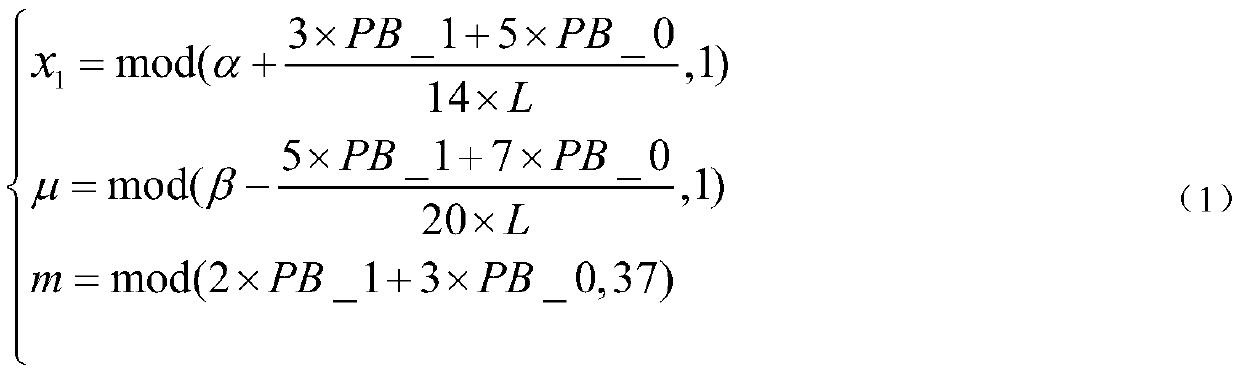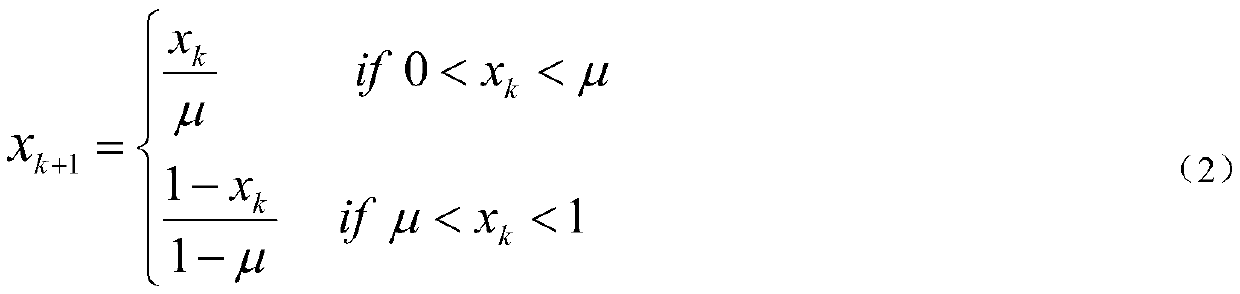Encryption and decryption method for Chinese and English character strings
An encryption method and string technology, applied in the field of information security, can solve the problems of poor readability and reproducibility of ciphertext, difficult to write or identify, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
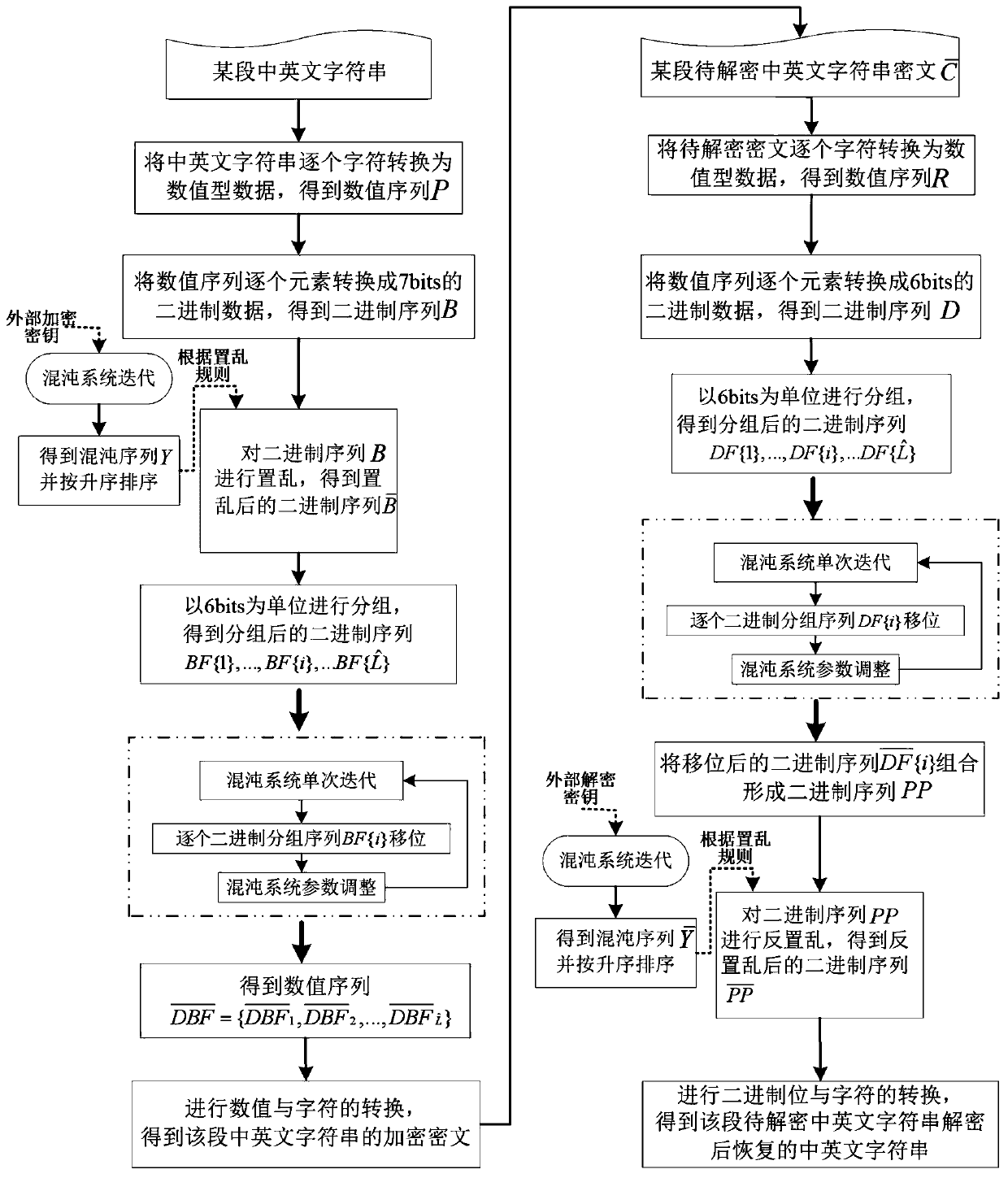
[0139] According to the encryption method of a kind of Chinese and English character string in the above-mentioned specific embodiment, the steps are as follows:
[0140] (1) With a certain section of Chinese and English character strings "encryption method and decryption method of a character, 1+1>2?" Character by character according to the encryption method steps (1) of a kind of Chinese and English character strings in the above-mentioned specific embodiment ) shown in the character and numerical conversion operation, it is converted into numerical data, and the numerical sequence P={82,59,86,86,87,86,55,123,53,68,60,83,67,92 is obtained ,55,61,55,40,58,77,61,98,67,92,55,61,55,40,35,44,0,49,0,43,0,49,0,62,0 ,50,66,112,35,63} and then convert the numerical sequence P into 7bit binary data element by element, and obtain the binary sequence B={1,0,1,0,0,1,0,0,1,1,1 ,0,1,1,1,0,1,0,1,1,0,1,0,1,0,1,1,0,1,0,1,0,1,1,1,1 ,0,1,0,1,1,0,0,1,1,0,1,1,1,1,1,1,1,0,1,1,0,1,1,0,1 ,0,1,1,0...
Embodiment 2
