Network data security method, device and storage medium for wearable devices
A wearable device and network data technology, applied in the field of network information security, can solve problems such as lack of detection actions, wearable device security cannot be guaranteed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the purpose, technical solution and advantages of the present application clearer, the implementation manners of the present application will be further described in detail below in conjunction with the accompanying drawings.
[0040] First, a brief introduction to the nouns involved in the embodiments of this application:
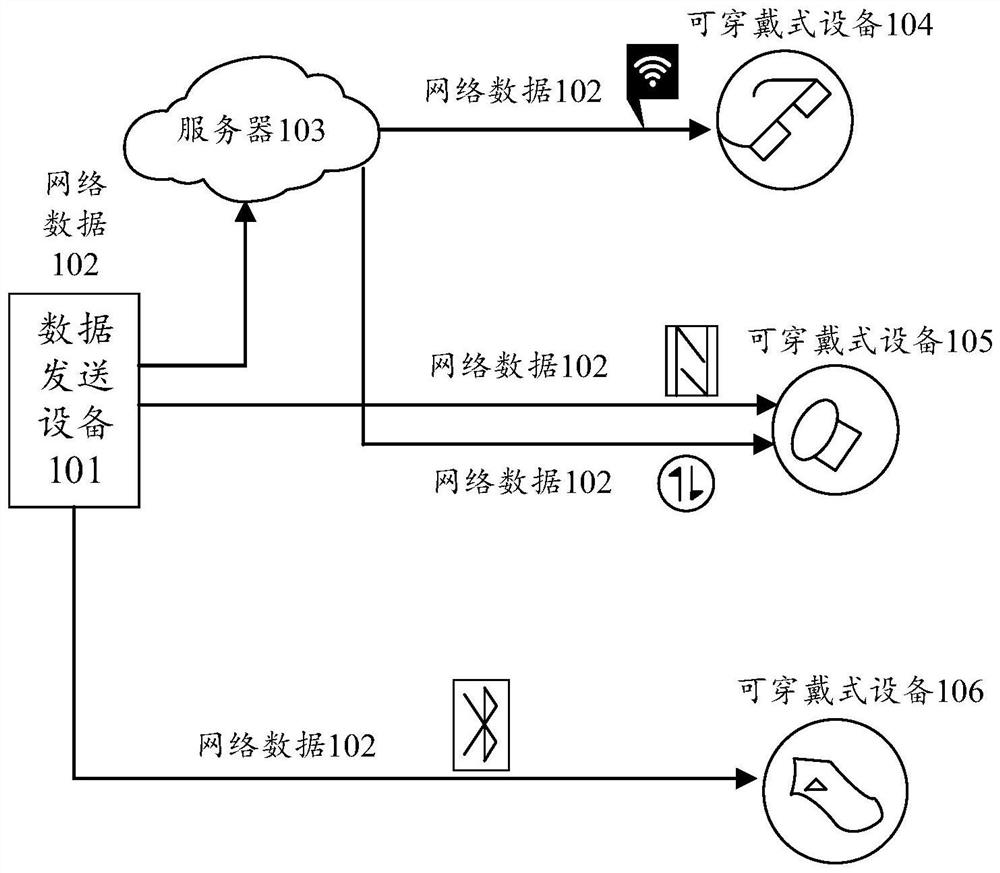
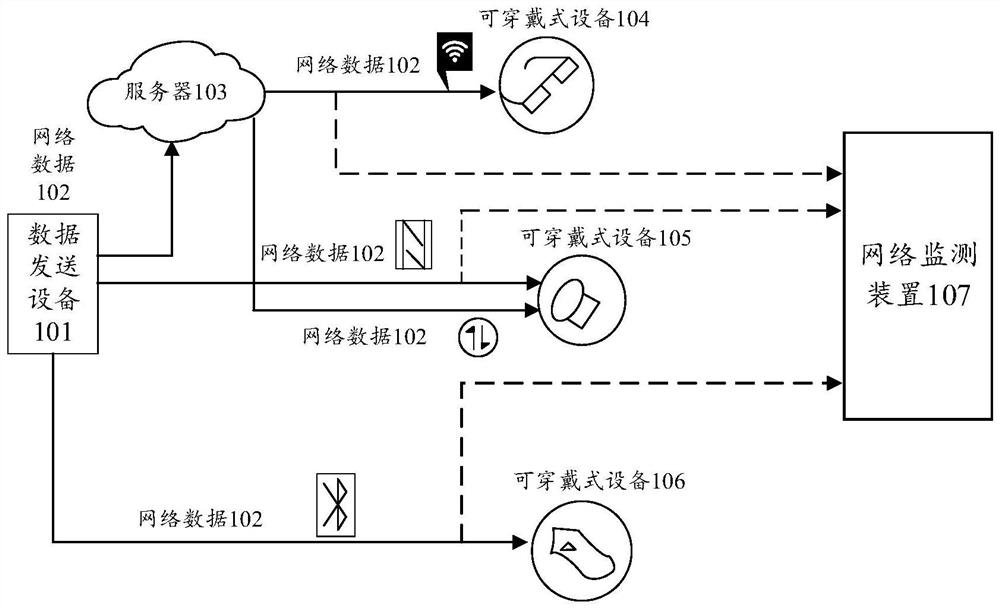
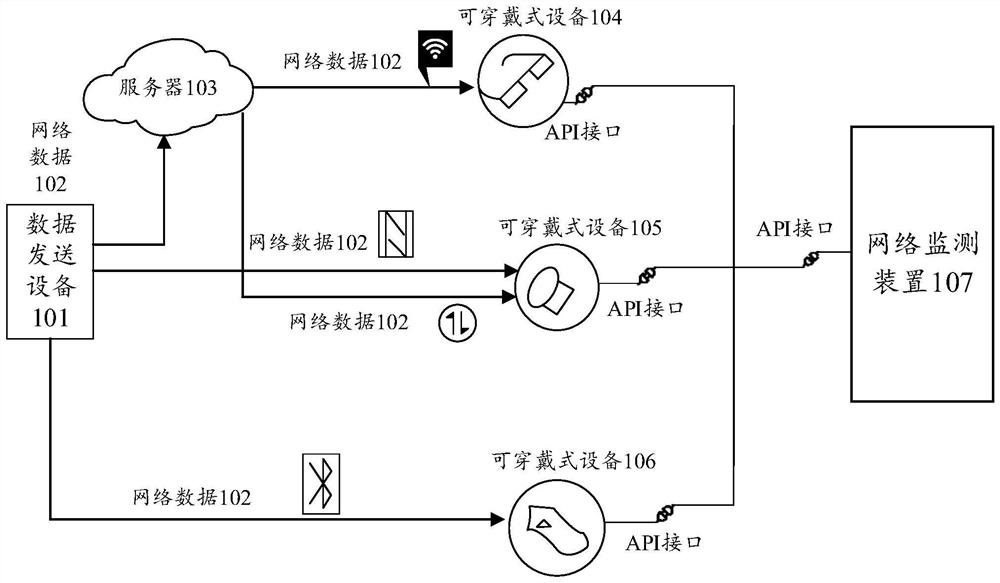
[0041] Wearable device: refers to a portable device that is directly worn on the body, or integrated into the user's clothes, or other wearable accessories. A wearable device is not only a hardware device, but also can realize the function of data transmission through software support, data interaction, and cloud interaction. The mainstream product forms of wearable devices include: Watches supported by the wrist (including watches and wristbands, etc.), Shoes supported by the feet (including shoes, socks and other products worn on the legs), and Glass (including glasses, helmets, and headbands) supported by the head, as well as no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com