Intelligent door lock unlocking system, method and device and medium
A smart door lock and door lock technology, applied to instruments, time registers, individual input port/output port registers, etc., can solve the problem of low security of smart door locks, improve security and reduce duplication Possibility, the effect of increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
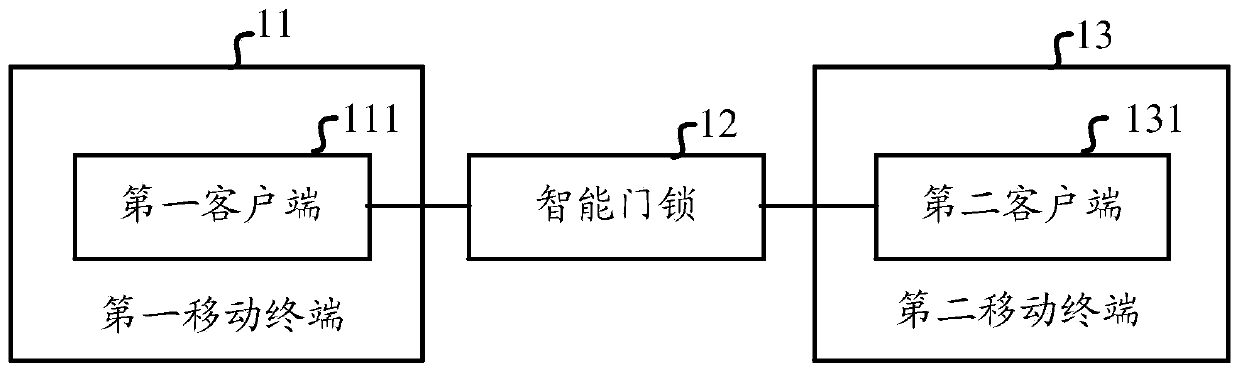
[0117] Embodiment 1 of the present invention provides an intelligent door lock unlocking system. The structural diagram of the system can be as follows figure 1 As shown, including the first mobile terminal 11 and the smart door lock 12, the first mobile terminal 11 uses the bound first client 111 to communicate with the smart door lock 12 through the local area network, and the first mobile terminal 11 and the smart door lock 12 bindings, of which:
[0118] The first client 111 is used to receive and generate an unlock data request in the administrator mode and send it to the smart door lock. The generated unlock data request carries the first terminal identifier of the first mobile terminal and / or the ID of at least one second mobile terminal. Second terminal identification;
[0119] The smart door lock 12 is used to generate a data packet corresponding to the first terminal identification and / or a data packet corresponding to each second terminal identification according t...
Embodiment 2
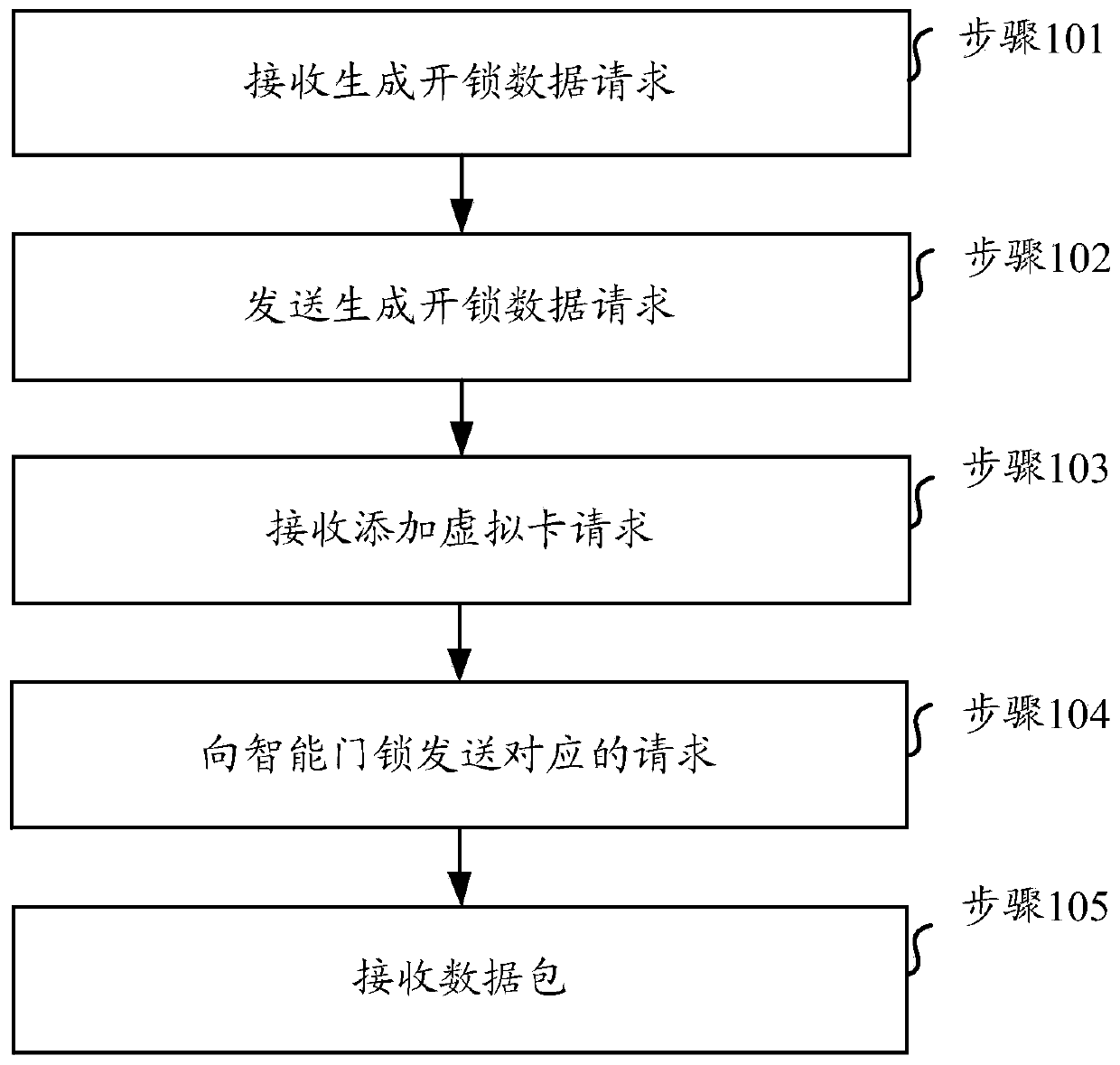
[0148] Embodiment 2 of the present invention provides a method for unlocking a smart door lock. The method is applied to a first client bound to a first mobile terminal. The first client communicates with the smart door lock through a local area network, and the first mobile terminal communicates with the Smart door lock binding, the steps of the method can be as follows figure 2 shown, including:
[0149] Step 101, receiving a request to generate unlock data.
