Android malicious application detection method fusing multi-feature classification
A malicious application and detection method technology, applied in the direction of computer security devices, instruments, platform integrity maintenance, etc., can solve the problems of high cost, low efficiency, and inability to simulate the real and brisk simulation of the program, so as to reduce the amount of calculation and improve the detection efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
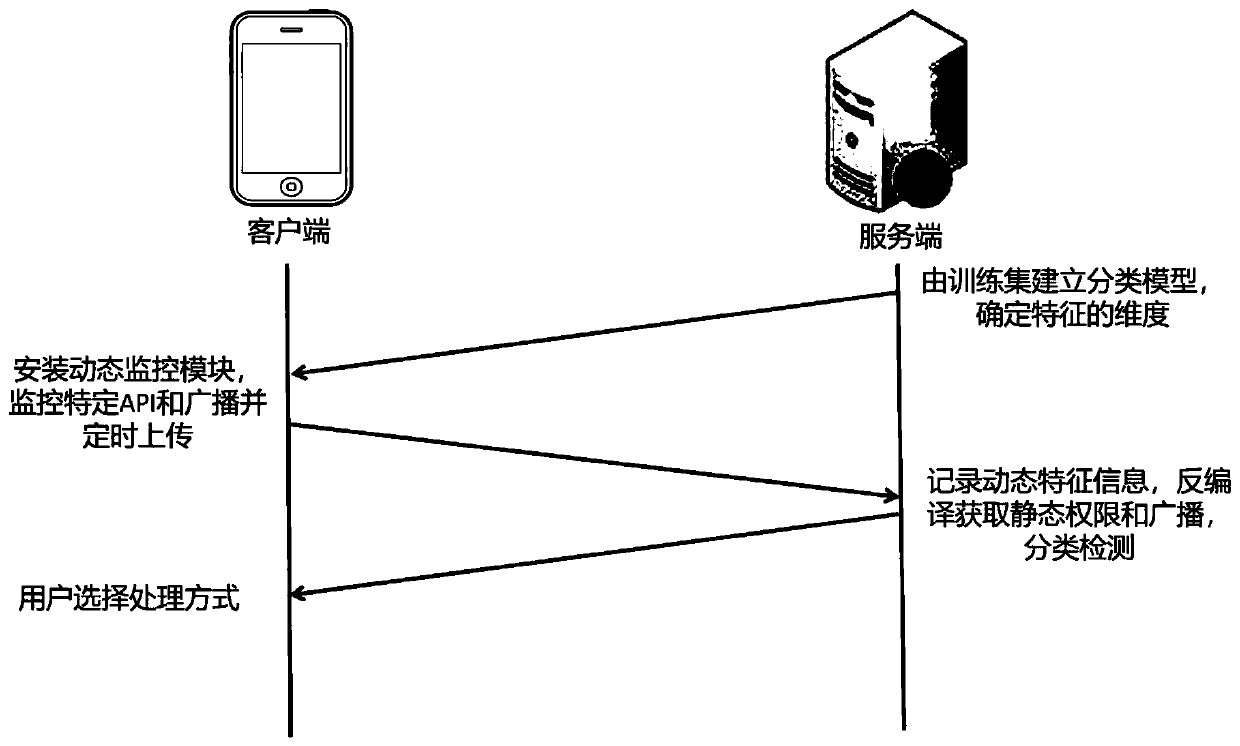
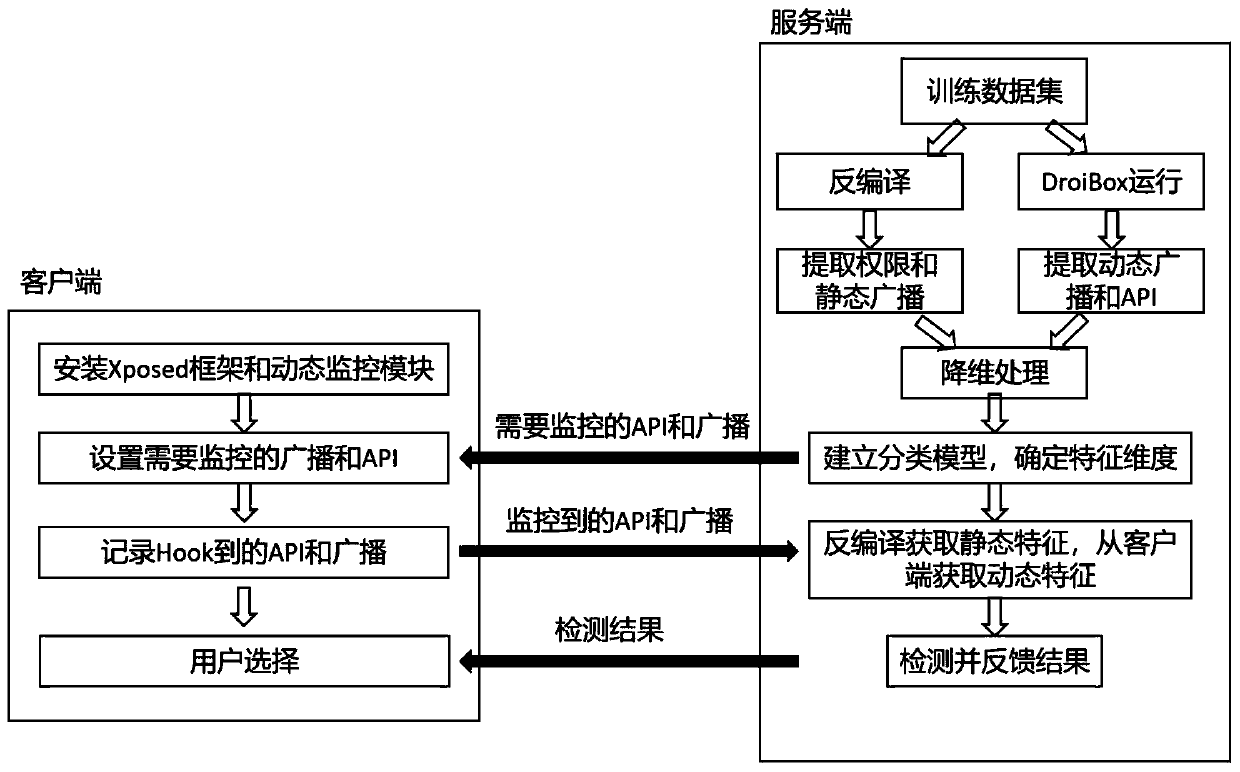
[0036] The Android malicious application detection method based on the broadcast mechanism of the present invention is schematically shown as figure 1 As shown, the Android malicious application detection method that integrates multi-feature classification, the specific steps are as follows:
[0037] Step 1: The client installs the dynamic monitoring module.
[0038] (1) After installing the Xposed framework on the mobile terminal, the user downloads and installs the client dynamic monitoring module.
[0039] (2) Select the application program to be monitored, and send the program APK to the server.
[0040] Step 2: The server establishes a classification model.
[0041] (1) The server first collects normal and malicious applications as training set samples, decompiles APK to extract all permissions and static broadcast features, and runs th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com