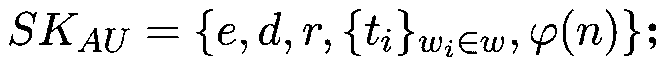Urbanization environment big data public benefit interaction system and method based on artificial intelligence
An artificial intelligence and interactive method technology, applied in the field of management, can solve the problems of volunteers without reliable information sources for public welfare activities, poor accuracy of reference information, and no unified public welfare platform.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
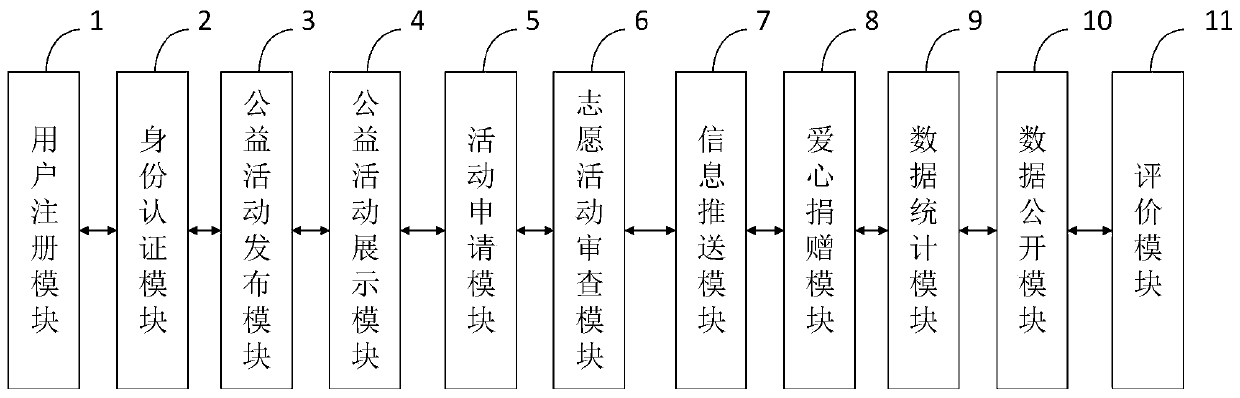
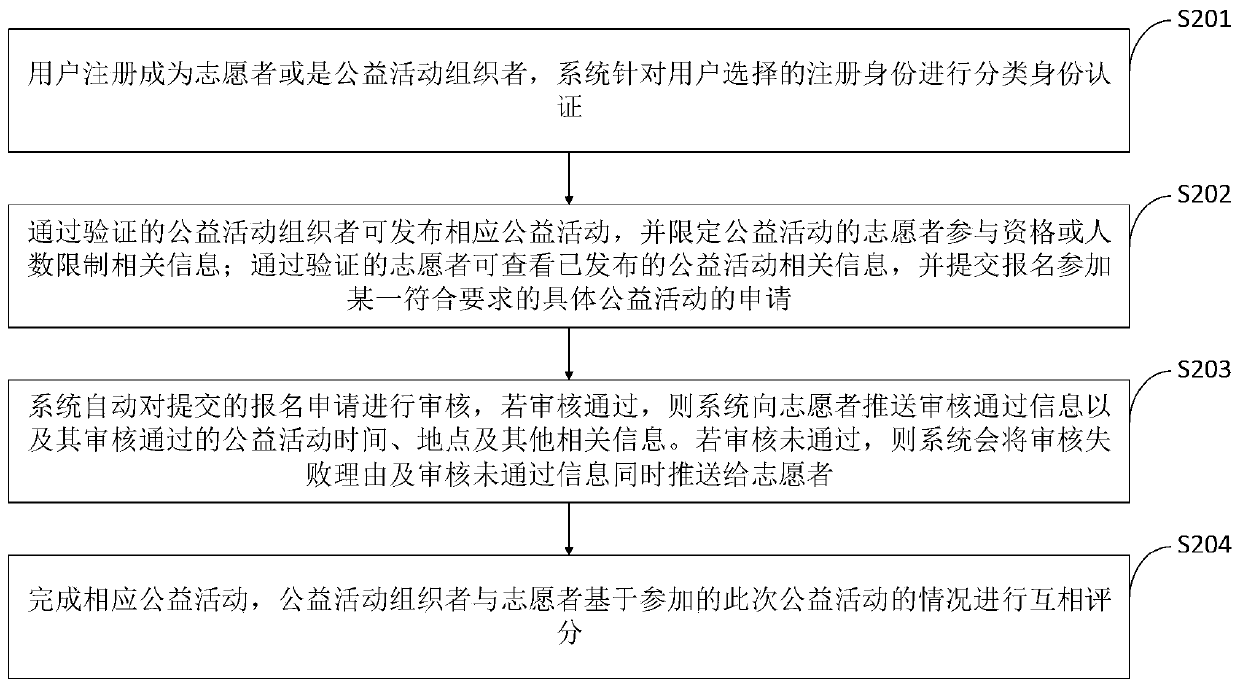
[0102] When the public welfare interaction method based on artificial intelligence urbanization environment big data provided by the embodiment is running, first, the user registers as a volunteer or a public welfare activity organizer through the user registration module 1 . Secondly, the identity authentication module 2 is used to classify and authenticate different types of users. The identity authentication of volunteers includes but is not limited to checking whether they have criminal records, criminal punishment records and corresponding civil punishment records, and whether they have health certificates. The identity authentication of the public welfare activity organizer includes but is not limited to reviewing whether the applicant is the actual manager or manager or staff member of the public welfare place, reviewing whether the user has a criminal record, criminal punishment record and corresponding civil punishment record, and reviewing whether the corresponding beh...
Embodiment 2
[0107] Volunteers or organizers of public welfare activities in the present invention conduct public welfare interactions in the form of online donations or offline donations, specifically including:
[0108] In the first step, the volunteer data processing terminal calculates the hash value h(m) of the data m, where h( ) is a strong hash function in cryptography, and h(m) is used as the key to encrypt the data n. Use h(m) to encrypt data, assuming E is a symmetric key encryption function, the generated ciphertext is E h(m) (m).
[0109] The second step is to encrypt h(m) with the public keys of all online authorized terminals, and the ciphertext is: (C, C'), where C=E h(m) (m), C'=(F PK (h(m)), F is a public key encryption function, and PK is the public key.
[0110] In the third step, the data can only be decrypted by the online authorized terminal. The volunteer data processing terminal first decrypts with its own private key to obtain h(m), and then uses h(m) to restore...
Embodiment 3
[0120] In Embodiment 2 of the present invention, system initialization includes:
[0121] User A and user B are initialized when they log in to the system for the first time.
[0122] After user A and user B complete the initialization, they will log in to the system. The login process is as follows:
[0123] When the user logs in to the system, the mobile APP will automatically obtain the key online donation or offline donation information stored in the third-party storage organization, and obtain the password key through hash calculation of the registration information, and decrypt the encryption through the password key Key information about online donations or offline donation items, after analyzing the information of key online donations or offline donation items, obtain the user master key and user private key respectively, and store the master key and private key in the mobile phone app.
[0124] The initialization process includes:
[0125] In the first step, the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com