Supervisable blockchain construction method based on group signature
A construction method and blockchain technology, applied in encryption devices with shift registers/memory, transmission systems, instruments, etc., can solve problems such as difficult supervision of blockchain transactions, to ensure security and prevent double spending Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
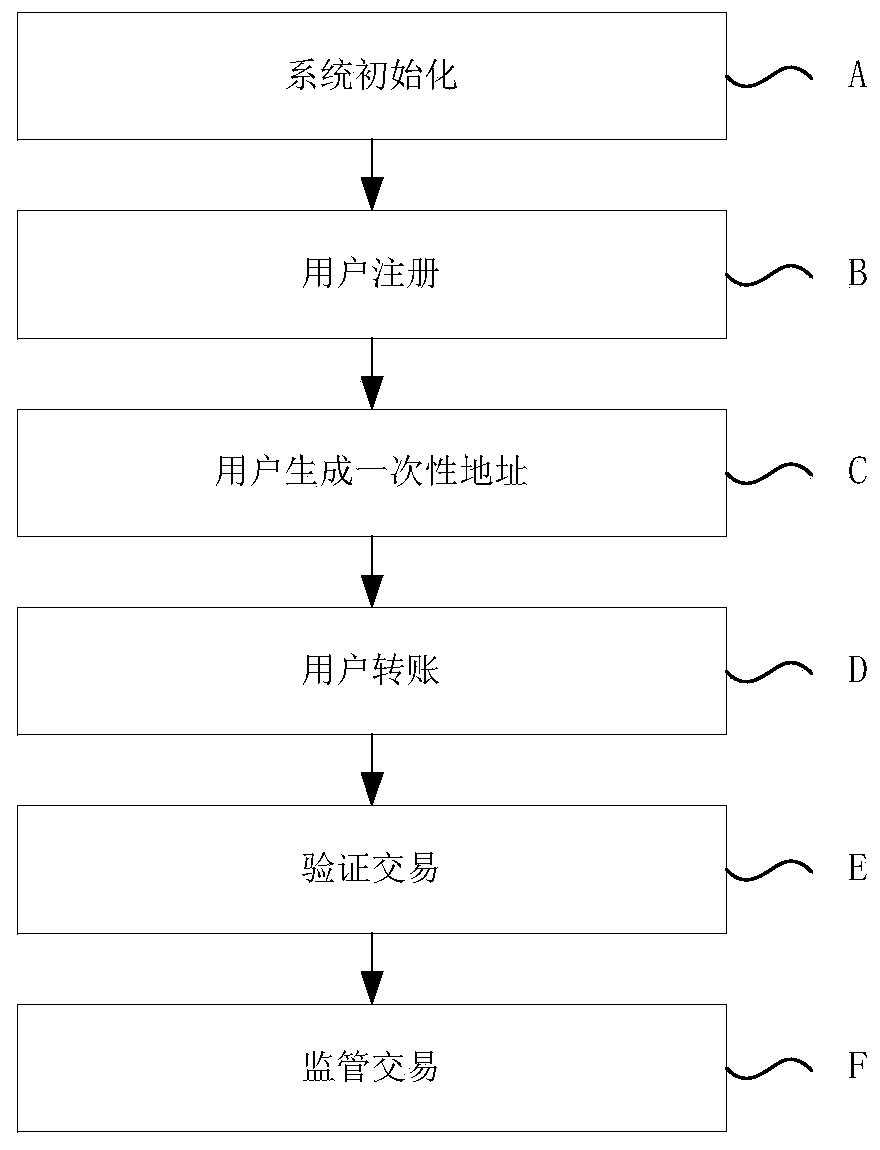
[0062] The central bank provides a group signature server, which is maintained by the group administrator GM. Central bank users use the central bank’s blockchain, and the number of users changes dynamically. For example, at a certain moment nu=10000, the central bank deploys 100 verification nodes, so nn=100. The following is blockchain user DU i 、DU j and verification node VN v To illustrate this embodiment.
