Application exception analysis method and generation method
A technology of application programs and analysis methods, applied in special data processing applications, hardware monitoring, instruments, etc., to achieve the effect of improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
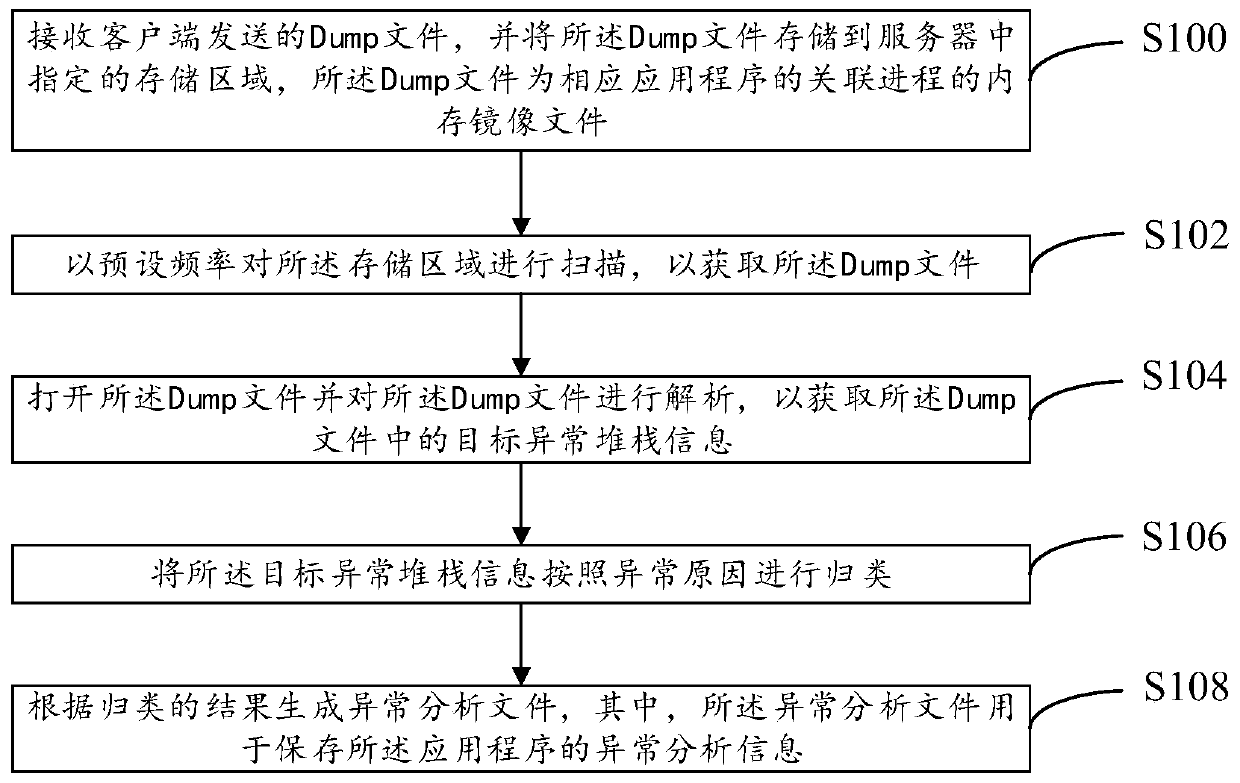
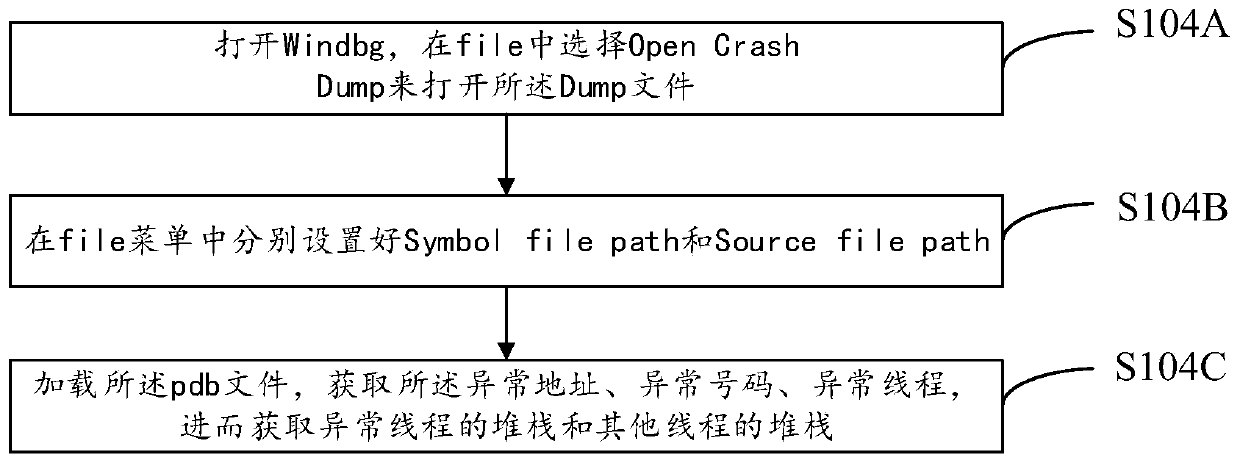
[0055] refer to figure 1 , shows a flow chart of the steps of the method for analyzing the application anomaly in Embodiment 1 of the present invention. It can be understood that the flowchart in this method embodiment is not used to limit the sequence of execution steps. details as follows:
[0056] Step S100, receiving the Dump file sent by the client, and storing the Dump file in a specified storage area in the server, the Dump file being a memory image file of an associated process of the corresponding application program.
