Information security and function security association analysis method
A technology of information security and correlation analysis, applied in the field of information security, can solve the problem of lack of integrated risk assessment method of cyber-physical mixed-layer system, and achieve the effect of enhancing authority and scientificity, enhancing quantification, and avoiding errors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
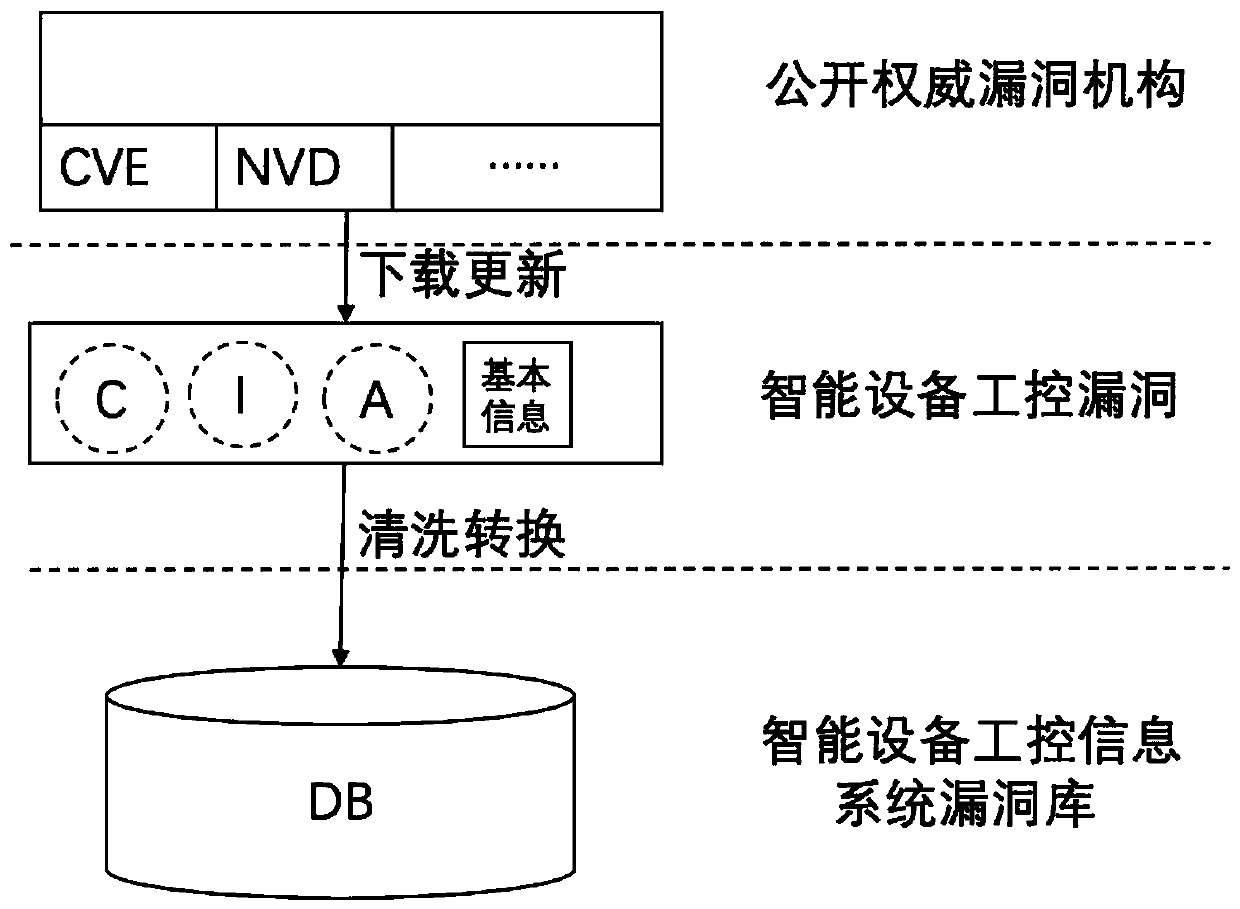