[0150] In this step, the first client may receive a request for generating unlock data sent by the user in the administrator mode. The request for generating unlock data may carry the first terminal identifier of the first mobile terminal and / or the second terminal identifier of at least one second mobile terminal.
[0151] Step 102, sending a request for generating unlock data.
[0152] In this step, the first client may send a request to generate unlock data to the smart door lock, so that in the administrator mo...
Embodiment 3
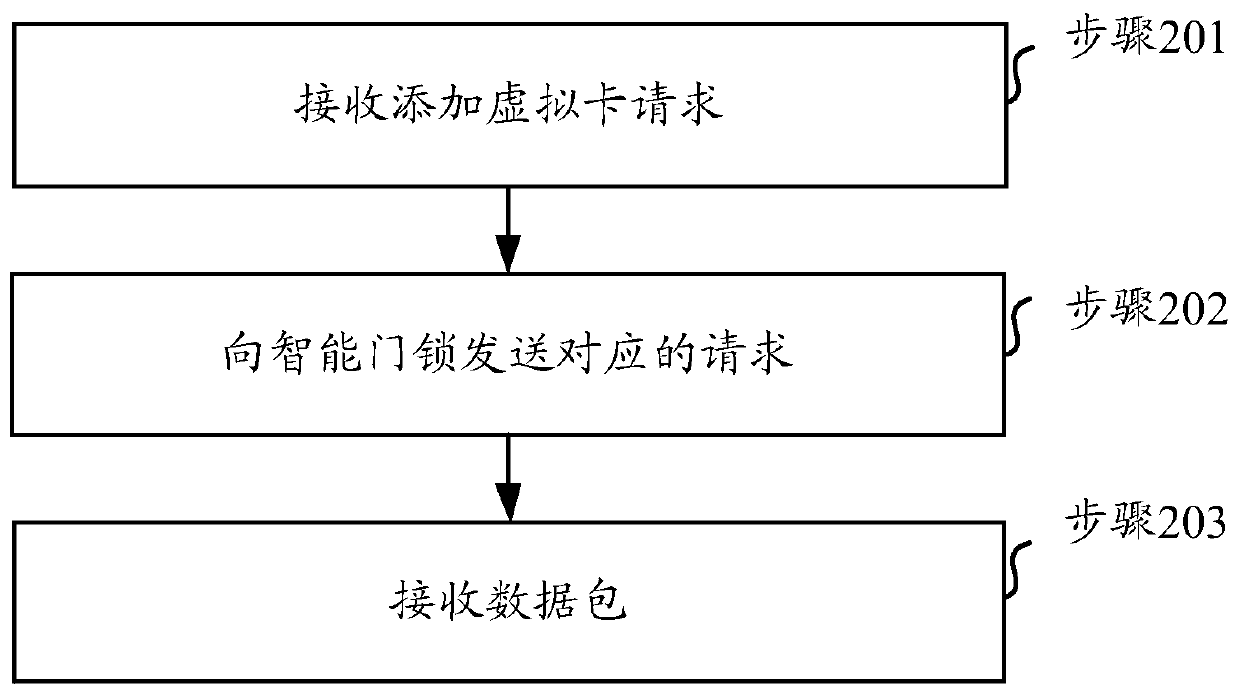
[0170] Embodiment 3 of the present invention provides a method for unlocking a smart door lock. The method is applied to a second client bound to a second mobile terminal. The second client communicates with the smart door lock through a local area network. The steps of the method can be Such as image 3 shown, including:
[0171] Step 201, receiving a request to add a virtual card.
[0172] In this step, the second client may receive a request for adding a virtual card sent by the user. At this point, the second client may be in a non-administrator mode.
[0173] Step 202, sending a corresponding request to the smart door lock.
[0174] In this step, the second client may send a corresponding virtual card addition request to the smart door lock according to the received virtual card addition request, and the corresponding virtual card addition request carries the second terminal identifier of the second mobile terminal.
[0175] Step 203, receiving the data packet.
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com