[0057] Exemplarily, the received Dump file is written into the server through the http protocol.
[0058] The Dump file is a memory image file of the associated process of the corresponding application program, which is used to save the execution state of the target program during running, such as the memory, stack, handle, thread and other program running related information associated with the target program.
[0059] Step S102, scanning the stora...
Embodiment 2
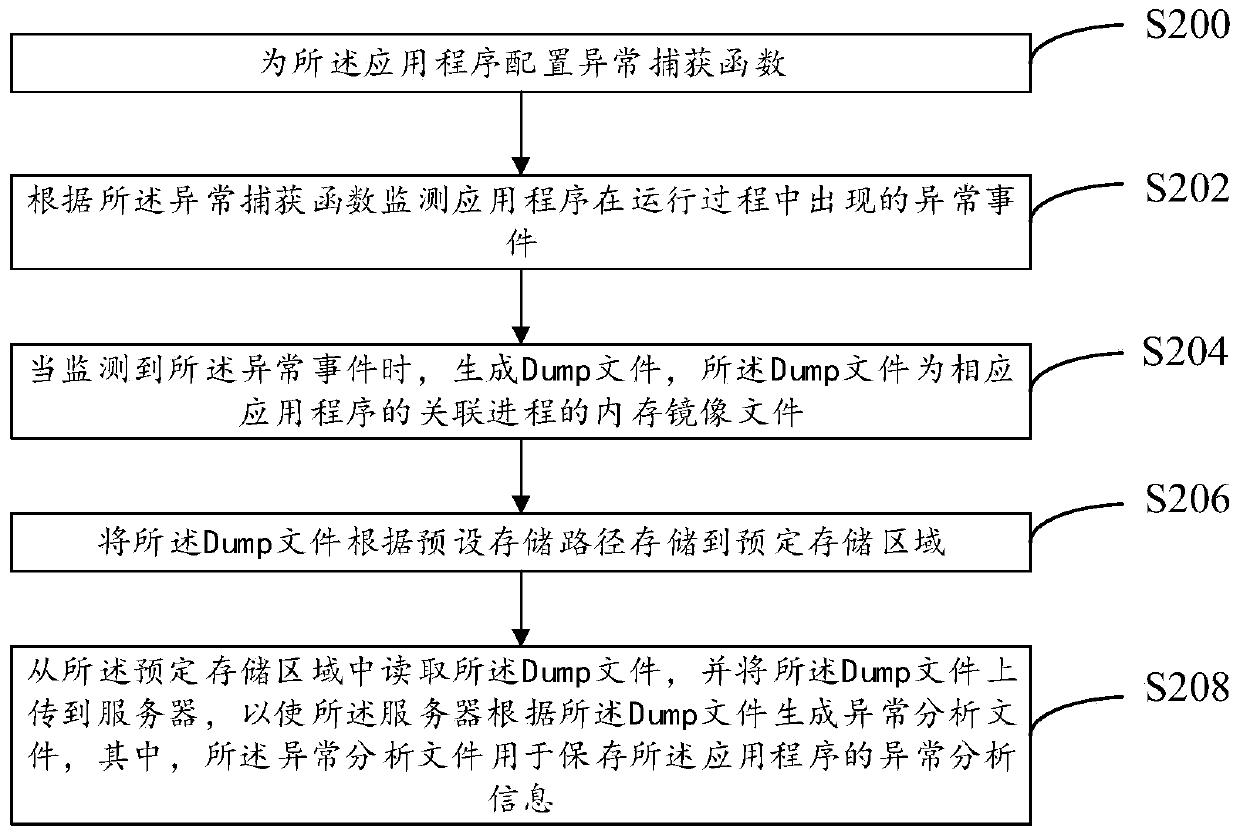
[0087] refer to image 3 , shows a flow chart of the steps of the method for generating an application exception according to Embodiment 2 of the present invention. It can be understood that the flowchart in this method embodiment is not used to limit the sequence of execution steps. details as follows:
[0088] Step S200, configuring an exception catching function for the application.
[0089] Optionally, the SetUnhandledExceptionFilter() function is set at the start position of the application program, so that the SetUnhandledExceptionFilter() function acts on the running life cycle of the application program.
[0090] Step S202 , monitoring abnormal events that occur during the running of the application program according to the exception catching function.
[0091] Exemplarily, when the target program encounters an unhandled exception and causes a program exception, the exception is handed over to the function for processing.
[0092] Step S204, when the abnormal event...
Embodiment 3
[0101] read on Figure 4 , shows a schematic diagram of program modules of Embodiment 3 of the application anomaly analysis system 20 of the present invention. In this embodiment, the application-based anomaly analysis system 20 may include or be divided into one or more program modules, one or more program modules are stored in a storage medium and executed by one or more processors, In order to complete the present invention, and realize the above-mentioned application anomaly analysis system method. The program module referred to in the embodiment of the present invention refers to a series of computer program instruction segments capable of completing specific functions, which is more suitable than the program itself to describe the execution process of the application anomaly analysis system 20 in the storage medium. The following description will specifically introduce the functions of each program module of the present embodiment:
[0102] The receiving module 300 is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com