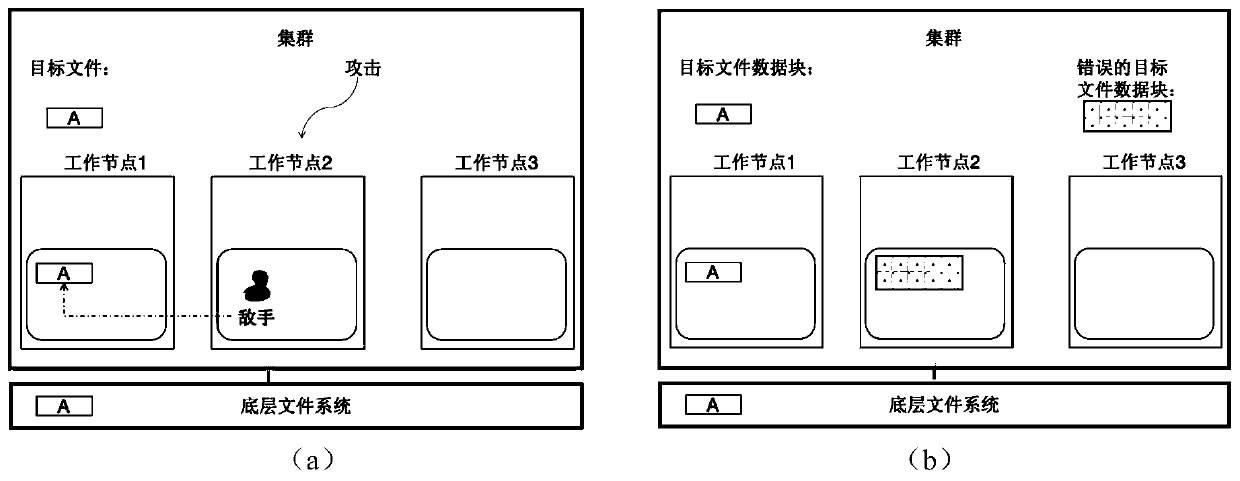
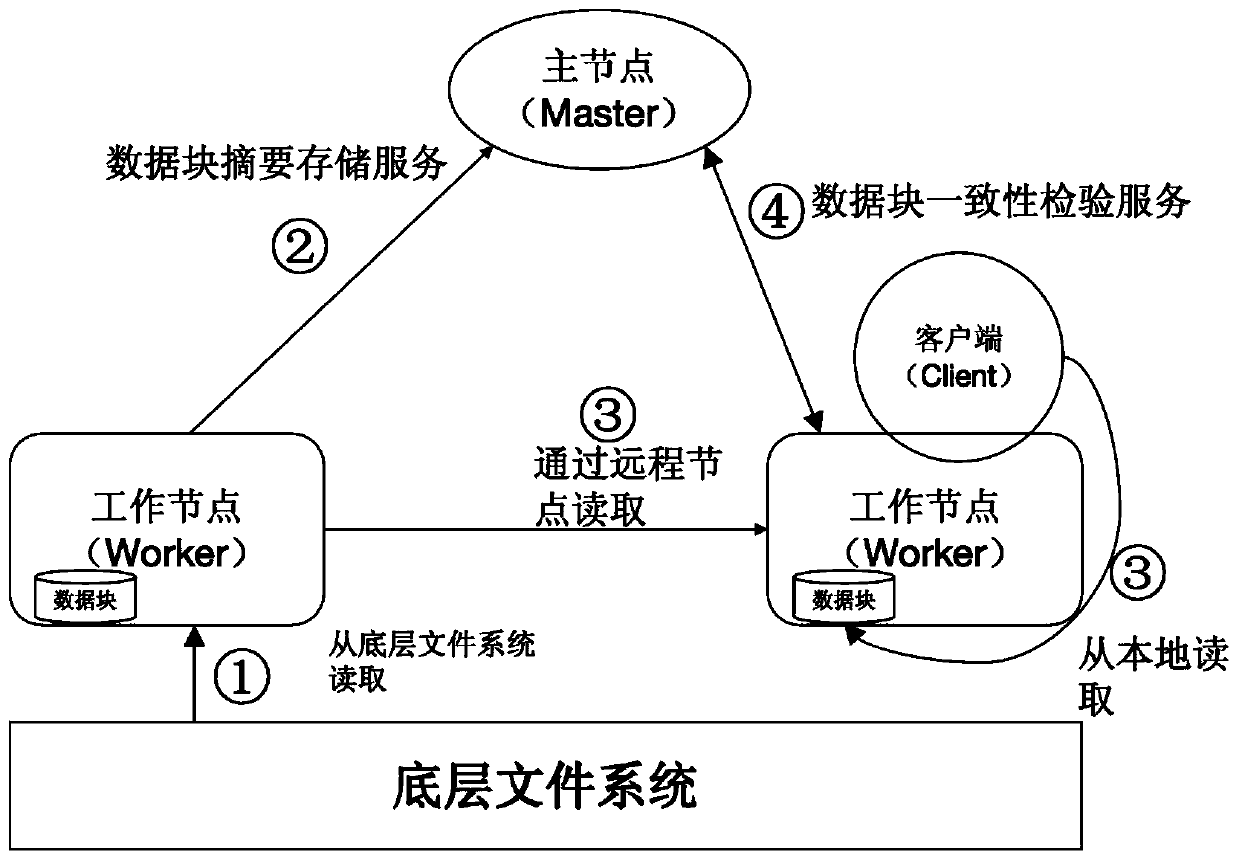
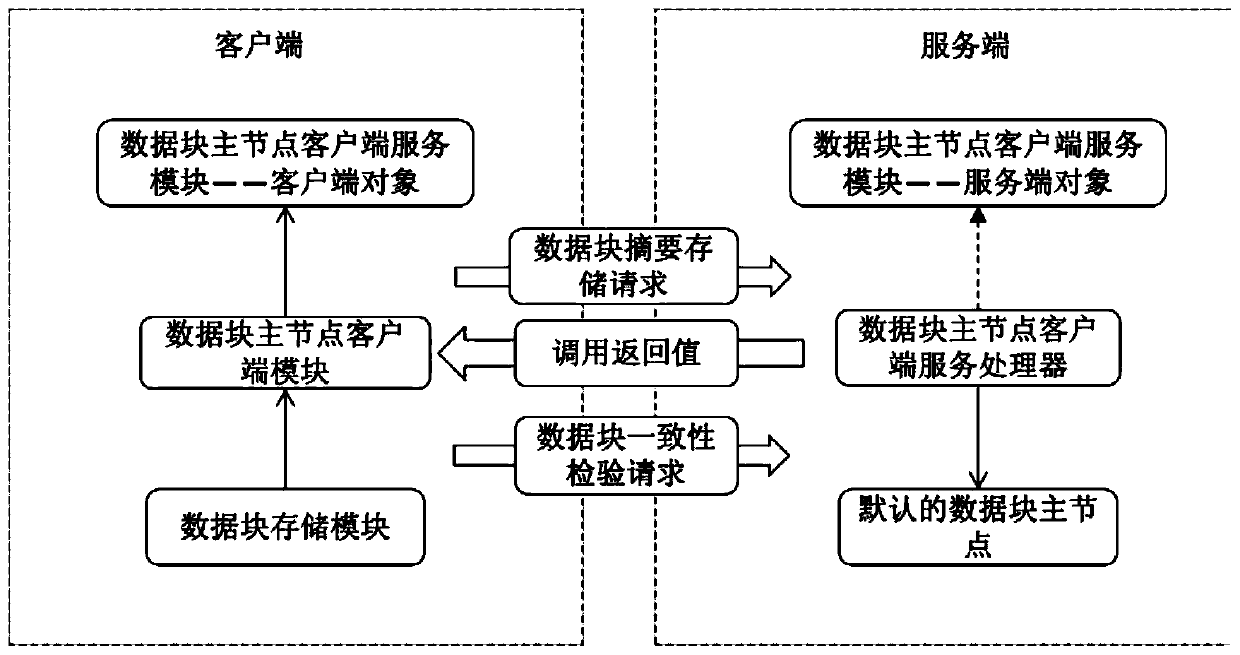
Memory data block integrity checking method
A technology for integrity inspection and memory data, which is applied in the field of integrity inspection of memory data blocks, can solve the problems of reduced accuracy rate and recognition accuracy rate, and achieve the effect of taking into account performance requirements and protecting against security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention not only improves the security of the Alluxio platform, but also has little impact on performance.
[0061] The cluster in this part of the experiment contains 11 nodes, including a master node Master and 10 slave nodes Worker, where Worker1 to Worker5 are deployed on the same rack, Worker6 to Worker10 are deployed on the same rack, and each node is installed with 64-bit Ubuntu 16.04 operation The system is physically configured with an Inter Core i7 processor with a main frequency of 3.4GHz, 8GB of physical memory and 256GB of hard disk storage. The version of Spark is 2.2.0 as the upper-level computing framework, the version of HDFS as the underlying file system is 2.8.1, and the JDK is Oracle-JDK8u121. The experimental clusters are in the same LAN environment. Deploy the native Alluxio system and SE-Alluxio on the cluster as an experimental comparison. Each Alluxio Worker is configured with 2GB memory storage and 10GB hard disk storage. The n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com