[0036] Use the industrial control system vulnerability scanning tool to scan the industrial control system vulnerabilities of a smart device and perform the following operations:
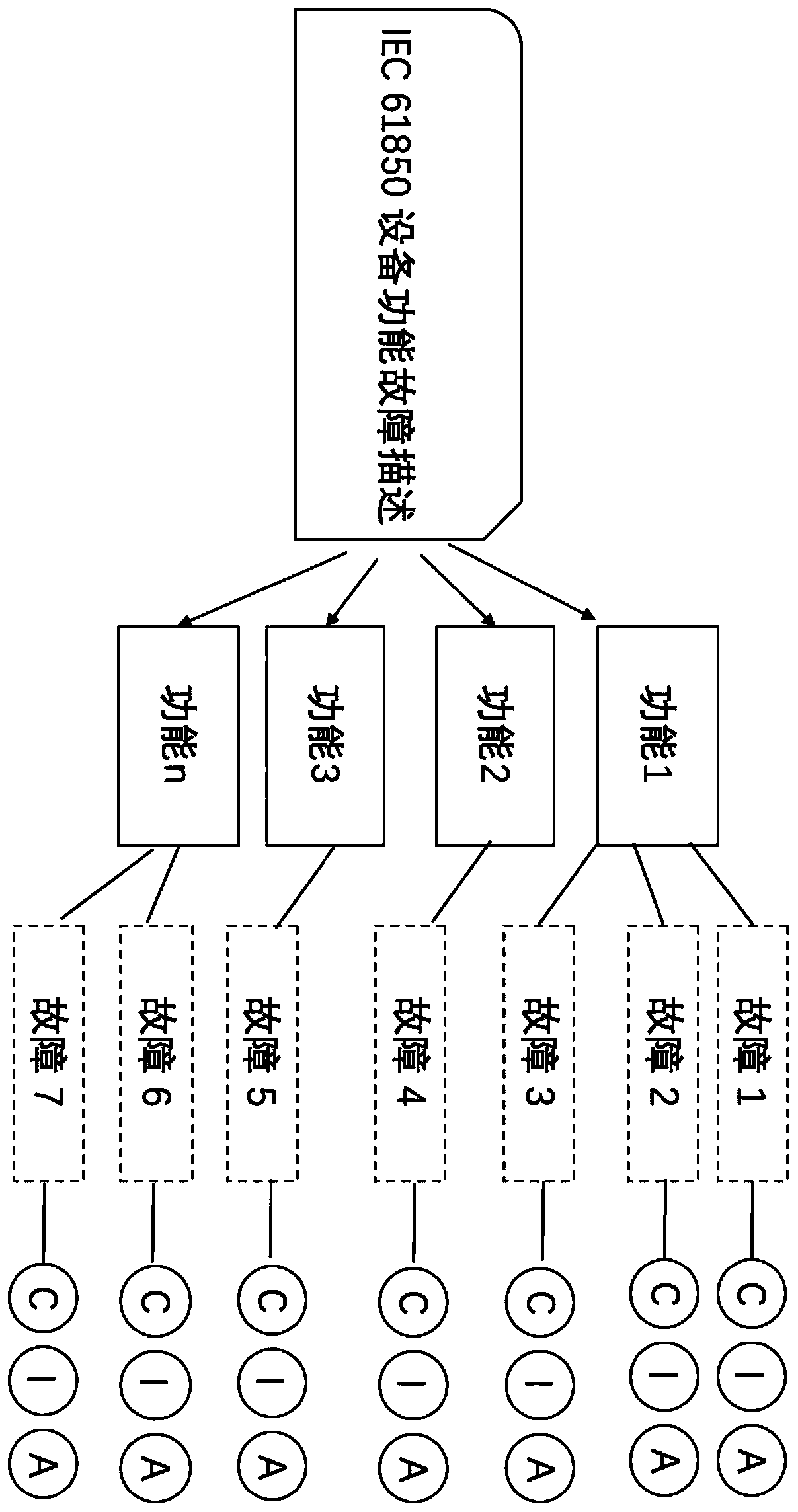
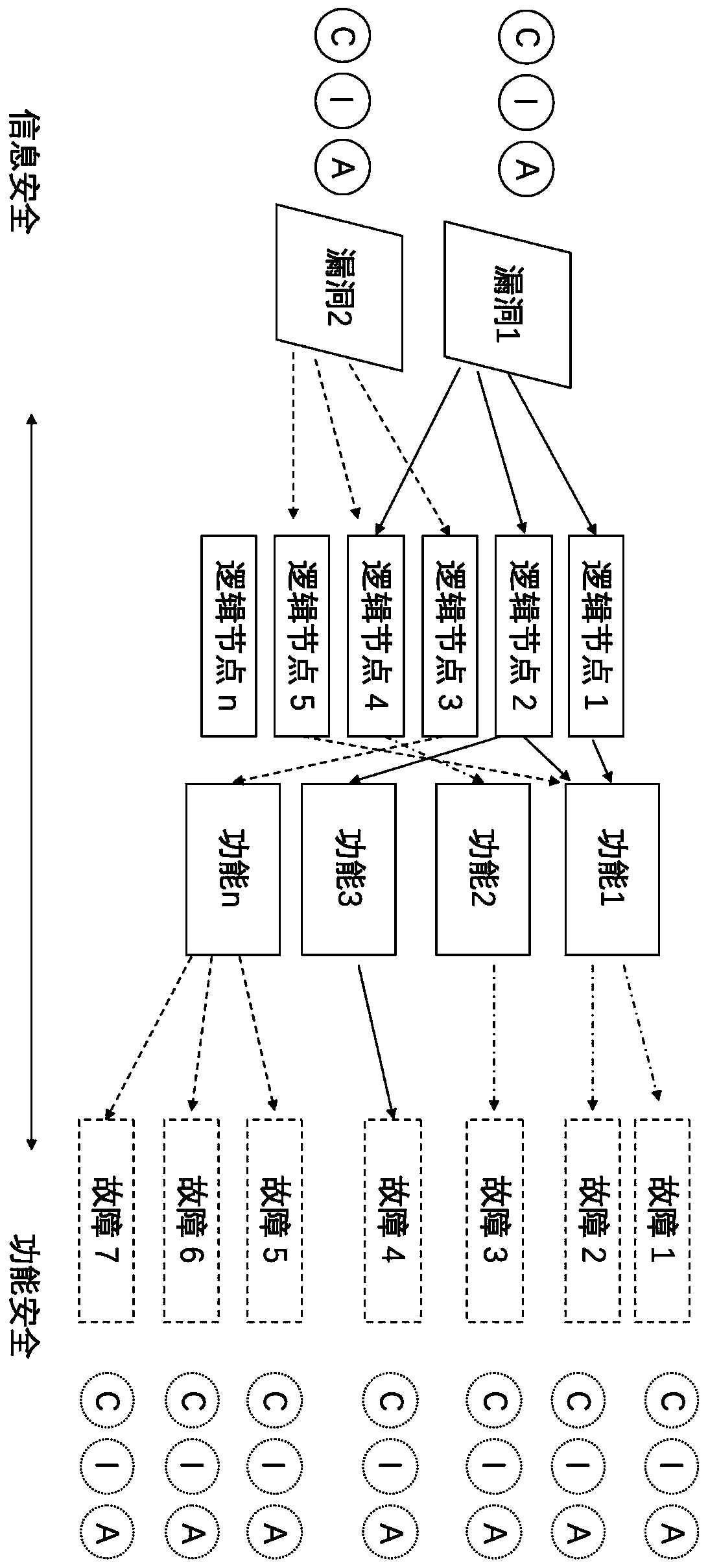
[0037] (1) According to the data generated by the information system where the vulnerability is located, map to all logical nodes that use the data, and then map the functions corresponding to this part of the logical nodes.
[0038] (2) Find the fault information corresponding to the function mapped in (1) and its CIA value from the functional fault CIA information database.
[0039] (3) Calculate the vector distance from the vulnerability CIA value to the fault information CIA value obtained in (2) by Euclidean distance.
[0040] (4) Select the shortest set of vectors in (3) as the association between vulnerabilities and faults.
[0041] In this way, the functional failures that may be caused by system vulnerabilities and the confidentiality threat value (C value), integrity threat value (I value...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com