Password protection method, password verification method and system
A password protection and password verification technology, applied in the field of information security, can solve problems such as brute force cracking and dictionary attacks that cannot be prevented, and achieve the effect of strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Various embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
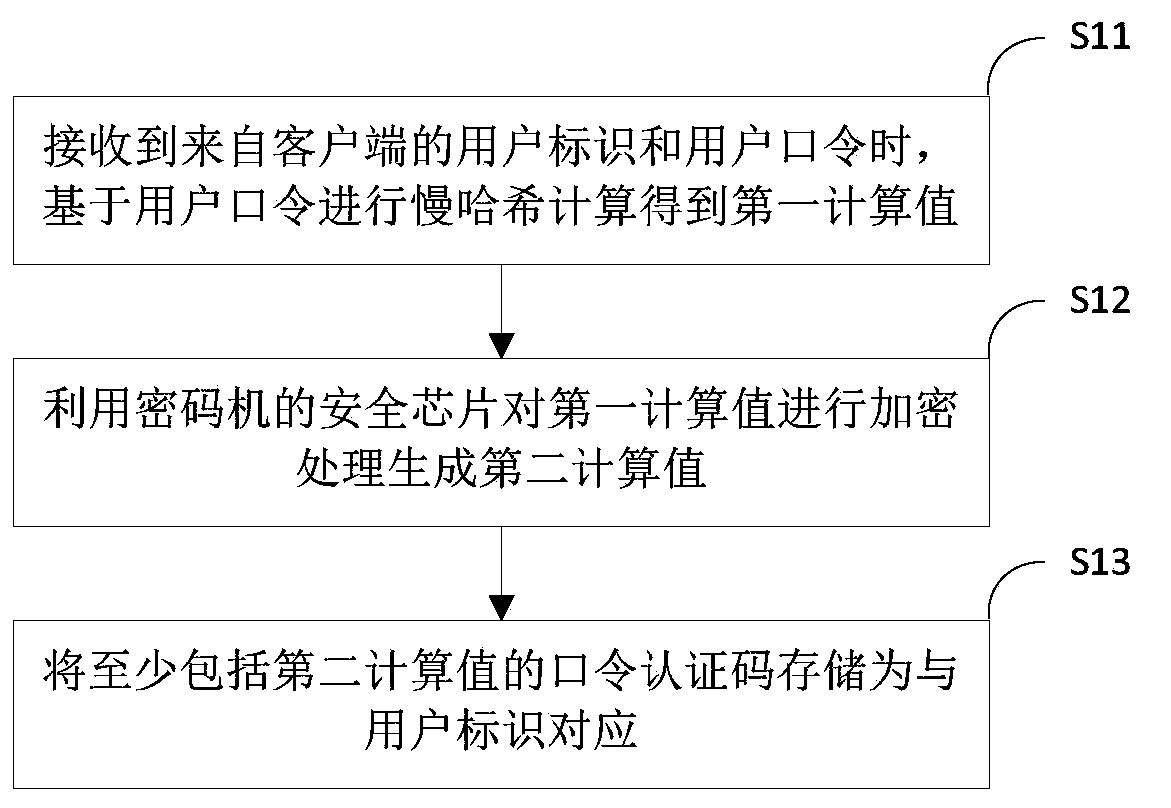
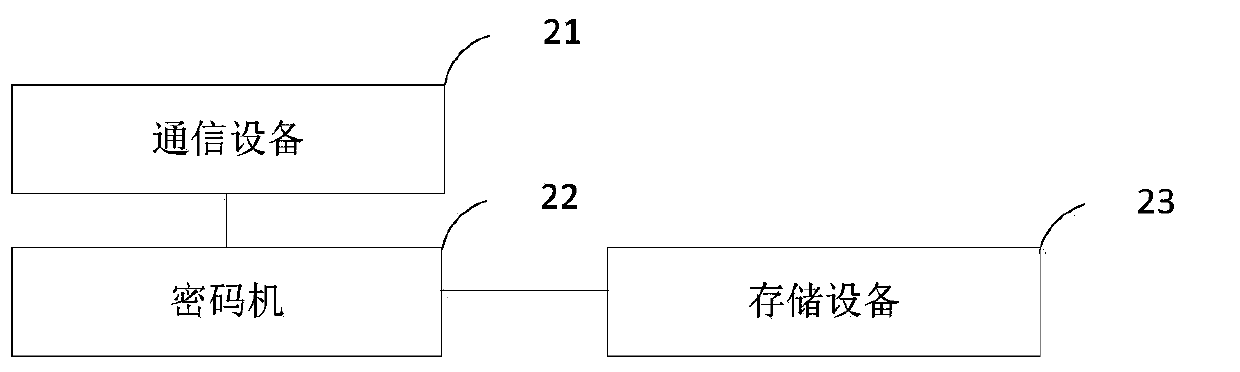
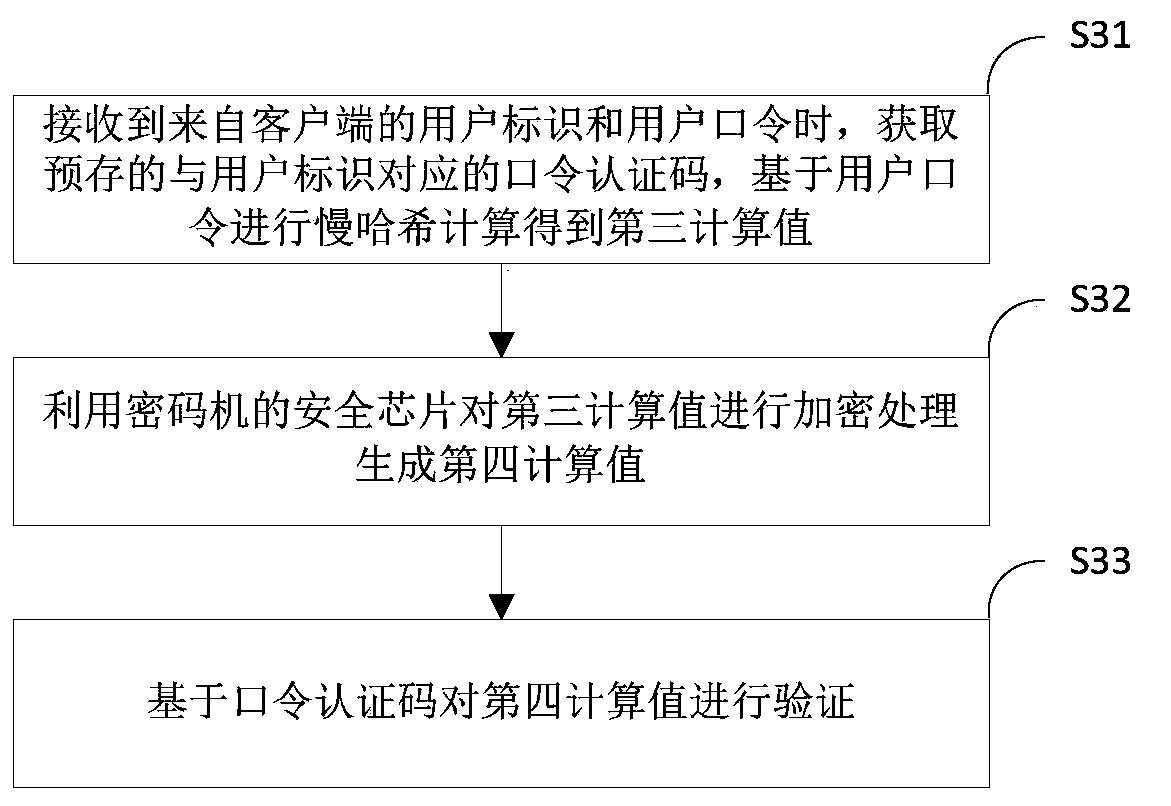
[0022] figure 1 It is an exemplary flowchart of a password protection method according to an embodiment of the present invention. The password protection method in the embodiment of the present invention is applied to the server.
[0023] Such as figure 1 As shown, the password protection method of the embodiment of the present invention includes:
[0024] S11. When receiving the user ID and the user password from the client, perform slow hash calculation based on the user password to obtain the first calculated value;
[0025] In the embodiment of the present invention, when the user needs to submit the user password to the server for verification, for example, the user needs to perform user registration on the application program or application website, or the user needs to set a separate verification for a specific network application servi...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap