Configuration file monitoring method of server
A configuration file and server technology, applied in the computer field, can solve problems affecting the BMC startup process, achieve the effect of reducing maintenance time, reducing maintenance costs, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
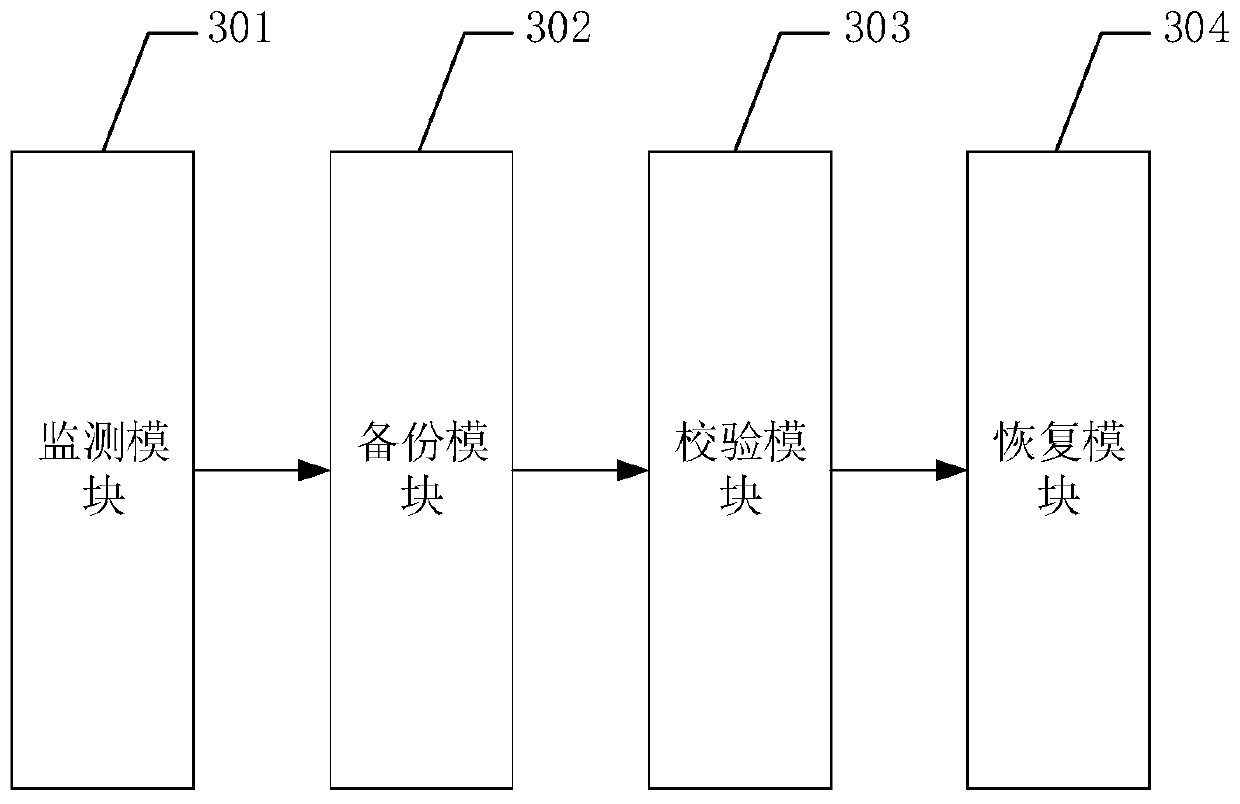
Image
Examples
Embodiment 1
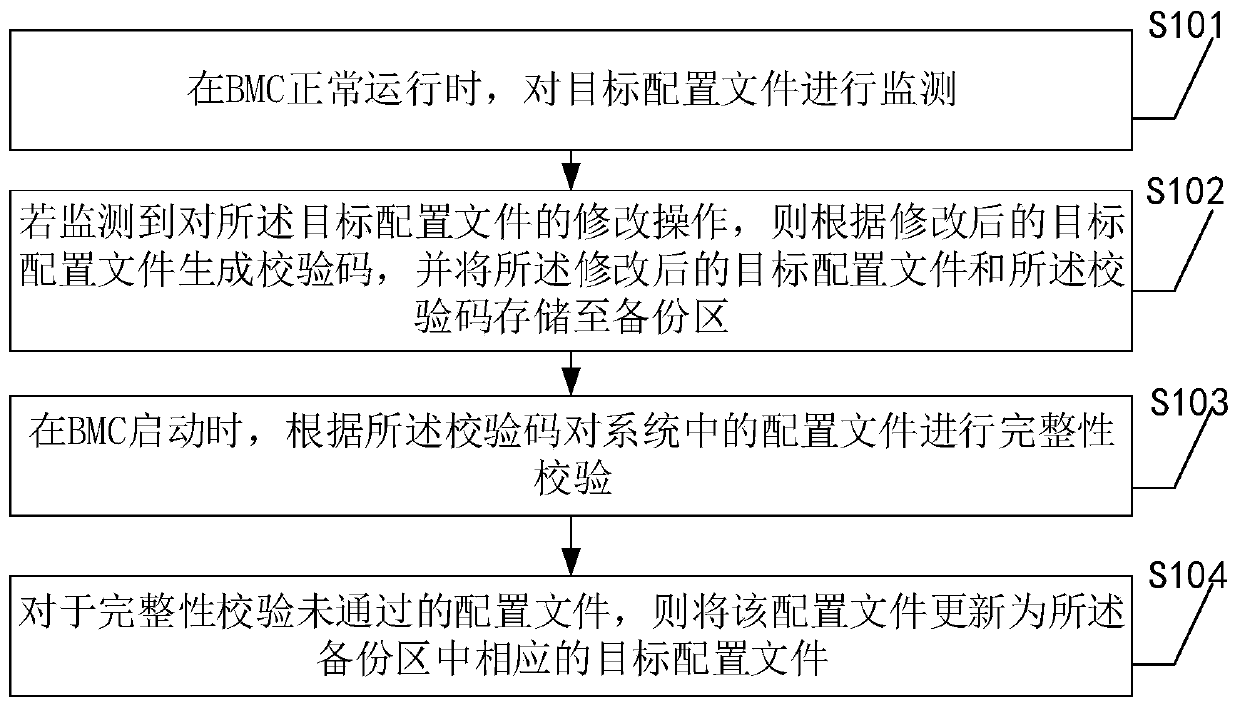
[0043] The following introduces Embodiment 1 of a server configuration file monitoring method provided by the present application, see figure 1 , embodiment one includes:
[0044] S101. When the BMC is running normally, monitor the target configuration file;
[0045] S102. If a modification operation to the target configuration file is detected, generate a check code according to the modified target configuration file, and store the modified target configuration file and the check code in a backup area;
[0046] S103. When the BMC starts, perform integrity check on the configuration file in the system according to the check code;
[0047] S104. For a configuration file that fails the integrity check, update the configuration file to a corresponding target configuration file in the backup area.
[0048] The BMC includes multiple configuration files, and the above target configuration file may be any one or more of the multiple configuration files. According to past experienc...
