SIM chip security and credibility authentication system and authentication method thereof
A security authentication and chip technology, applied in security communication devices, transmission systems, digital transmission systems, etc., can solve the problem of inability to effectively prevent SIM chip data leakage from SIM chip network attacks, lack of user authentication of mobile terminal equipment and networks, and threats to equipment and network security issues, to achieve the effect of increasing trusted authentication functions, realizing self-security, and increasing security self-inspection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
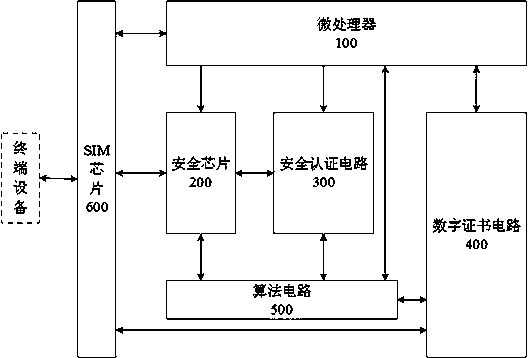
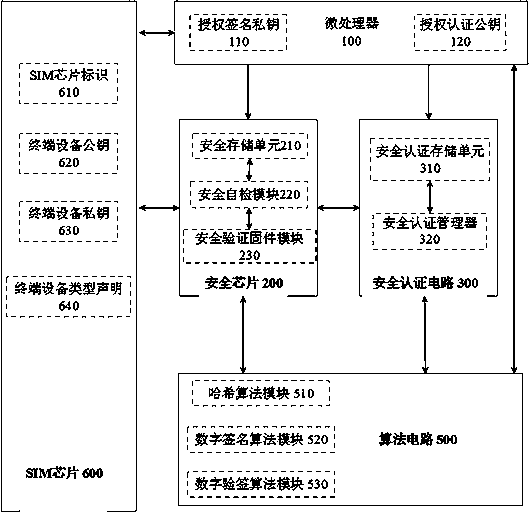
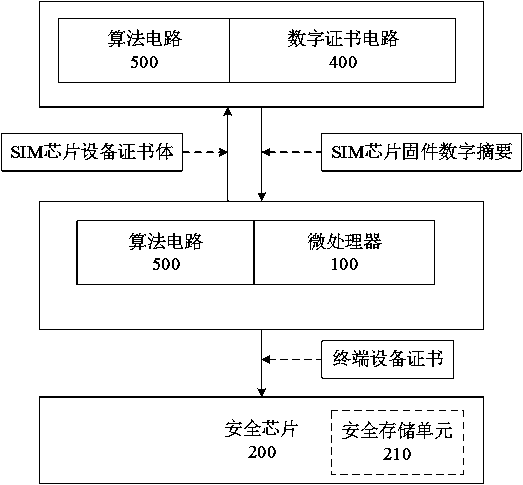
[0026] see figure 1 As shown, it is a structural frame diagram of the SIM chip security and trusted authentication system implemented in the present invention. The SIM chip safe and trusted authentication system includes a microprocessor 100, a security chip 200, a security authentication circuit 300, a digital certificate circuit 400, an algorithm circuit 500 and a SIM chip 600, wherein the microprocessor 100 is connected to the security chip 200, the security authentication circuit 300, the digital certificate circuit 400, the algorithm circuit 500 and the SIM chip 600, the SIM chip 600 is connected to the security chip 200, the security authentication circuit 300, the digital certificate circuit 400 and the algorithm circuit 500 in sequence, and the security chip 200 is connected to the algorithm circuit 500, the algorithm circuit 500 is connected to the digital certificate circuit 400, the digital certificate circuit 400 is connected to the SIM chip 600 and the microproces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com