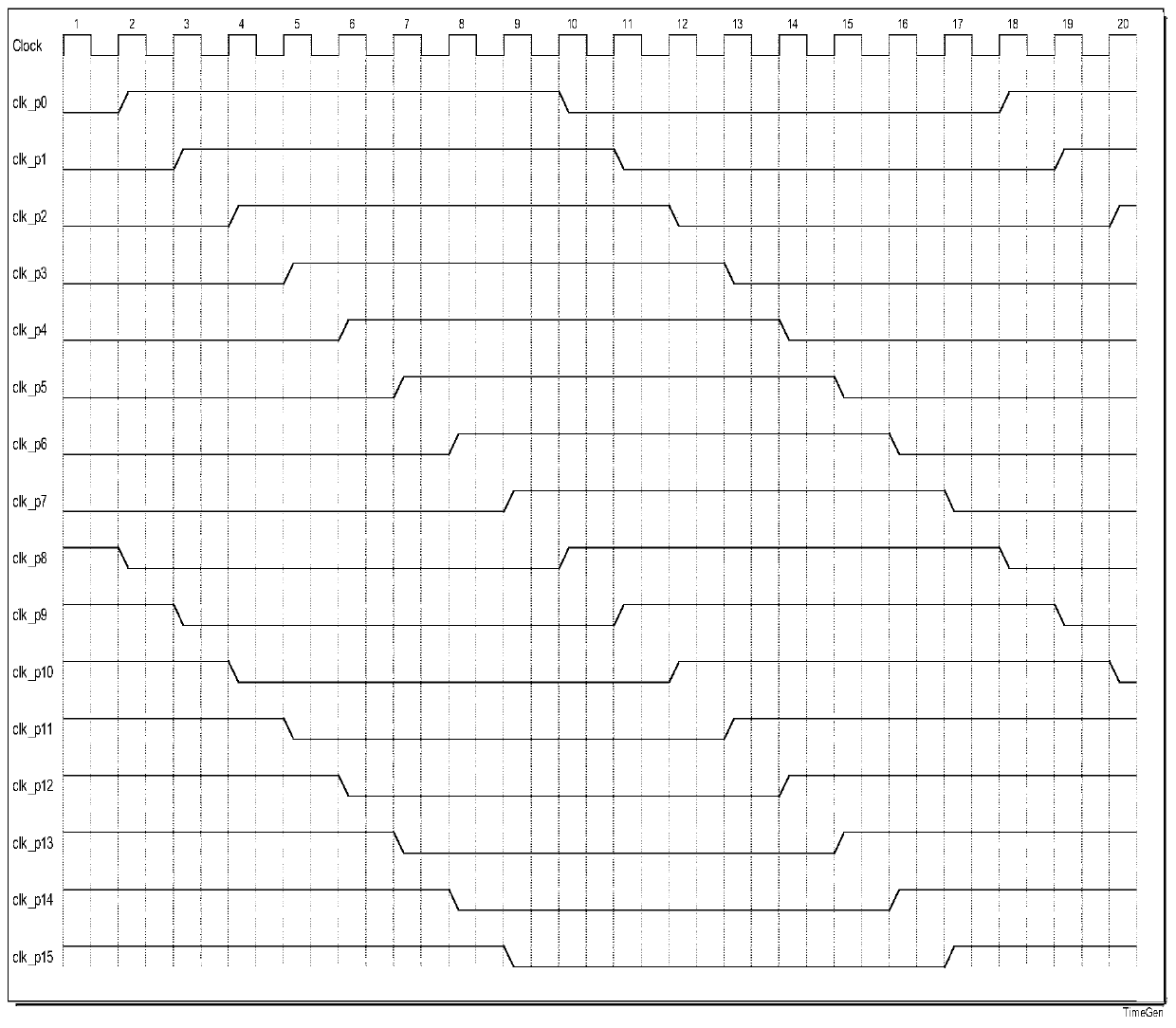
[0037] In order to obtain faster frequency and throughput in Bitcoin special-purpose chips, the usual practice is to use full pipeline implementation. Because SHA256 has 64 rounds of operations, there are a total of 64 levels of pipeline. Each stage processes a round of infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com