Embodiment 2
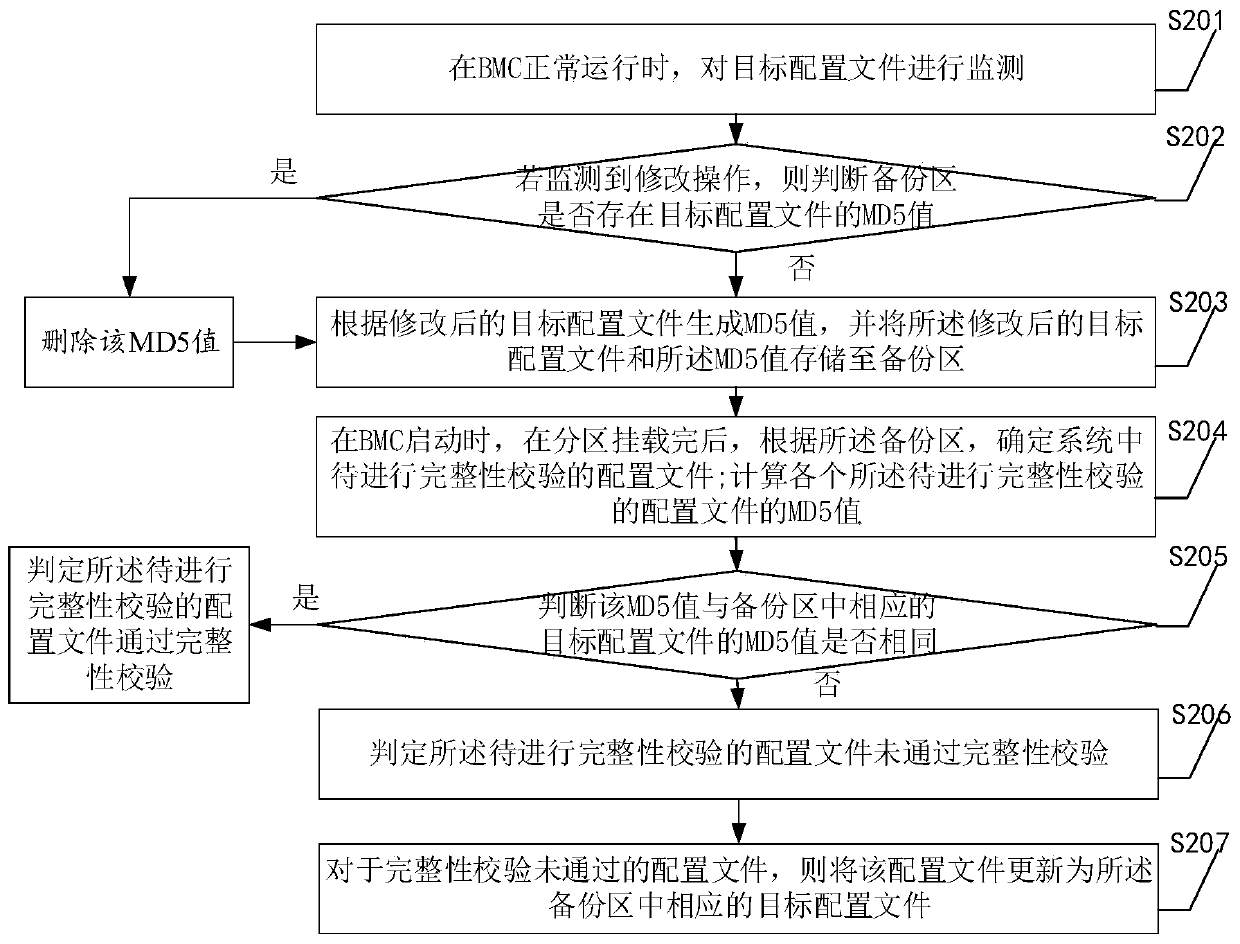
[0054] see figure 2 , embodiment two specifically includes:
[0055] S201. When the BMC is running normally, monitor the target configuration file;
[0056] The above-mentioned monitoring manner may be specifically monitoring the folder where the target configuration file is located, or may be monitoring a modification interface used to modify the target configuration file.
[0057] S202. If a modification operation to the target configuration file is detected, determine the file name and path of the target configuration file, and determine whether the MD5 value of the target configuration file exists in the backup area; if it exists, delete the MD5 value and jump to Go to S203, otherwise skip directly to S203;
[0058] S203. Generate an MD5 value according to the modified target configuration file, and store the modified target configuration file and the MD5 value in a backup area;
[0059] Specifically, this embodiment can be implemented by monitoring threads and verific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com