Intelligent contract security detection method based on oracle machine
A smart contract, security detection technology, applied in error detection/correction, redundant code for error detection, response to error generation, etc., to reduce storage space occupation, improve efficiency, and reduce memory storage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
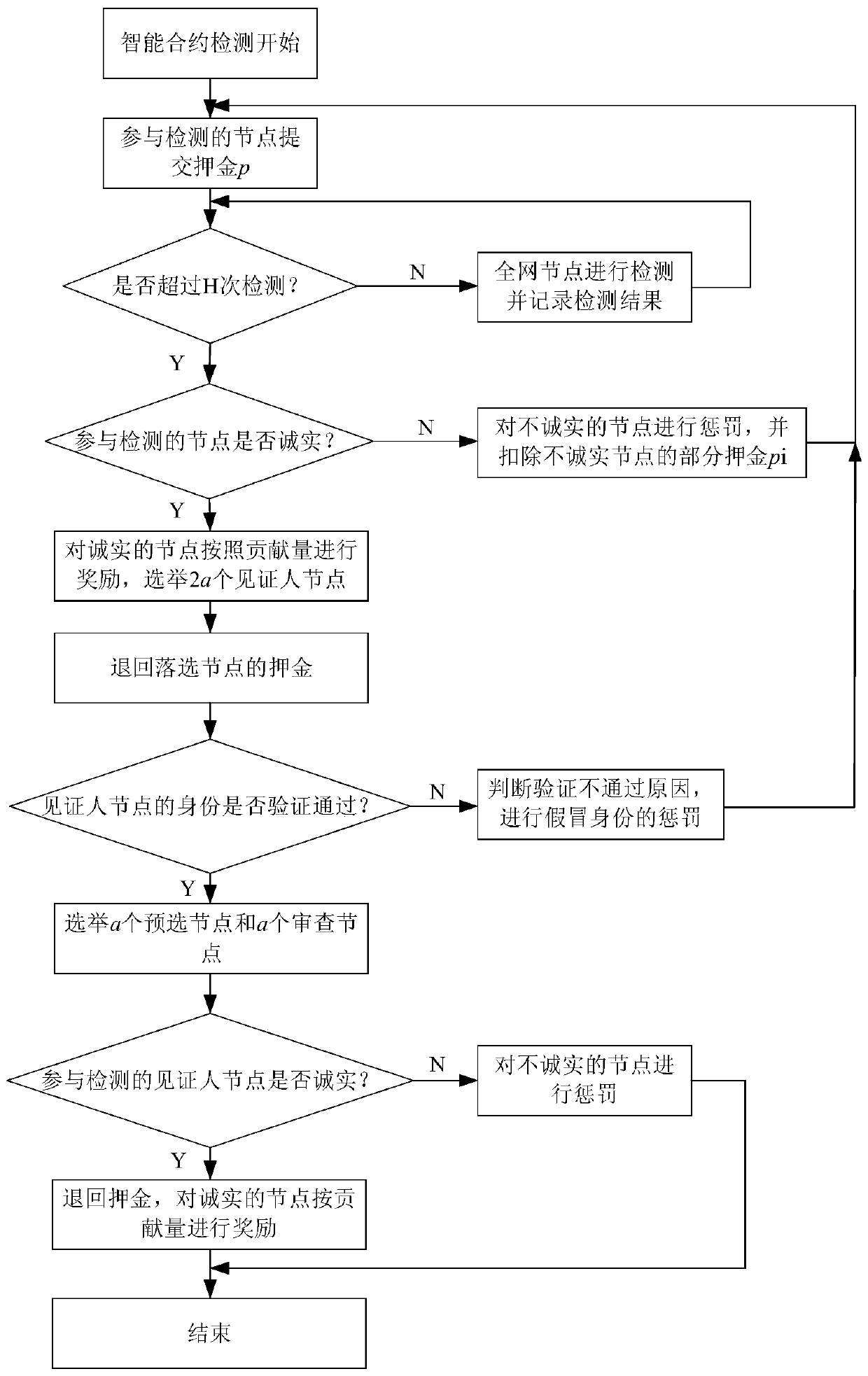
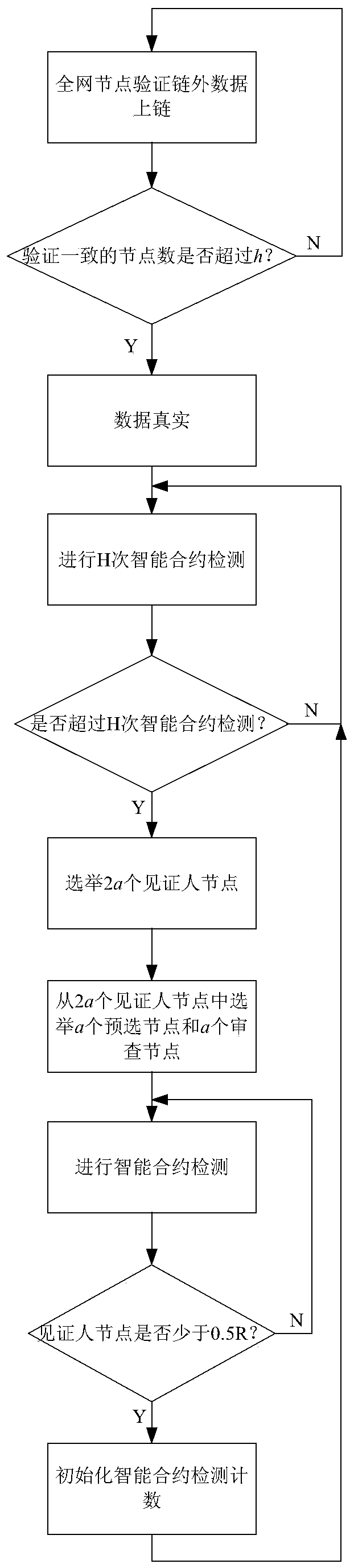
[0057] 3. The process diagram of the oracle machine performing smart contract security detection is as follows image 3 shown. An implementation of an oracle-based smart contract security detection method in the above scheme is as follows: the review and election mechanism includes: N nodes in the entire network (N≥n) verify the off-chain data and upload the data to the chain. (0.5N1 , the pre-selected nodes whose reports are true will be rewarded. When the witness node is less than 0.5R, restart H times of smart contract detection on the whole network, and recalculate the smart contract detection ability of the node again, and the nodes that made outstanding contributions in the last round of detection (such as the top 10%, according to the requirements settings), the contribution can be retained (this helps to adapt to network dynamics).
