Two-party elliptic curve digital signature algorithm supporting key refreshing
An elliptic curve and key technology, applied in the field of cryptography, can solve problems such as key shares cannot be refreshed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] The specific implementation of the present invention is mainly divided into two parts: the code is written using the Golang programming language, and the elliptic curve digital signature algorithm is implemented as a library, which can be directly embedded in the application for use.
[0066] Algorithm module:
[0067] The algorithm module is mainly responsible for the implementation of the two-party elliptic curve signature algorithm, and the three interfaces of key generation, signature, and key refresh can be implemented according to specific programming languages.
[0068] External service module:
[0069] The external service module refers to packaging the algorithm, and only opens three interfaces to users: the three functions of KeyGen(), Sign() and Refresh().
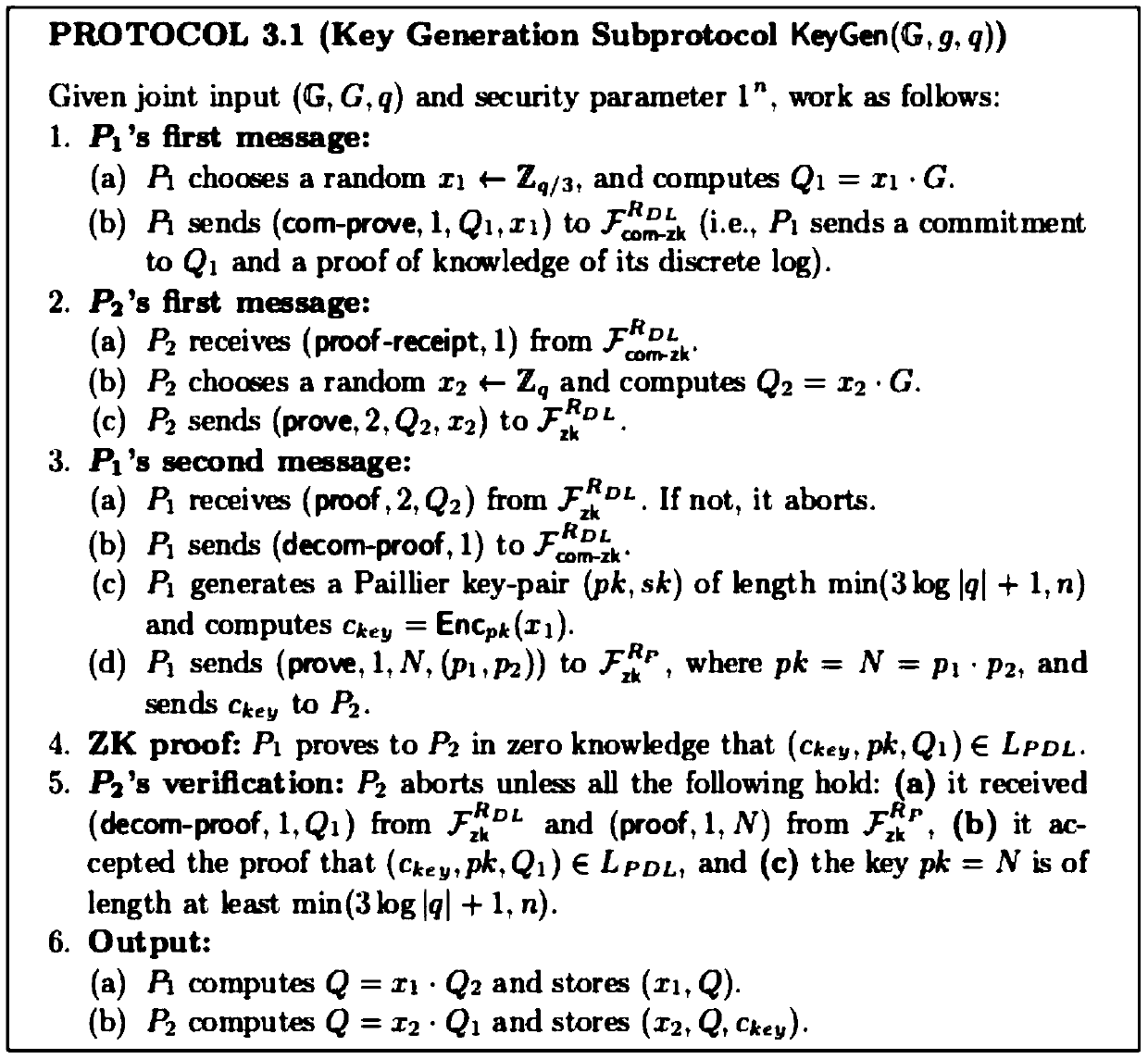
[0070] Appendix 1, Two-Party Key Generation Process
[0071]
[0072] Appendix 2 Two-Party Signature Process
[0073]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com