Voice attack detection method and device and network equipment
A technology for voice detection and network equipment, applied in the field of Internet of Things security, can solve the problems of not being able to detect whether the voice signal is a specific user, and home equipment being vulnerable to attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The following will clearly and completely describe the technical solutions in the embodiments of the present application in conjunction with the drawings in the embodiments of the present application. Obviously, the described embodiments are only a part of the embodiments of the present application, not all of the embodiments. Based on the embodiments of the present application, all other embodiments obtained by those of ordinary skill in the art without creative work shall fall within the protection scope of the present application.
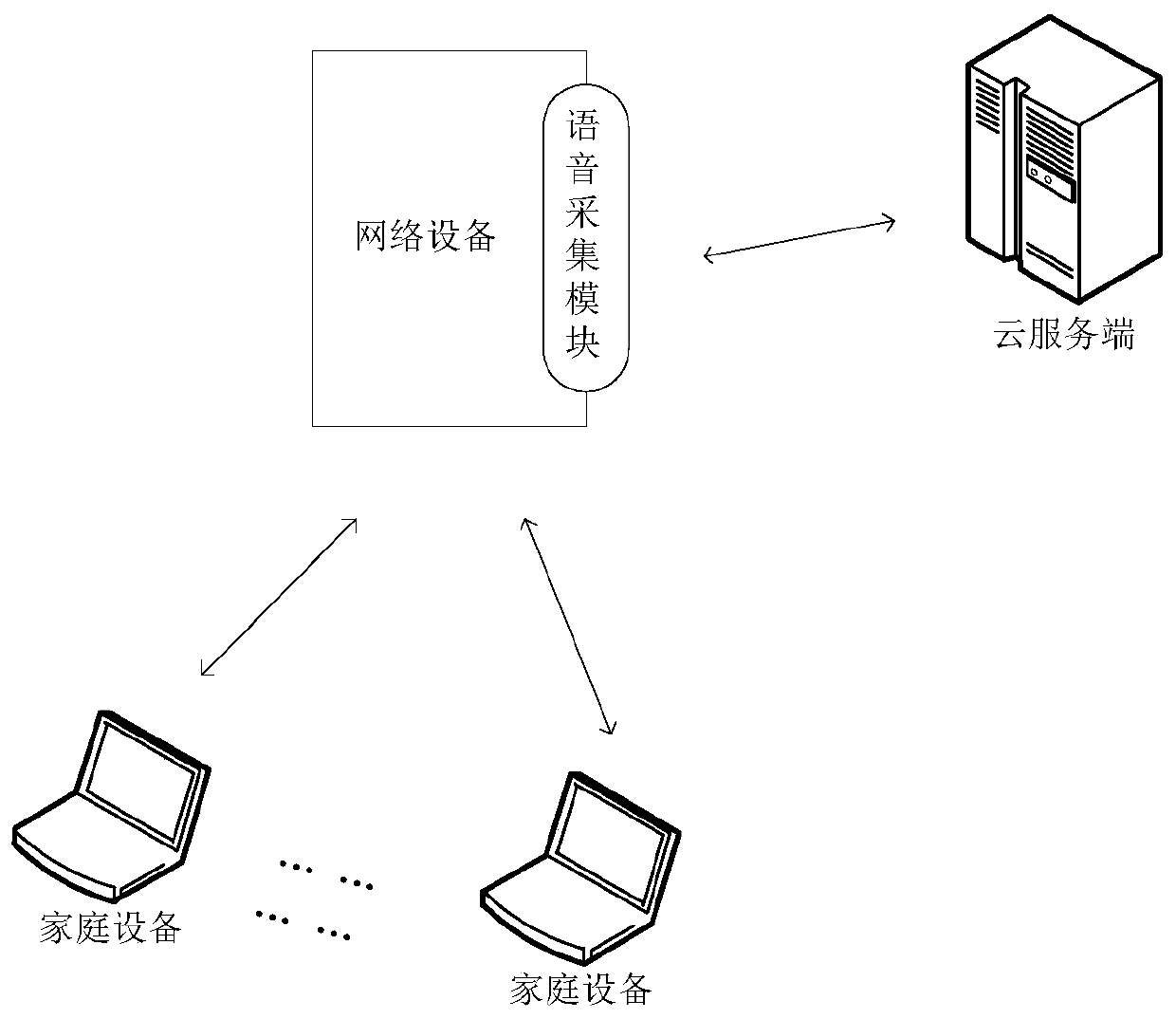
[0048] The voice recognition attack detection method provided by the embodiment of the present invention can be applied to figure 1 In the system architecture described, the system may include at least one home device, network device, and cloud server.
[0049] At least one home device may establish a communication connection with the network device in a wired or wireless manner, and the network device may also establish a communication connect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com