Source code vulnerability detection method based on graph convolution network
A convolutional network and source code technology, applied in the field of computer network security, can solve the problems of low false negative rate and false positive rate, and the inability of static detection technology of source code vulnerabilities to use graph representation at the same time, so as to narrow the scope and reduce the the effect of time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
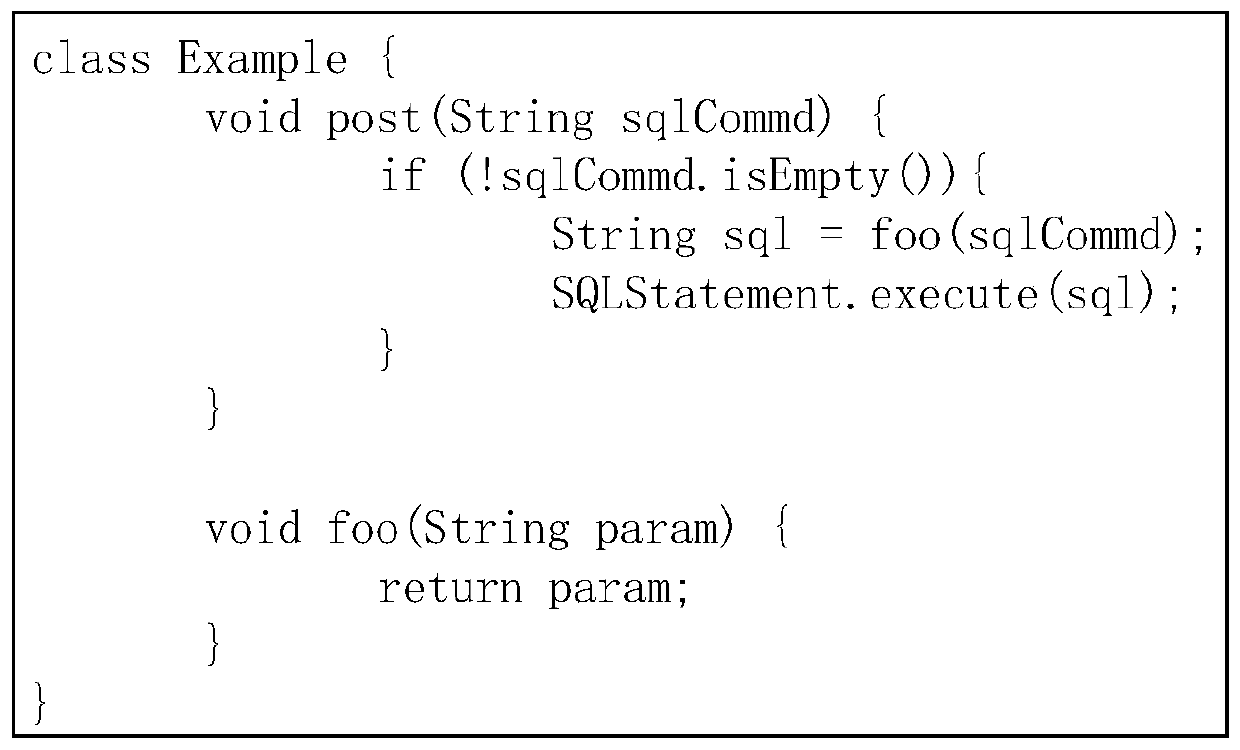
[0034] It should be noted that the automatic detection method for source code vulnerabilities based on graph convolutional networks of the present invention is not limited to specific programming languages. The specific details of the invention.
