A Hardware Trojan Detection Method Based on Lifting Algorithm
A hardware Trojan detection and algorithm technology, applied in the direction of internal/peripheral computer component protection, can solve the problems of infrequent use, multi-investment, time-consuming detection, limitations, etc., to reduce classification error rate, improve fault detection efficiency, and process simple effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The present invention will be further described below with reference to the accompanying drawings and embodiments.
[0070] like Figure 4 As shown, an embodiment of the implementation of the complete method according to the content of the present invention is as follows:
[0071] Download the following 37 integrated circuit layout files containing hardware Trojan tags from the public homepage of the github website, import them into the Xilinx ISE development environment, synthesize, implement, and get their NP (number of original gates) NA (number of AND gates) and NO ( or number of gates).
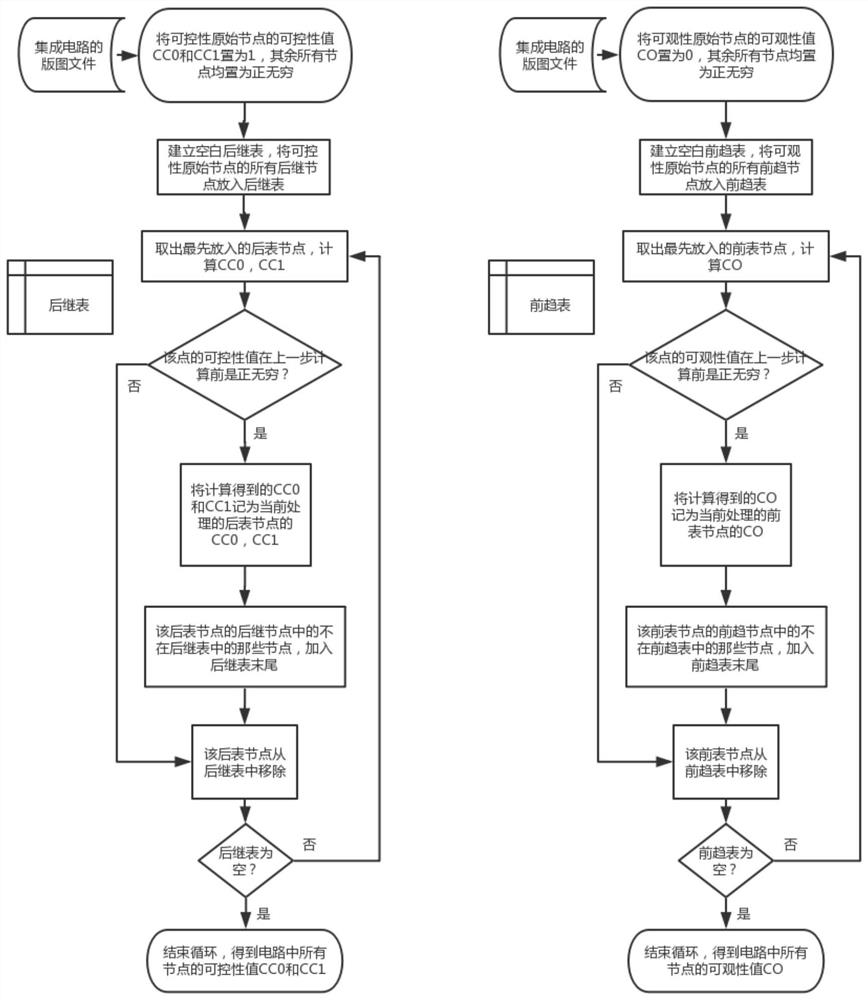
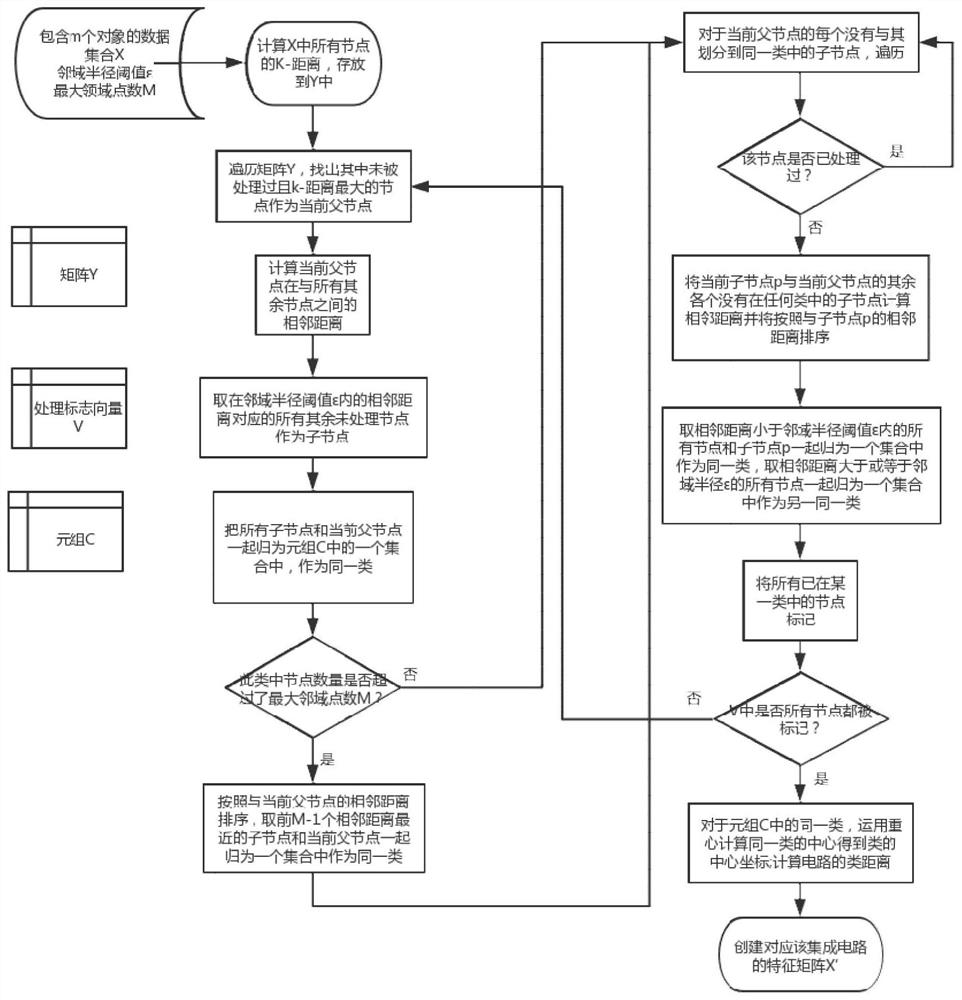
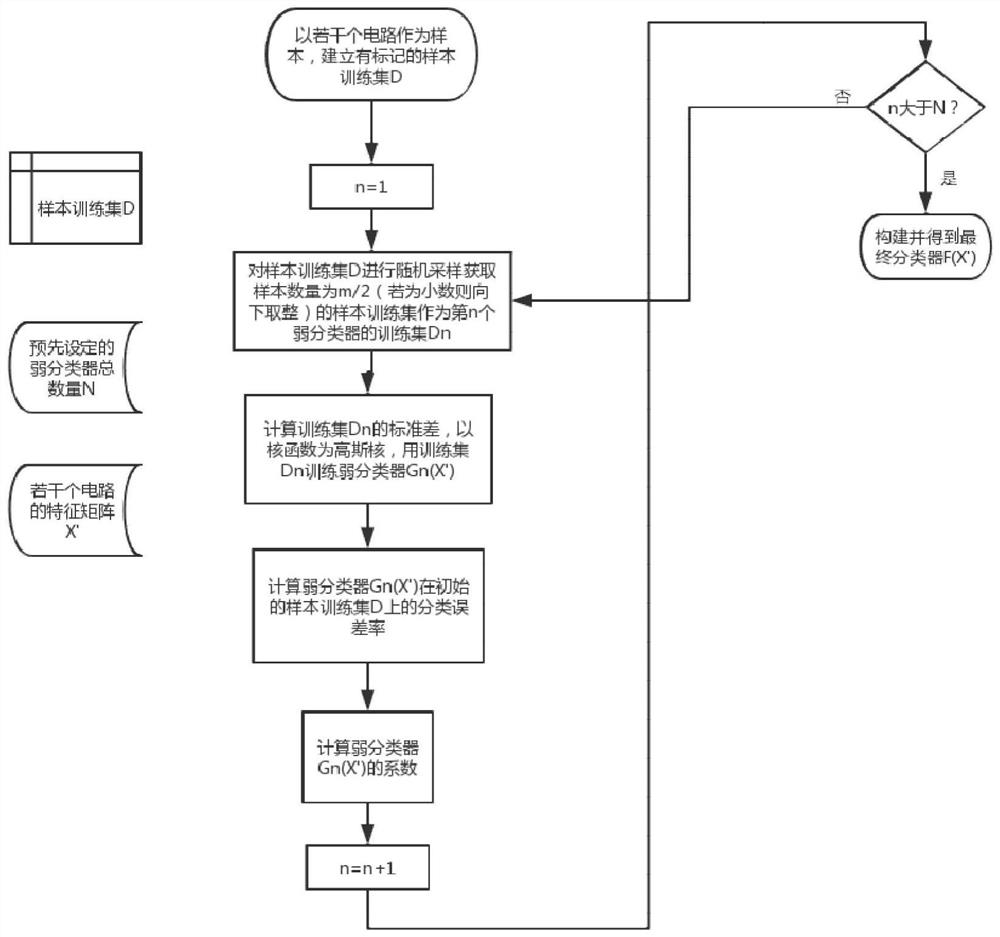
[0072] Using the results of the present invention, such as figure 1 As shown in the process, the first and second controllability values and observability values of all nodes in each circuit are calculated in the matlab software, and are calculated as follows figure 2 The shown process performs cluster analysis on each circuit to obtain the feature matrix X' of each circui...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com