An anti-cracking verification code generation method
A verification code and anti-cracking technology, applied in the field of anti-cracking verification code generation, can solve the problems of loss of verification code, reducing the difficulty of cracking the verification code in pictures, and discounting the defense effect of verification code, so as to increase security and increase automatic identification. Difficulty, the effect of increasing the difficulty of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
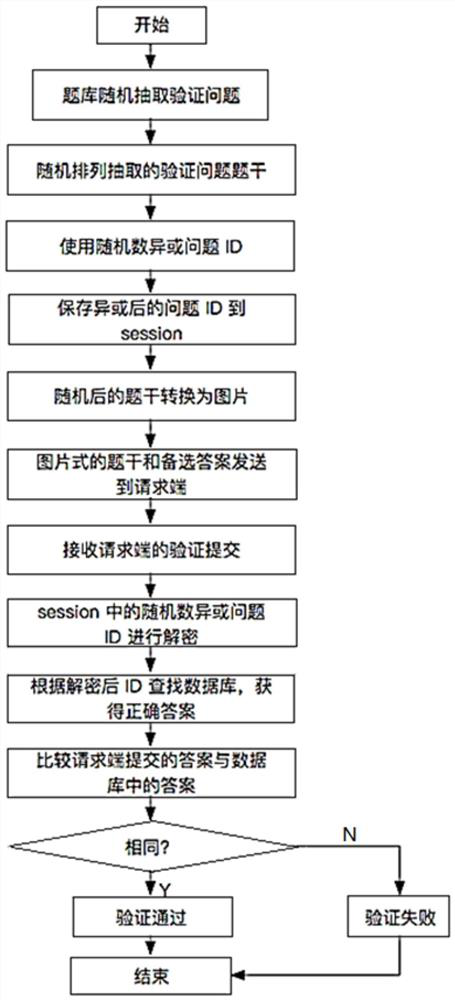
[0027] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments. The core idea of the present invention is to process the verification code questions out of order, and encrypt the verification code question number (ID), so that the computer cannot directly identify it, and must rely on human subjective knowledge and understanding, so as to prevent the verification code from being cracked. .
[0028] The flow chart of the verification code generation method in this embodiment is as follows figure 1 As shown, the specific steps are as follows:
[0029] Step 1: Create a verification code question bank; the questions should be open-ended as much as possible, and there is no unique standard answer.
[0030] For example, if the question is "Which value is your height closest to?", the alternative answers are "0.1", "10", "170", "1000000", and the exact answer is "170".
[0031] Step 2: Make pictures o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com