Process protection method and system and data processing method
A process and memory data technology, applied in the computer field, can solve problems such as the inability to guarantee the trusted state of dynamic processes, and achieve the effect of ensuring static integrity and ensuring trusted state.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] According to an embodiment of the present invention, an embodiment of a process protection method is also provided. It should be noted that the steps shown in the flow charts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
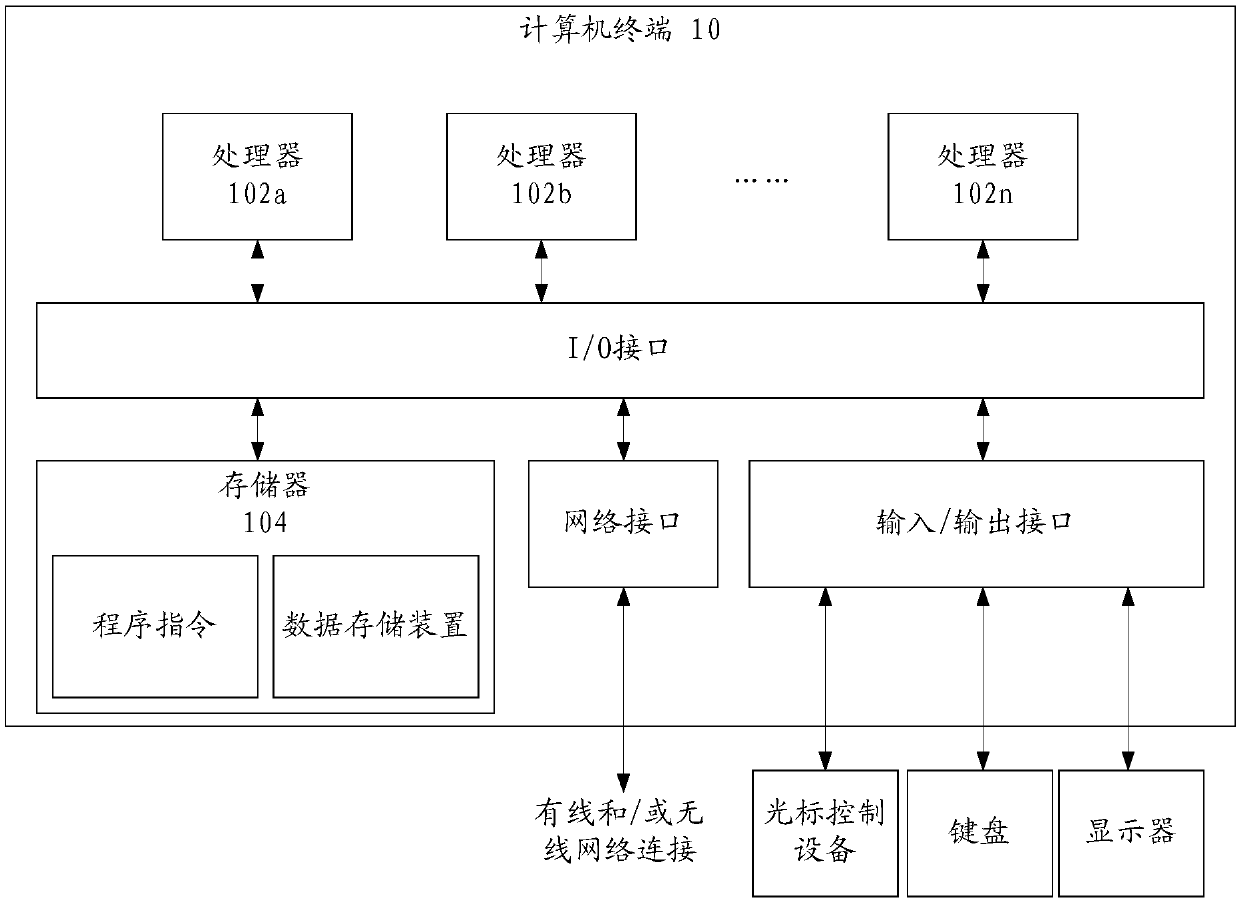
[0047] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Figure 1c A block diagram of a hardware structure of a computer terminal (or mobile device) for implementing a process protection method is shown. Such as Figure 1c As shown, the computer terminal 10 (or mobile device 10) may include one or more (shown by 102a, 102b, ..., 102n in the figure) processor 102 (the processor 102 may include ...
Embodiment 2
[0197] According to an embodiment of the present invention, a process protection method is also provided, Figure 7 It is a flow chart of a process protection method according to Embodiment 2 of the present application, combined with Figure 7 As shown, the method includes:
[0198] Step S71, if it is detected that the process needs to be started again, the initial credible measurement information of the process in the process of starting for the first time is acquired.
[0199] Specifically, the above process is the process to be protected, which may be the process of the application running on the device, and the steps in this embodiment can be executed by the TPM security chip in the device running the process.
[0200] The above starting process for the first time refers to starting the process on a device for the first time. For example, taking the process of an application as an example, if the application is started for the first time after being installed on the devi...
Embodiment 3
[0224] According to an embodiment of the present invention, there is also provided a process protection device for implementing the process protection method in Embodiment 1 above, Figure 8 It is a schematic diagram of a process protection device according to Embodiment 3 of the present application, such as Figure 8 As shown, the device 800 includes:
[0225] The first determining module 802 is configured to determine the initial credibility metric information of the process during the process of starting the process for the first time.
[0226] The first checking module 804 is configured to, if it is detected that the process needs to be started again, perform a credibility check on the starting of the process based on the initial credibility measurement information of the process.
[0227] The second determining module 806 is configured to determine that the process is allowed to start again if the verification is passed.
[0228] It should be noted here that the above-m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com