File multi-encryption two-dimensional code electronic encryption and decryption management system and method
A multi-encryption, encryption and decryption technology, applied in electronic digital data processing, computer parts, record carriers used by machines, etc., can solve problems such as loss and disorderly dissemination of classified electronic files, and improve management capabilities and management effectiveness. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in combination with specific embodiments and with reference to the accompanying drawings. It should be understood that these descriptions are exemplary only, and are not intended to limit the scope of the present invention. Also, in the following description, descriptions of well-known structures and techniques are omitted to avoid unnecessarily obscuring the concept of the present invention. see figure 1 , figure 2 , image 3 .
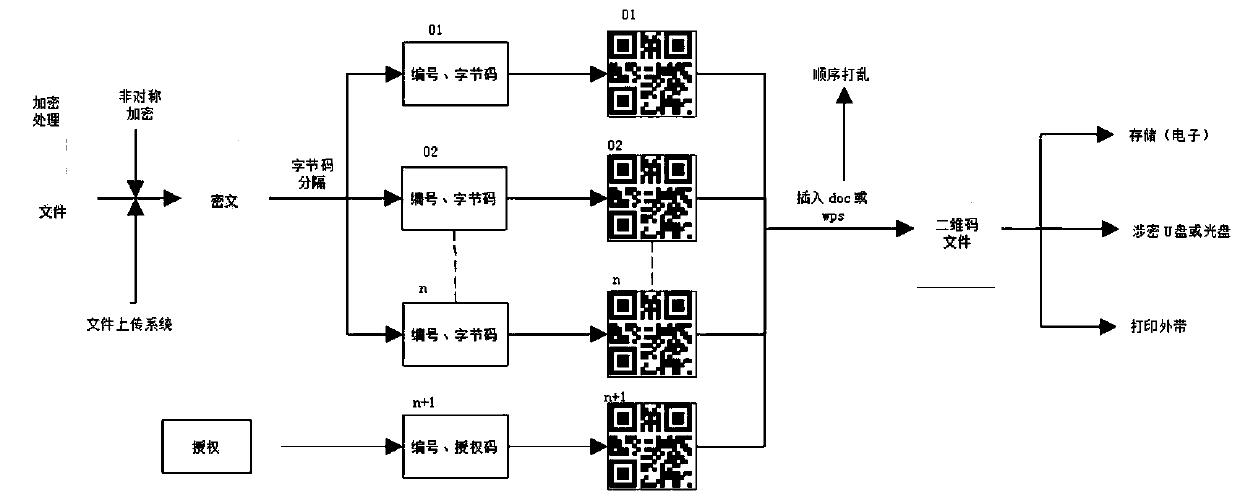
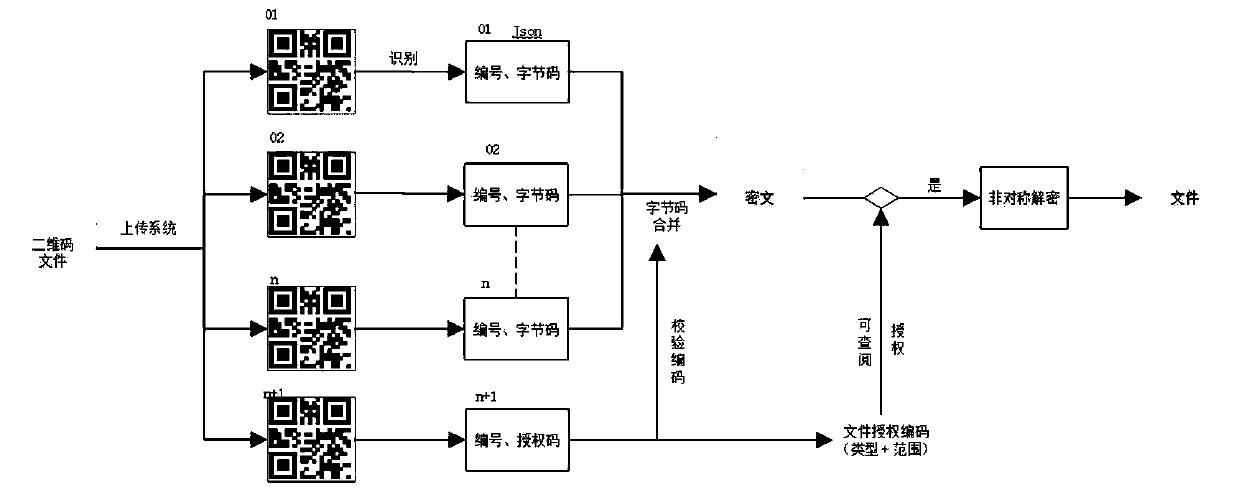
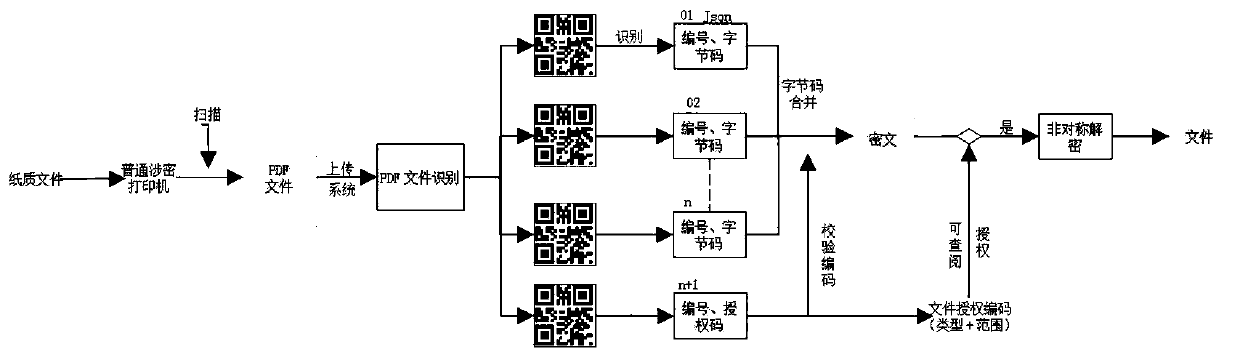
[0031] Embodiment 1: A two-dimensional code electronic encryption and decryption management system for multiple encryption of files, including: a file acquisition and encryption module, used to obtain a file to be encrypted, and convert it into a ciphertext file according to an encryption protocol; a ciphertext splitting module , which is used to obtain the bytecode of the ciphert...
Embodiment 2
[0039] A two-dimensional code electronic encryption and decryption method for multiple file encryption, comprising the following steps:
[0040] S1. Obtain the file to be encrypted, and convert it into a ciphertext file according to the encryption protocol;
[0041] S2. Obtain the bytecode of the ciphertext file, divide the bytecode into several bytecode segments according to the number of bytes, and perform data encoding in sequence to obtain the corresponding bytecode for each bytecode segment Encoded data including sequence number and byte code content; the data is encoded as JSON data encoding, and is encoded in segments within 900 bytes per segment, or 900-1500 bytes; the data encoding also includes each segment The number of the corresponding row number of the byte code segment arranged in order, where the number of the last byte code segment also includes the termination character
[0042] S3. Generate a plurality of two-dimensional code graphic information correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com