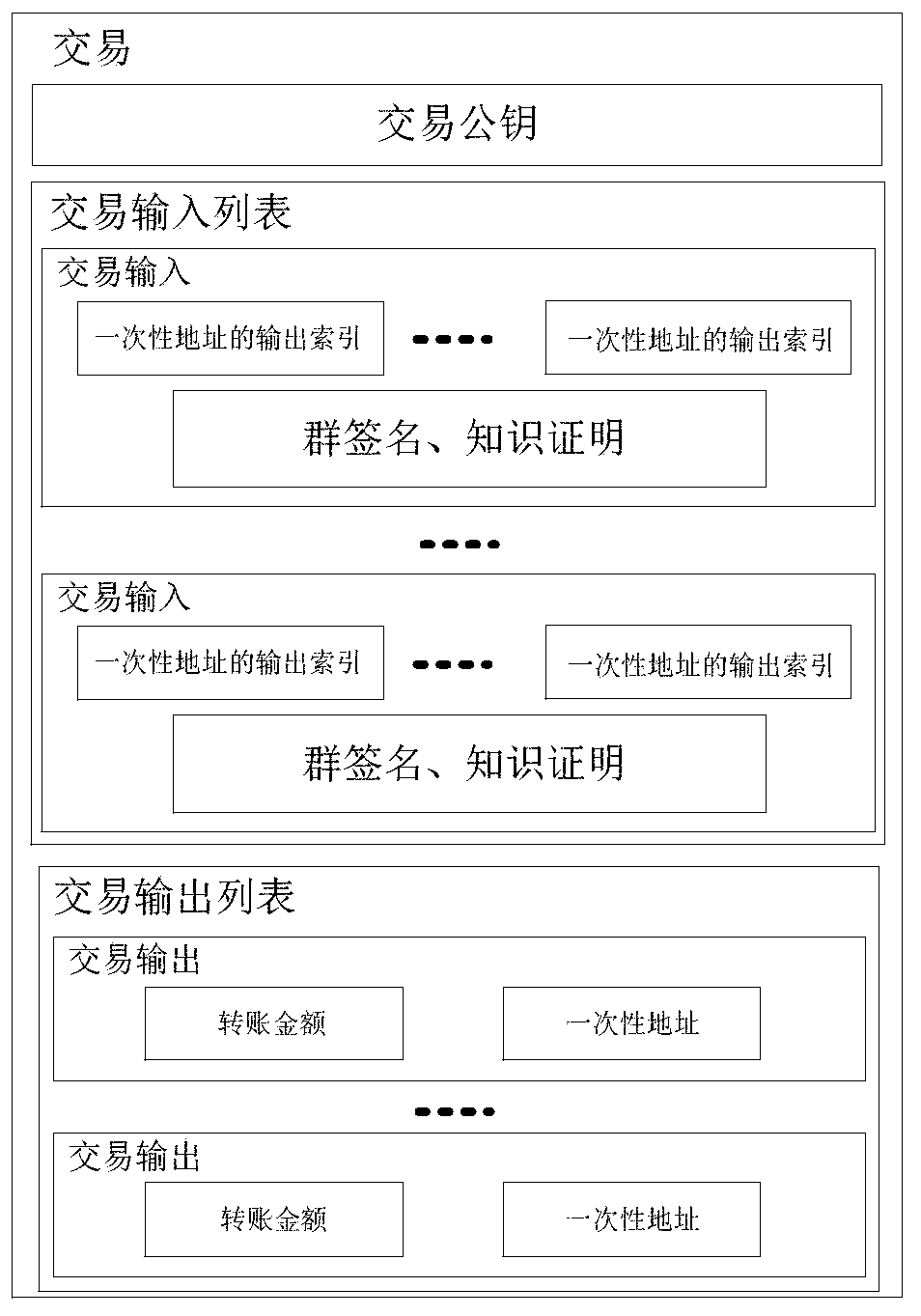
[0063] A) System initialization. GM selects the d224 parameter in the Pairing-Based Cryptography (PBC) library to determine the (G 1 ,G 2 ,e,p), where the prime number p is 15028799613985034465755506450771561352583254744125520639296541195021, and G is randomly selected 1 and G 2 The two elements in as g 1 and g 2 , determine the system parameter para=(G 1 ,G 2 , g 1 , g 2 ,e,p). Afterwards GM from G 1 Randomly select elements h and w from the integer ring Z modulo p p Randomly select a non-zero number ξ from 1 , ξ 2 and λ, calculate G 1 The two eleme...
Embodiment 2
[0095] Embodiment 2 is basically the same as Embodiment 1, except that the blockchain system adds a user registration center and a transaction supervision center. Wherein, the user registration is provided by the user registration center, and the supervision transaction is provided by the transaction supervision center.
[0096] Group private key (ξ 1 ,ξ 2 ,λ) is divided into two parts: the user registration center holds λ, and the transaction supervision center holds ξ 1 and ξ 2 . Members in possession of any part of the group private key's parameters must encrypt the parameters for storing said group private key.
Embodiment 3
[0098] Embodiment 3 is basically the same as Embodiment 1, except that the blockchain system uses hash algorithms such as SHA-3 or SM3 as the basic hash function.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com