Unified authentication and authorization scheme
An authentication and solution technology, applied in the information field, can solve problems such as inability to communicate personnel information, low efficiency of multi-system login, and user inconvenience, and achieve the effect of protecting information security, reducing the probability of being stolen, and reducing the cost of employee use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and embodiments. However, it should be understood that the specific embodiments described here are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0017] Unless otherwise defined, all technical terms and scientific terms used herein have the same meaning as commonly understood by those skilled in the technical field of the present invention, and the terms used in the description of the present invention herein are only to describe specific implementations The purpose of the example is not intended to limit the present invention.
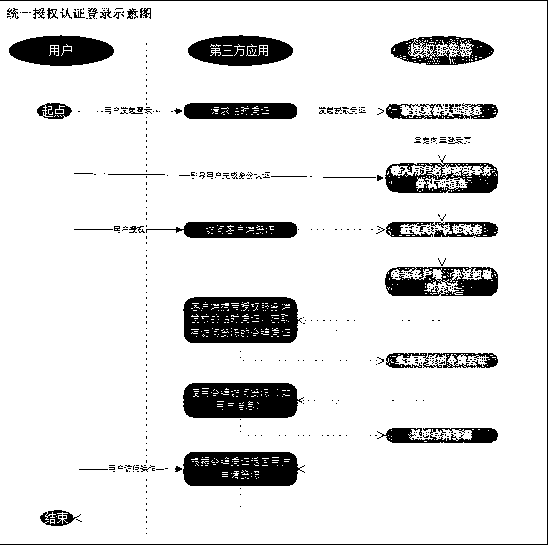
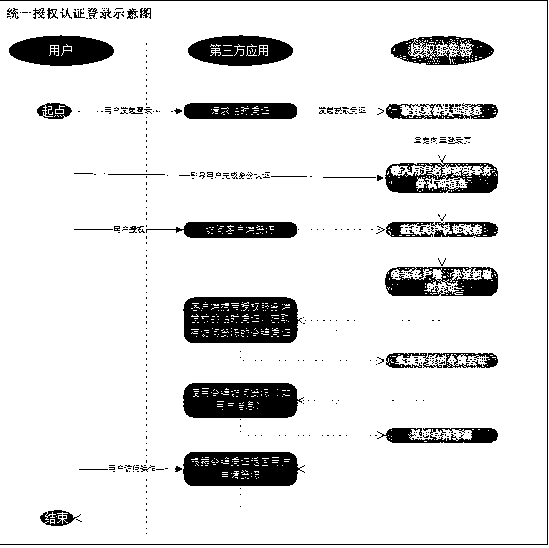
[0018] Such as figure 1 As shown, a unified authentication and authorization scheme includes the following steps;
[0019] Step 1: The third-party system introduces the authori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com