A data security protection method and related equipment
A data security and data technology, applied in the field of communication, can solve problems such as leakage, achieve the effect of improving security and solving online play
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0101] The terms used in the embodiments of the present invention are only used to explain specific examples of the present invention, and are not intended to limit the present invention.
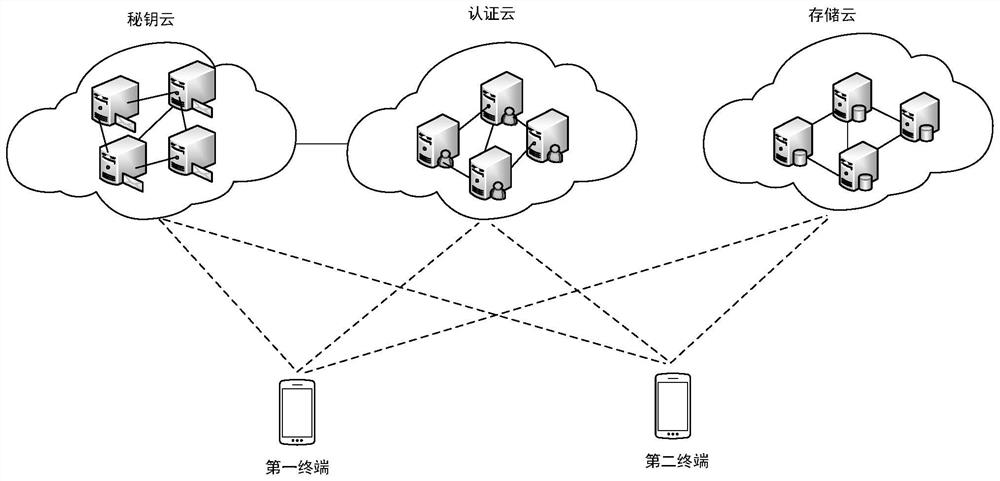
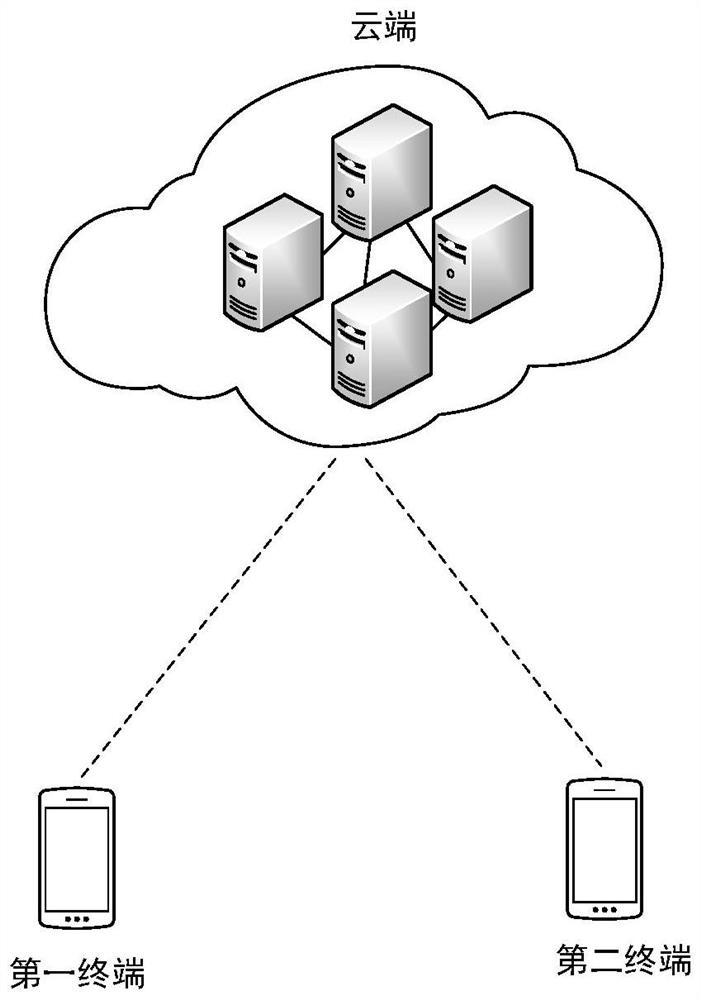
[0102] The following describes a process in which a user backs up and downloads personal data in the cloud through a terminal in a conventional solution.
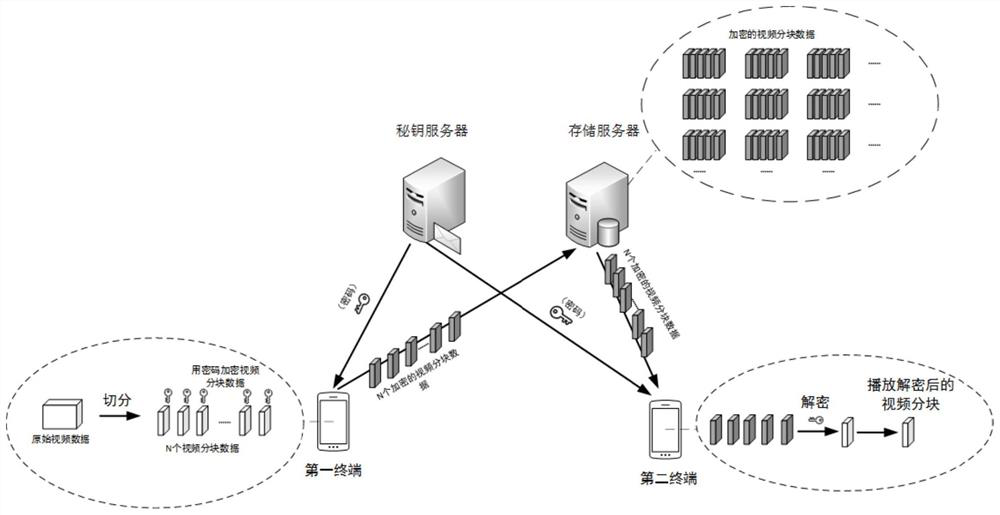
[0103] The terminal encrypts the user's personal data according to the user's private key, and then the terminal uploads the encrypted user's personal data to the storage server for backup. There is no user's private key in the storage server, so the encrypted personal data of the user cannot be accessed. Manufacturers that provide decryption services deploy independent decryption servers, which are responsible for obtaining keys from user terminals and storing them in the keystore. When the user needs to download the user's personal data that has been backed up in the cloud, the decryption server is responsible for obtaining the user's...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com