[0152] According to the above-mentioned encryption method of a Chinese and English character string, a Chinese and English character string to be encrypted is "a kind of character encryption method and decryption method, 1+1>2?", and its encryption steps are similar to the specific embodiment 1 , only the encryption key changes slightly: α=0.12345000000001, or β=0.54321000000001, the results of the encryption of Chinese and English strings are shown in Table 1. It can be seen from Table 1 that slight changes in the encryption key will cause great changes in the encrypted ciphertext of the Chinese and English strings. It can be seen that the encryption method for the Chinese and English strings proposed in this patent is sensitive to the encryption key.
[0153] Table 1 Encryption results of Chinese and English strings when the external encryption key changes slightly
[0154]
[0155]
Embodiment 3
[0157] According to the above-mentioned encryption method of a Chinese and English character string, its encryption steps are similar to the specific embodiment 1, only a certain section of Chinese and English character strings to be encrypted ("A kind of character encryption method and decryption method, 1+1>2? ") slight changes: "encryption method and decryption method of two characters, 1+1>2?"; or "encryption method and decryption method of a character, 1+1>2?"; or " A character encryption method and decryption method, 1+1>2?"; or "A character encryption method and decryption method, 1+1>2?"; or "A character encryption method and Decryption method, 1+12."; or "A character encryption method and decryption method, 1+1> 2?", the encryption results of Chinese and English strings are shown in Table 2. It can be seen from Table 2 that slight changes in the plaintext information of the Chinese and English strings to be encrypted will cause the encrypted ciphertext to be "unrecog...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com