Secure Network Connection Restoration
A network and network node technology, applied in the field of connection restoration, can solve problems that cannot completely solve privacy and security issues, and achieve the effect of preventing security and privacy issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
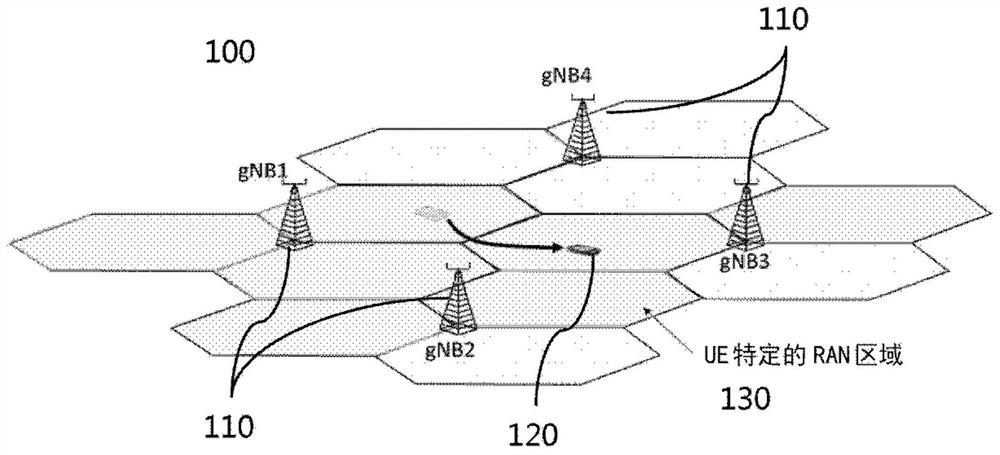
[0088]An important feature of LTE Light Connect and RRC_INACTIVE is the ability of the RAN to reach the UE by initiating RAN paging within a configured "RAN Notification Area". Such RAN areas are configured as a list of cells associated with one or more nodes (eNB / gNB). figure 1 An exemplary communication network 100 is shown having a plurality of network nodes 110 (also referred to as gNB1 to gNB4 ), a user equipment (UE) 120 and a RAN area 130 . The UE 120 is configured with a RAN area 130 consisting of all cells associated with gNB1 and a subset of cells associated with gNB2 and gNB3. A UE can freely move between cells inside the configured RAN area 130 while in RRC_INACTIVE.
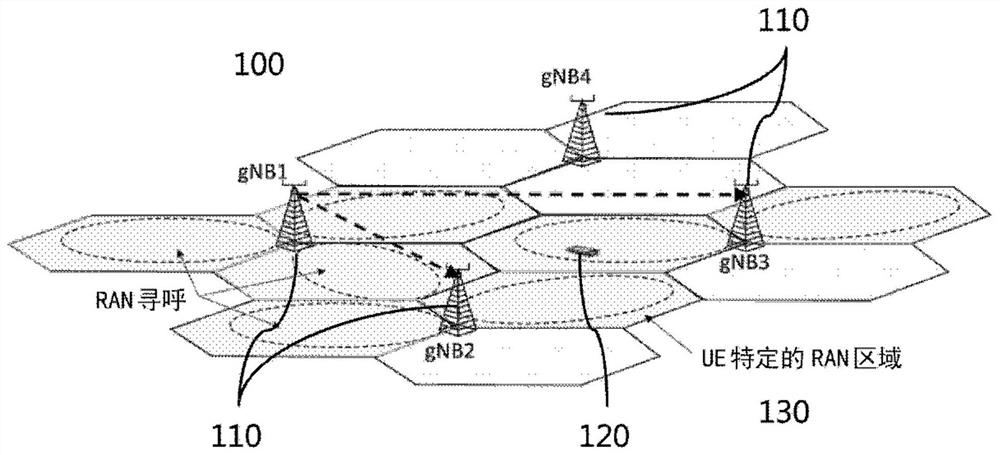
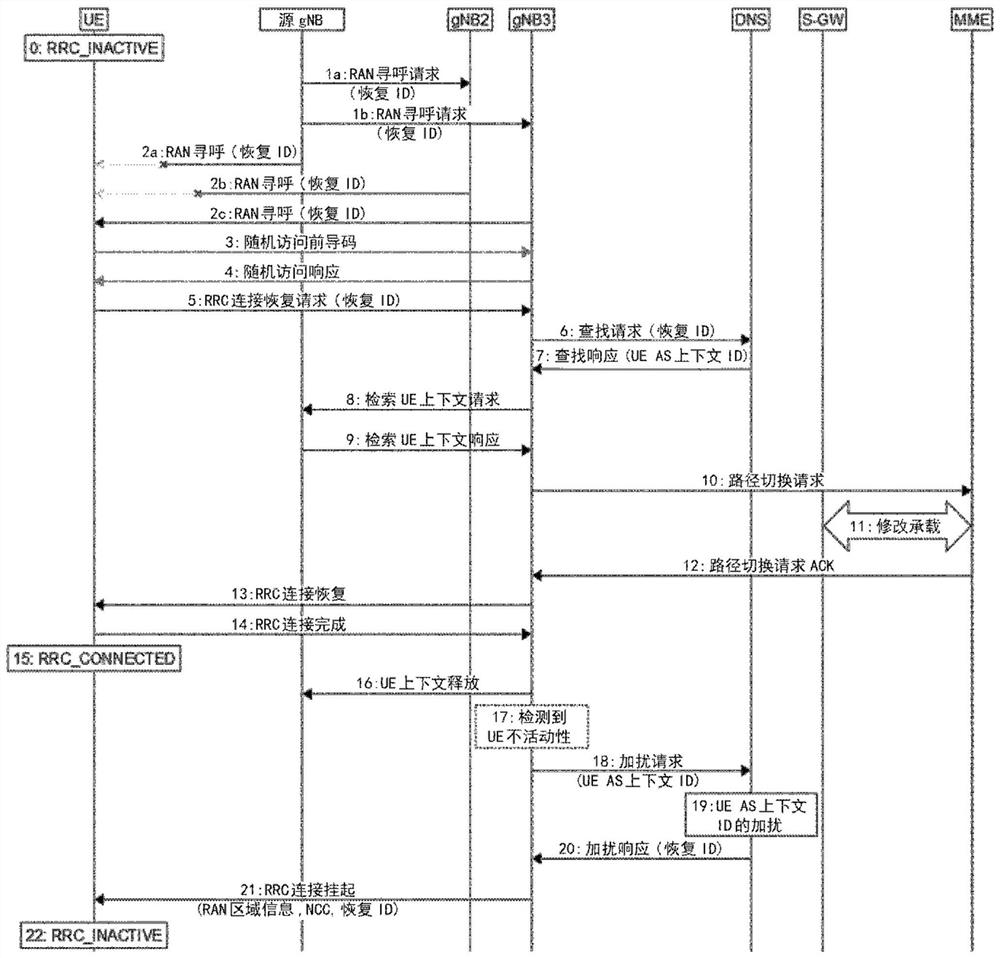
[0089] figure 2 The communication network 100 is shown during a paging process. When the RAN needs to reach UE 120 under RRC_INACTIVE, the node gNBi (one of gNB1 to gNB4) with CN / RAN connection for UE 120 initiates RAN paging in RAN area 130 . The cell associated with the source gNB is directly ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com