specific Embodiment 2
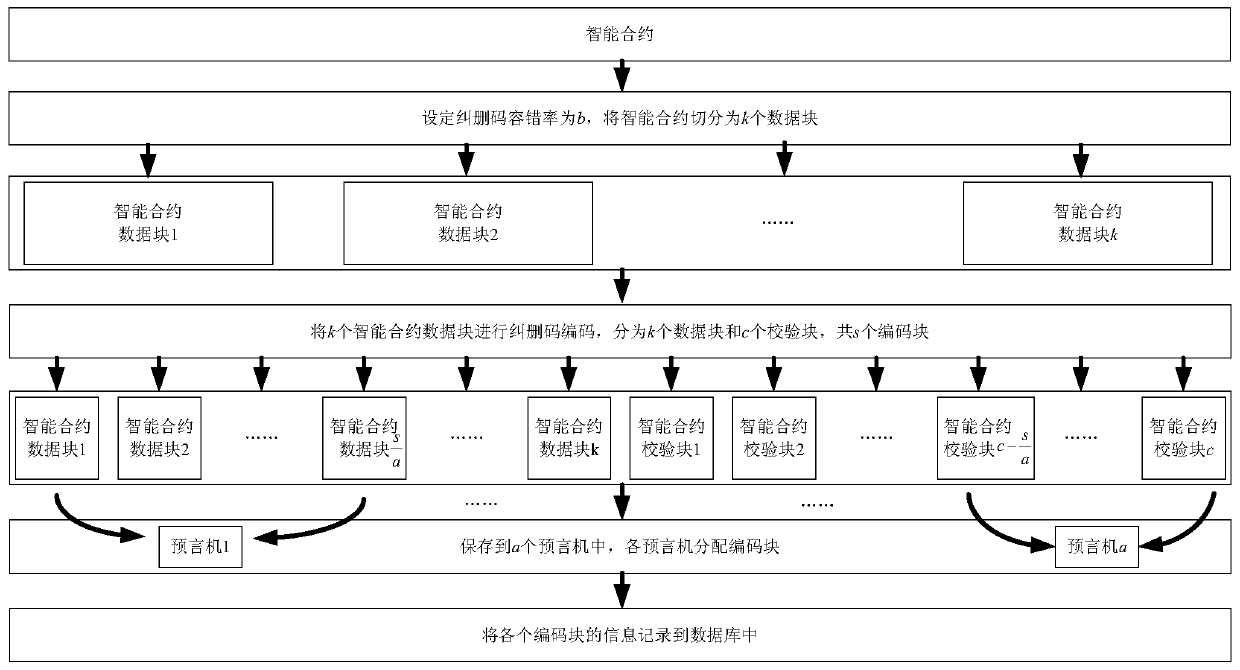
[0059] 4. (t, a) The principle flow chart of smart contract security detection threshold setting is as follows: Figure 4 shown. The number of smart contract coding blocks that have reached or exceeded the consensus vote of t, the oracle machine has passed the test, and the entire smart contract is proved to be safe, or the code of the smart contract that has been found to be wrong is modified so that the smart contract as a whole reaches the number of t consensus votes, Where t is the threshold value (0.5n<t≤N) that must be met for the smart contract to be executed safely, and the number of oracles is set as a. Multiple models are more complex and costly than single models, but have higher security guarantees.
[0060] For example, if the data of a oracle is set as a credible threshold, the intelligent oracles with the critical value must agree on the result, and the review node uses The oracle model of , only when a oracle is not less than The contract can only be execu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com