TLS secure communication method and system
A technology of secure communication and counterparty, which is applied in the field of information communication security, can solve problems such as potential safety hazards, and achieve the effect of enhancing security and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
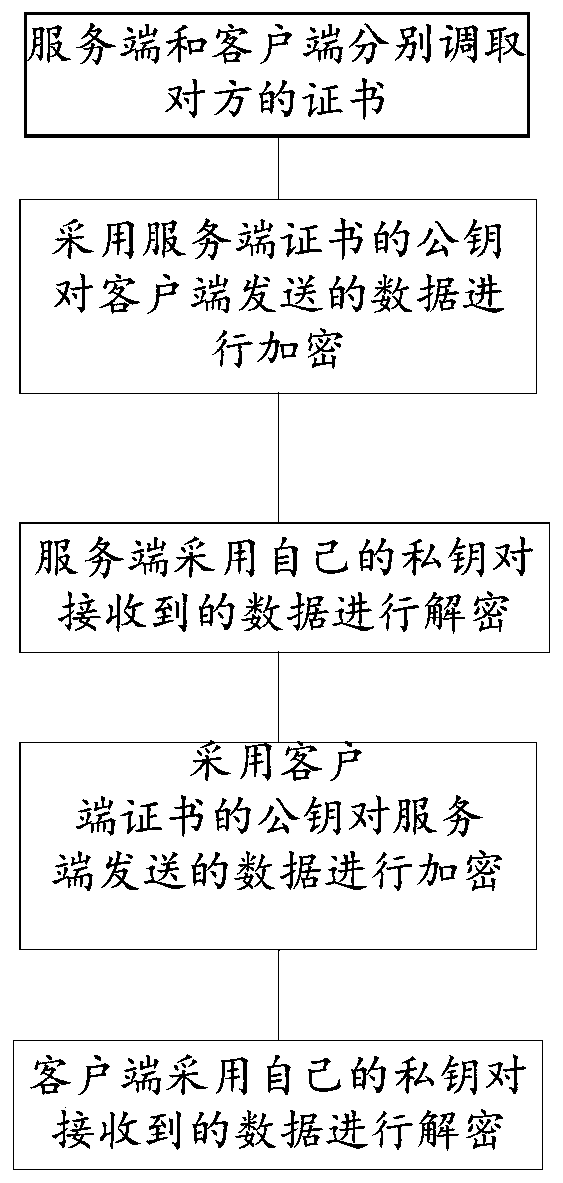
[0035] In one or more implementations, a method for TLS secure communication is disclosed, such as figure 1 shown, including the following process:
[0036] (1) When using it for the first time, exchange the certificates of the server and the client through pre-installed certificates and other means in advance; before communicating with the two parties, first connect to the public cloud server to obtain the certificate (or key) of the other party, and then use the certificate ( key) to communicate with the other party. The certificate contains the public key of the certificate holder. The public key is not afraid of being leaked, and can make the other party confirm that the certificate really belongs to the holder rather than being impersonated.
[0037] Of course, the key exchange can also be realized by manually generating the key by the administrator and then notifying the communicating parties by telephone, email or manual delivery.
[0038] (2) All SSL / TLS plaintext da...
Embodiment 2
[0048] In one or more embodiments, a client is disclosed, which adopts the TLS secure communication method in Embodiment 1, and the client is configured to:
[0049] Get the certificate of the server;
[0050] Use the public key of the server certificate to encrypt the cipher suite and key exchange information and send them to the server;
[0051] Use your own private key to decrypt the received encryption suite selection and key exchange information from the server.
[0052] In other embodiments, a server is disclosed, which adopts the TLS secure communication method in Embodiment 1, and the server is configured as:
[0053] Get the client's certificate;
[0054] Use the public key of the client certificate to encrypt the encryption suite selection and key exchange information and send it to the client;
[0055] For the received client cipher suite and key exchange information, use your own private key to decrypt it.
Embodiment 3
[0057] In one or more implementations, a TLS secure communication system is disclosed, including: a client and a server, wherein,
[0058] The server and the client retrieve the certificates of each other respectively;
[0059] The client and the server respectively use the public key in the other party's certificate to encrypt the information to be sent to the other party;
[0060] Both the client and the server use their own private keys to decrypt the received information sent by the other party to achieve secure data transmission.
[0061] For the specific working mode of the above system, refer to the method disclosed in Embodiment 1, which will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com