Virtualization protection method in cloud environment, and terminal
A cloud environment and virtualization technology, applied in the field of virtual machine security, can solve problems such as attacks, inability to meet security protection requirements, and inability to guarantee virtual machine security, and achieve the effect of centralized management and control, improving security, and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
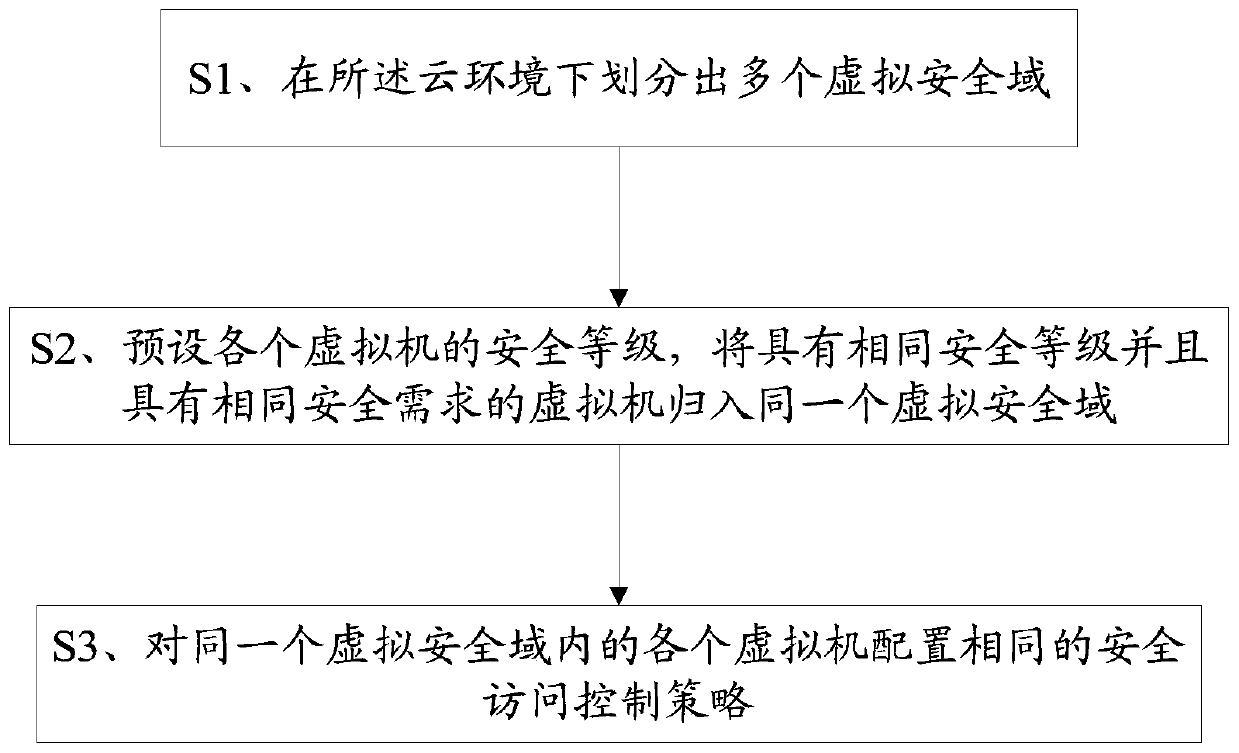
[0062] Please refer to figure 1 , a virtualization protection method in a cloud environment, comprising the steps of:
[0063] S1. Dividing multiple virtual security domains under the cloud environment;
[0064] S2. Preset the security level of each virtual machine, and classify the virtual machines with the same security level and the same security requirements into the same virtual security domain;
[0065] S3. Configure the same security access control policy for each virtual machine in the same virtual security domain;
[0066] S4. Receive a resource access request sent by the client, where the resource access request includes the virtual machine where the resource is located and the corresponding virtual security domain;
[0067] S5. Determine whether the virtual machine in the resource access request is in the corresponding virtual security domain, and whether the resource to be accessed by the client is saved in the corresponding virtual security domain, and if so, se...
Embodiment 2
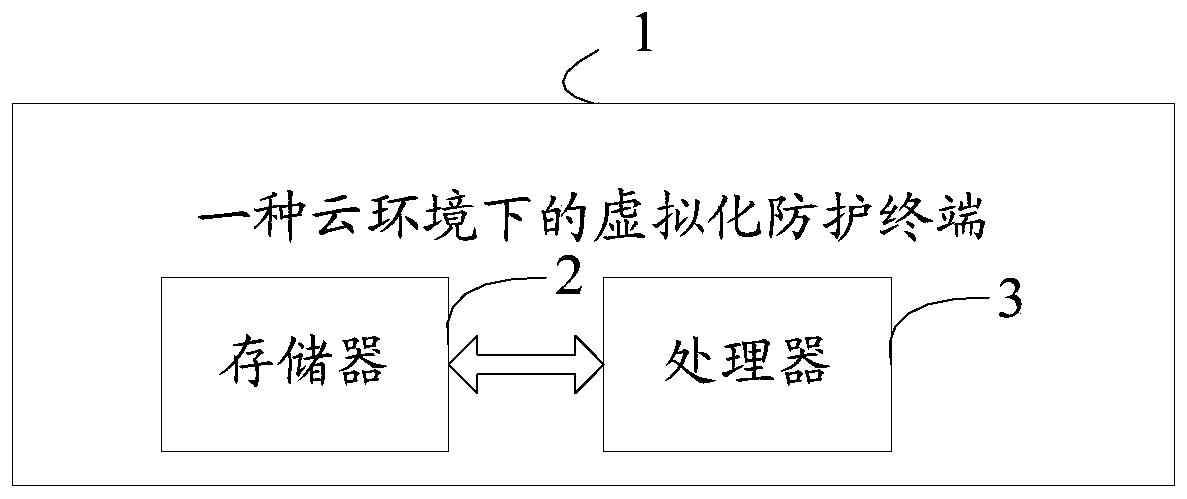
[0084] Please refer to figure 2 , a virtualization protection terminal 1 in a cloud environment, comprising a memory 2, a processor 3, and a computer program stored in the memory 2 and operable on the processor 3, and the processor 3 executes the Each step in the first embodiment is implemented as a computer program.
[0085] To sum up, the virtualization protection method and terminal in the cloud environment provided by the present invention divide multiple virtual security domains in the cloud environment, and classify virtual machines with the same security level and the same security requirements into the same domain. A virtual security domain, configure the same security access control policy for each virtual machine in the same virtual security domain, and perform real-time detection of the virtual security domain where the virtual machine is located through virtual machines, virtual firewalls and virtual network objects, When abnormal access is detected, it will be n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com