Image encryption method based on L-F cascade chaos and 3D bit scrambling
An encryption method and 3D technology, applied in image coding, image data processing, computer security devices, etc., can solve the problems of weak anti-noise and selected plaintext attack ability, bit scrambling, etc., so as to improve anti-noise attack ability and improve randomness. performance, improve the effect of plaintext sensitivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings, but it is not limited thereto. Any modification or equivalent replacement of the technical solution of the present invention without departing from the spirit and scope of the technical solution of the present invention should be covered by the present invention. within the scope of protection.
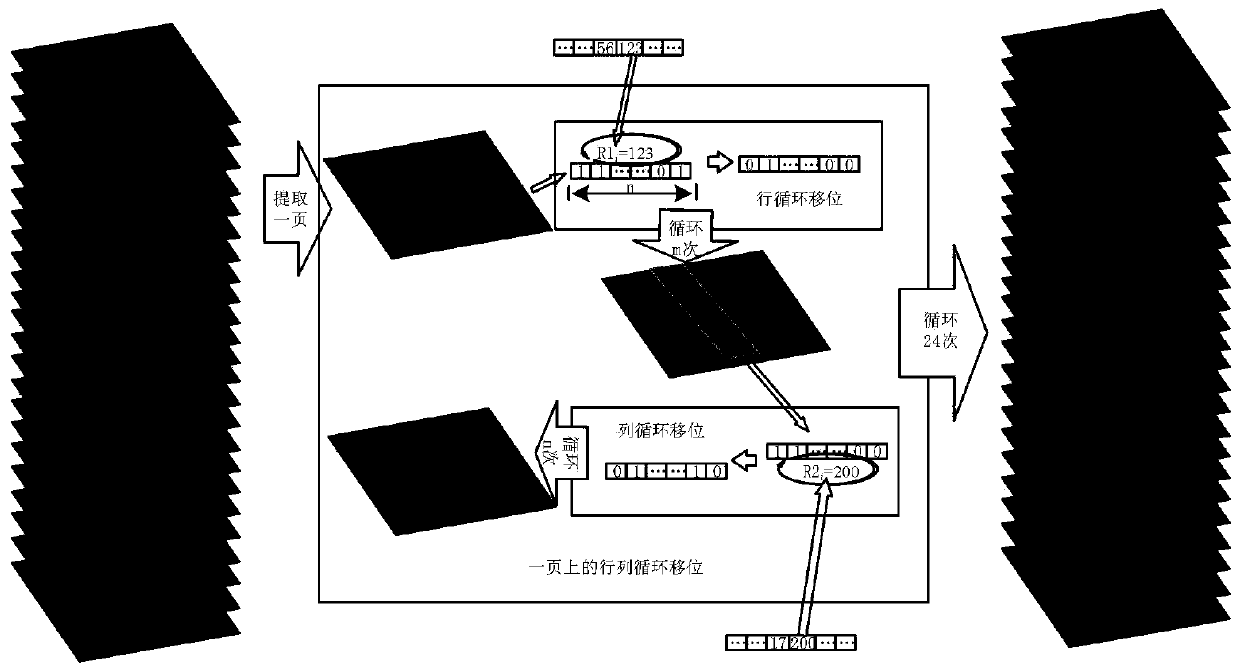
[0042] The present invention provides a kind of image encryption method based on L-F cascade chaos and 3D bit scrambling, and described method comprises the following contents:
[0043] 1. Encryption principle
[0044] The main core content of encryption in the present invention has three parts: (1) L-F cascade chaos, (2) key generation, (3) 3D bit scrambling. The three principles are introduced below:
[0045] 1. L-F cascading chaos
[0046] Logistic chaotic map is simple in expression, easy to realize, and has good randomness, so it is widely used ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com