Message expansion circuit in low-power-consumption SHA256 algorithm
An extended circuit and low power consumption technology, applied in logic circuits with logic functions, electrical components, encryption devices with shift registers/memory, etc., to achieve the effects of saving power consumption, saving energy costs, and extending battery life
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to clearly illustrate the technical features of the solution, the solution will be described below through specific implementation modes.
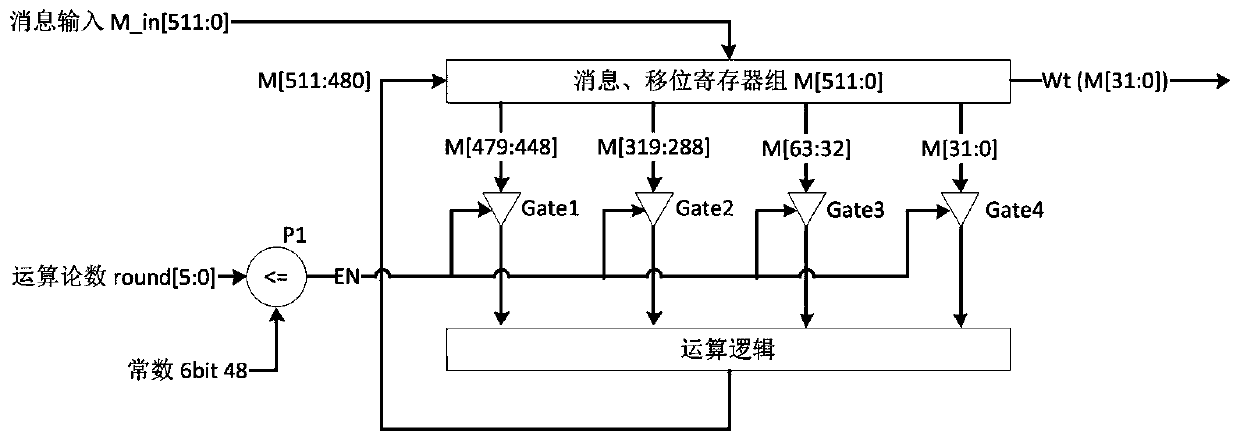
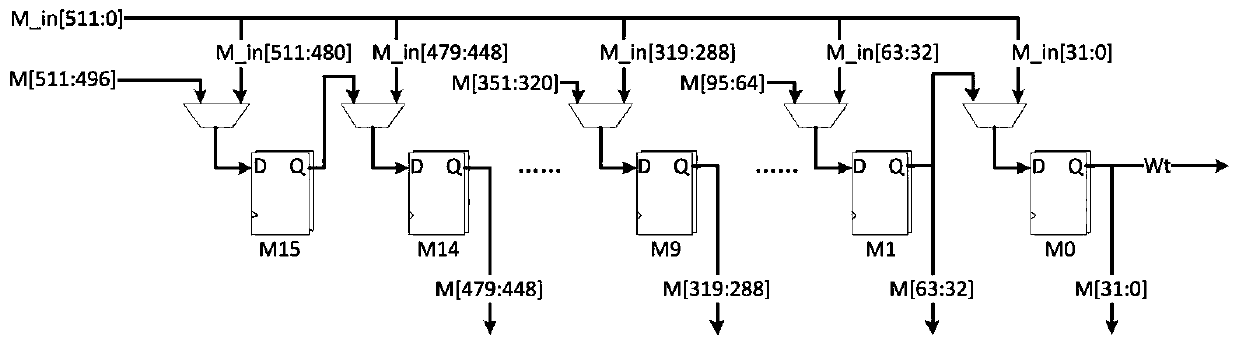
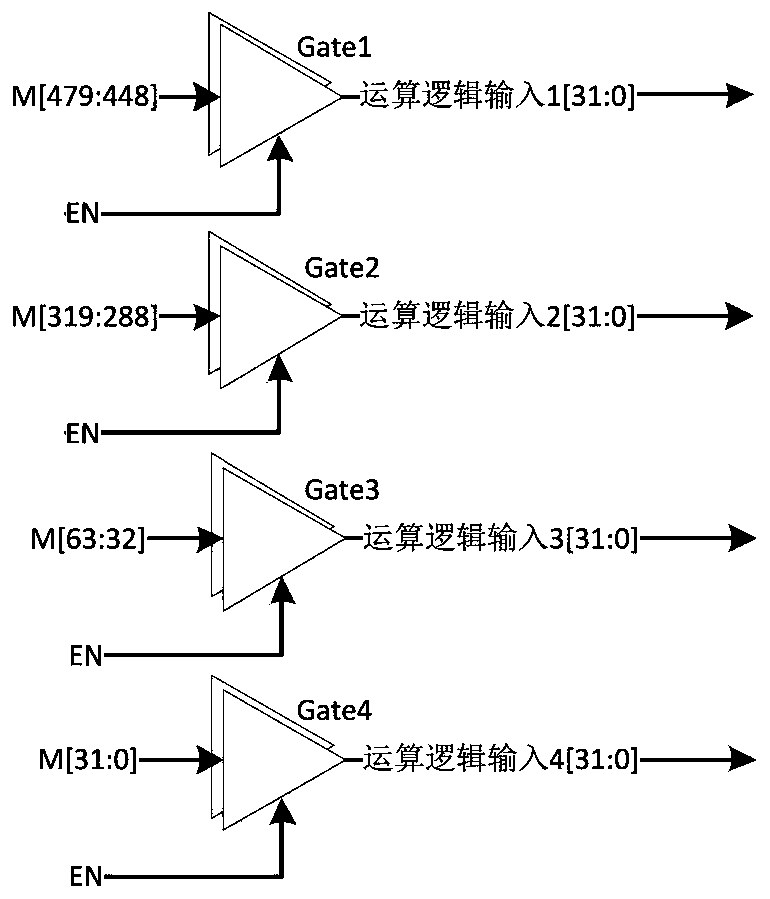
[0025] see Figure 1 to Figure 4 , the present invention is: a message extension circuit in a low-power SHA256 algorithm, wherein the message extension circuit includes a group of 512bit message and shift multiplexing register M, four groups of tri-state gates Gate1, Gate2, Gate3 and Gate4 consists of a set of arithmetic logic circuits and a set of 6-bit comparators P1.
[0026] Specifically, the specific content of the group of 512-bit message and shift multiplexing register M is: when a new message needs to be input, the value of M comes from the message input M_in; in the 64 rounds of operations of the SHA256 algorithm, each round of operations The message register M moves 32 bits to the right, the highest 32 bits, namely M[511:480] are from the output of the operation logic, and the lowest 32 bits, namely M[31:0] are t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com