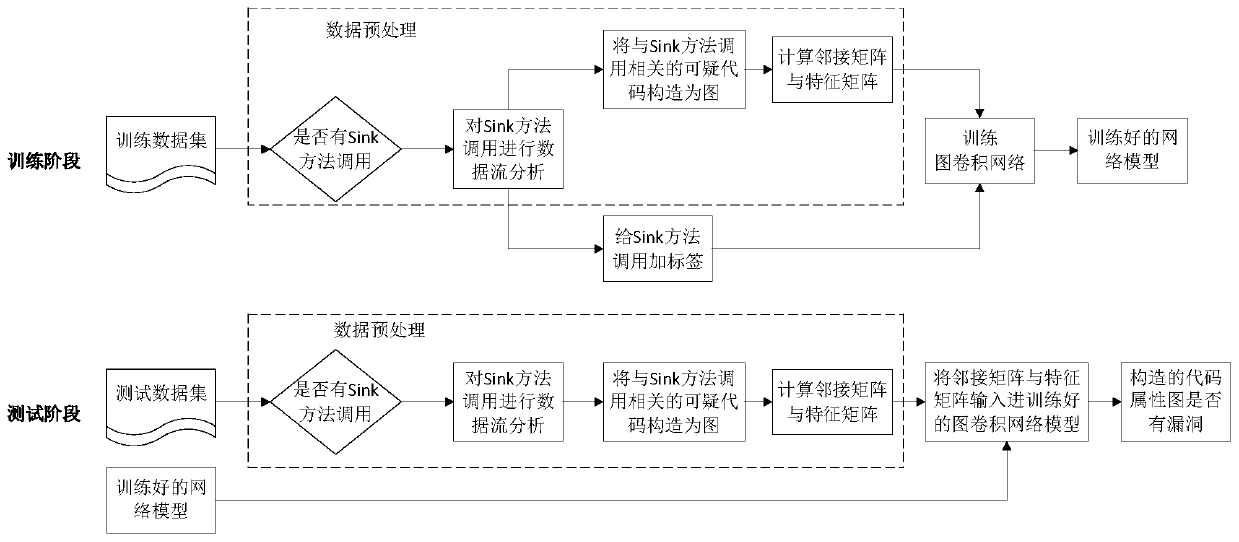
[0035] according to figure 1 As shown, this embodiment provides a method for automatic detection of source code vulnerabilities based on graph convolutional networks, including a training phase and a testing phase, wherein:
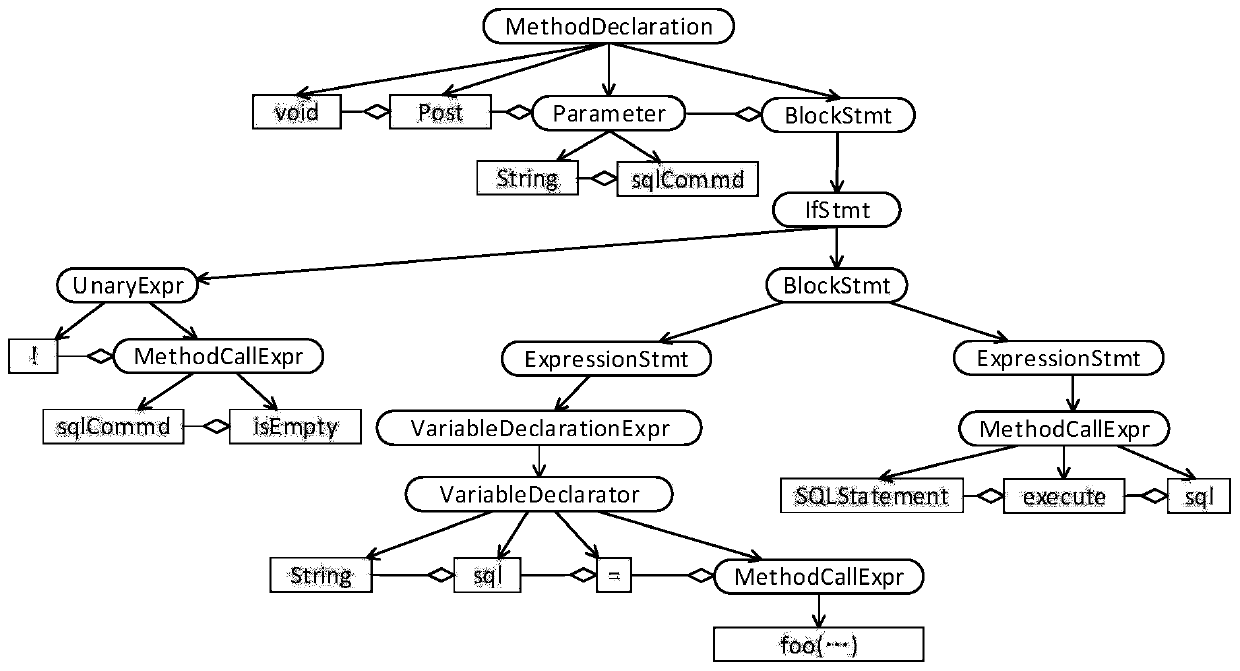
[0036] In the training phase, data acquisition and data preprocessing are performed on the training data set. The process of data preprocessing is to first judge whether the source code of the test data set has a sink method call, analyze the data flow of the sink method call, and then compare the source code with The suspicious code related to the sink method call is constructed as a code attribute graph, and the adjacency matrix and characteristic matrix of the code attribute graph are calculated, and the sin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com